== CODE IMPLEMENTATION ==
AWS Command Line Interface (CLI) & Software Developer Kit (SDK)
- both protected by access keys, generated from AWS Management Console
- CLI can direct access to public APIs of AWS resources
- to use MFA with CLI, which means a temporary session
- run the STS GetSessionToken API call
aws sts get-session-token --serial-number arn-of-the-mfa-device --token-code code-from-token --duration-seconds 3600
- run the STS GetSessionToken API call
- CLI Credentials Provider Chain
- Command line options – –region, –output, and –profile
- Environment variables – AWS_ACCESS_KEY_ID,AWS_SECRET_ACCESS_KEY, and AWS_SESSION_TOKEN
- CLI credentials file – aws configure ~/.aws/credentials
- CLI configuration file – aws configure ~/.aws/config
- Container credentials – for ECS tasks
- Instance profile credentials – for EC2 Instance Profiles
- SDK is set of libraries for programming, as language-specific APIs
- the AWS CLI uses the Python SDK (boto3)
- “us-east-1” would be chosen by default, if no region specified
- SDK Credential Provider Chain
- Java system properties – aws.accessKeyId and aws.secretKey
- Environment variables –
AWS_ACCESS_KEY_ID and AWS_SECRET_ACCESS_KEY - The default credential profiles file – ex at: ~/.aws/credentials, shared by many SDK
- Amazon ECS container credentials – for ECS containers
- Instance profile credentials– used on EC2 instances
- pagination parameters in AWS CLI command could help to solve the Time-Out issue from massive resource item processing
- –page-size
- The CLI still retrieves the entire list, but it makes a greater number of service API calls in the background and retrieves fewer items with each request. This increases the probability that individual calls will succeed in without the use of a timeout.
AWS CloudFormation
- provision infrastructure using a text-based (JSON/YAML) templates (uploaded to S3) that describes exactly what resources are provisioned and their settings.
- manages the template history similar to how code is managed in source control
- Benefits
- Infrastructure as code (IaC)
- Cost
- Each resources within the stack is tagged with an identifier so you can easily see how much a stack costs you
- Productivity
- Ability to destroy and re-create an infrastructure on the cloud on the fly
- Automated generation of Diagram for your templates!
- Declarative programming (no need to figure out ordering and orchestration)
- Separation of concern: create many stacks for many apps, and many layers.
- Delete the stack would also remove each individual artifact
- Components
- AWSTemplateFormatVersion
- Description
- Resources (mandatory) – aws resources
- Parameters – dynamic inputs (AllowedValues/NoEcho) !Ref
- Pseudo Parameters
- AWS::AccountId
- AWS::Region
- AWS::StackId
- AWS::StackName
- AWS::NotificationARNs
- AWS::NoValue (Doesn’t return a value)
- Pseudo Parameters
- Mappings – static variables !FindInMap [ MapName, TopLevelKey, SecondLevelKey ]
- Outputs – reference about what has been created !ImportValue
- declares optional outputs values that we can import into other stacks (if you export them first)!
- Conditions
- (References / Functions) as Helper
- Transformer- used for Serverless services, especially for AWS SAM.
- 2 methods of updating a stack
- direct update – CloudFormation immediately deploys your changes
- change sets – preview your changes first, then decide if you want to deploy
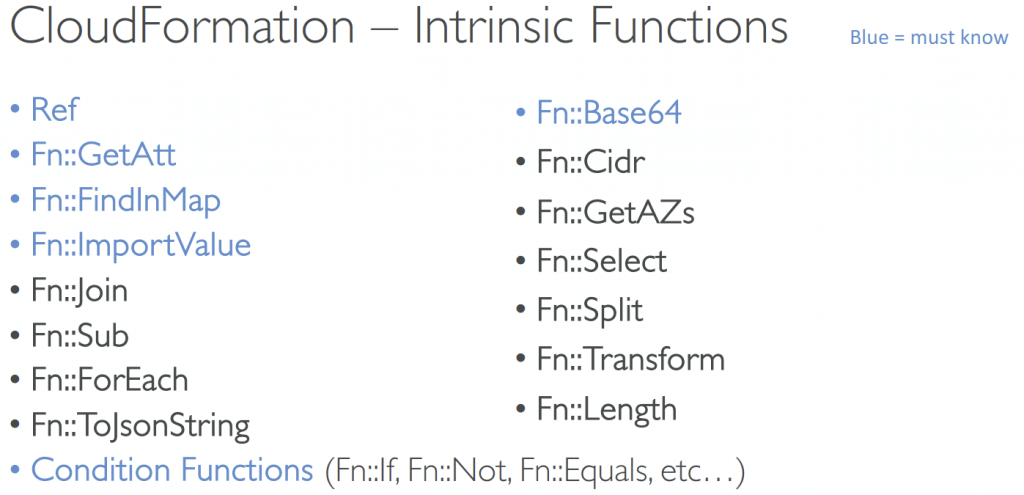
- Intrinsic Functions
- Fn::Ref (!Ref)
- Parameters – returns the value of the parameter
- Resources – returns the physical ID of the underlying resource (e.g., EC2 ID)
- Fn::GetAtt (!GetAtt)
- Attributes are attached to any resources you create
- Fn::FindInMap (!FindInMap) [MapName, TopLevelKey, SecondLevelKey]
- Fn::ImportValue (!ImportValue)
- Import values that are expor ted in other stacks
- Fn::Base64 (!Base64)
- convert string to Base64; heavily used in EC2 instance’s UserData property
- user data script log is in /var/log/cloud-init-output.log
- Conditions (Fn::If, Fn::Not, Fn::Equal, Fn::And, Fn::Or, etc)
- Fn::Ref (!Ref)
- Rollbacks
- Stack Creation Fails:
- Default: ever ything rolls back (gets deleted). We can look at the log
- Option to disable rollback and troubleshoot what happened
- Stack Update Fails:
- The stack automatically rolls back to the previous known working state
- Ability to see in the log what happened and error messages
- Rollback Failure? Fix resources manually then issue ContinueUpdateRollback API from Console
- Or from the CLI using continue-update-rollback API call
- Stack Creation Fails:
- Service Role
- IAM role that allows CloudFormation to create/update/delete stack resources on your behalf
- User must have iam:PassRole permissions
- Capabilities
- CAPABILITY_(Resource Named)_IAM & CAPABILITY_IAM
- Necessary to enable when you CloudFormation template is creating or updating IAM resources (IAM User, Role, Group, Policy, Access Keys, Instance Profile…)
- CAPABILITY_AUTO_EXPAND, for Macro and Nested stakes
- Necessar y when your CloudFormation template includes Macros or Nested Stacks (stacks within stacks) to perform dynamic transformations
- InsufficientCapabiltiesException
- Exception that will be thrown by CloudFormation if the capabilities haven’t been acknowledged when deploying a template (security measure)
- CAPABILITY_(Resource Named)_IAM & CAPABILITY_IAM
- DeletionPolicy
- Default: Delete (wont work in S3 if the bucket is not empty)
- Retain
- Snapshot: create a final snapshot before deleted
- works with storage related (EBS, ElastiCache, RDS, Redshift, Neptune, etc)
- Stack policy is a JSON to tell which resource(s) should be protected as not touched during update; so an explicit ALLOW for the desired resources for update is needed
- Termination Protection is to prevent accidental delete
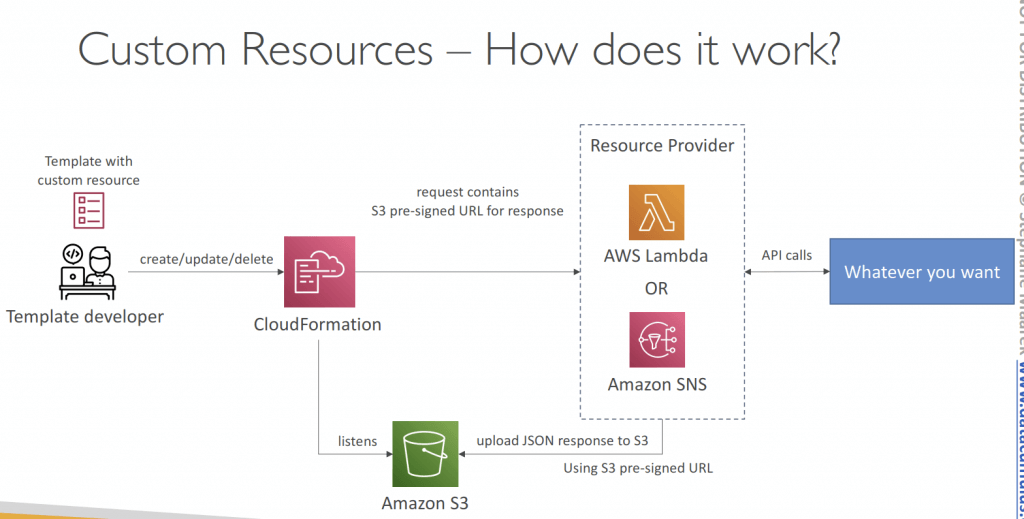
- Custom Resources
- custom functions running via Lambda, for example, empty a S3 bucket
- AWS::CloudFormation::CustomResource or Custom::MyCustomResourceTypeName
- Properties with Service Token (Lambda function or SNS topic, in the sam region) and optional Input data
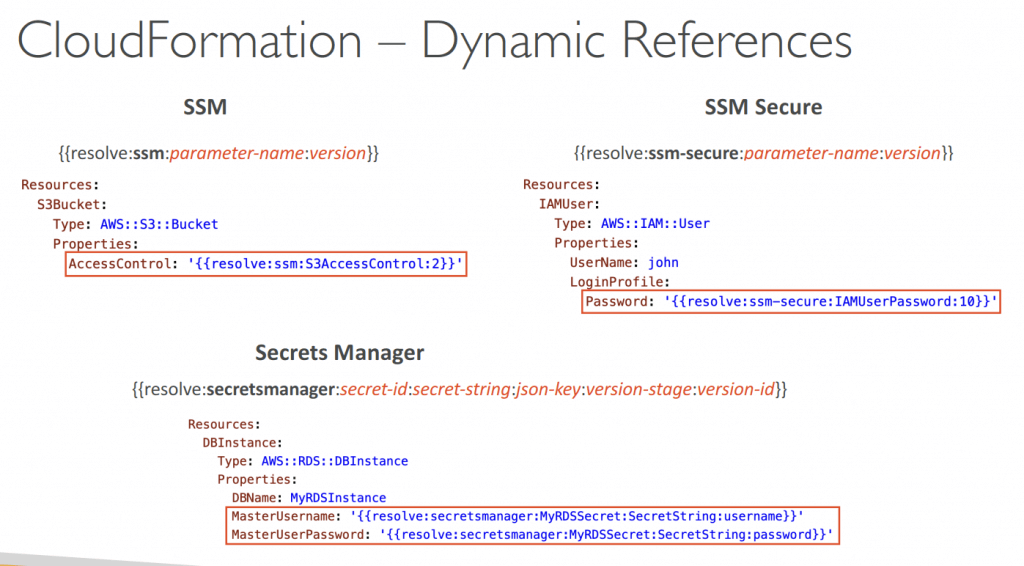
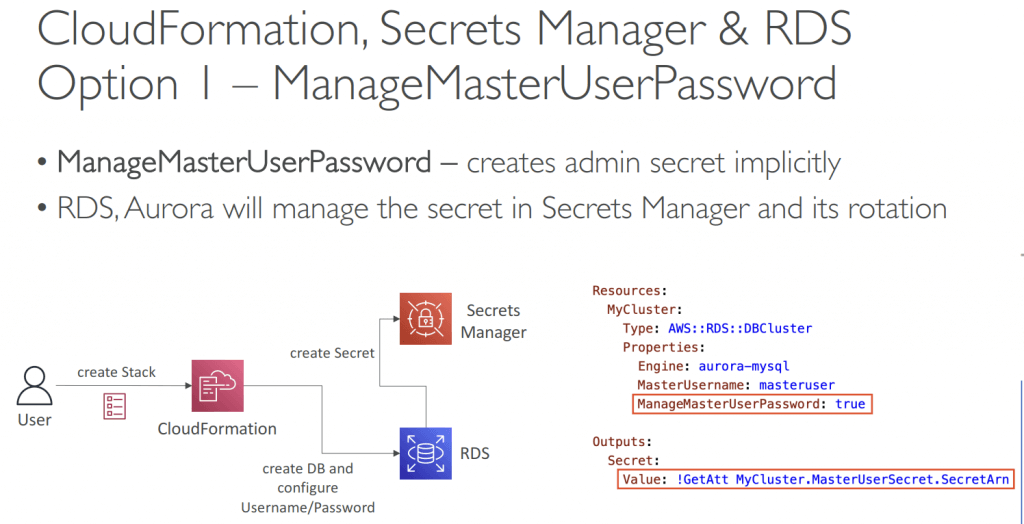
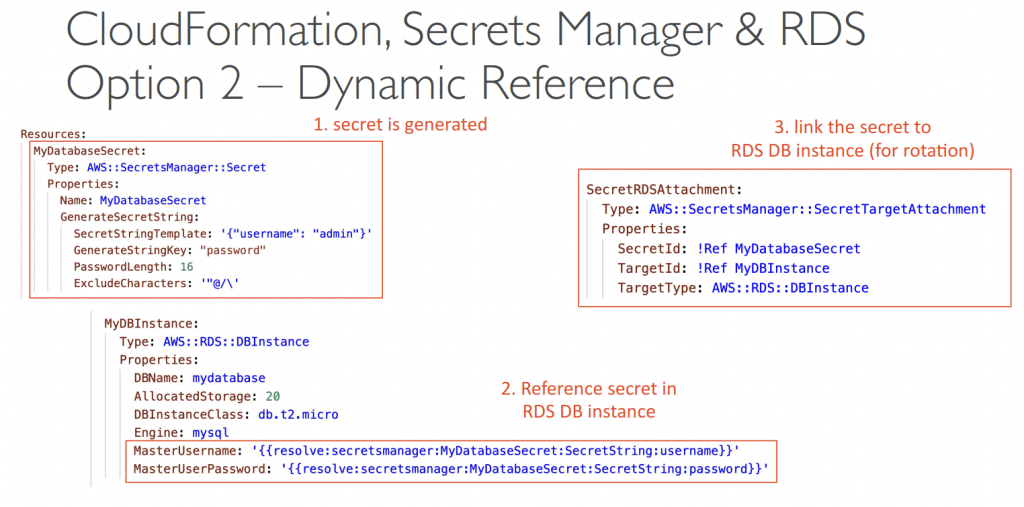
- Dynamic References
- Reference external values stored in Systems Manager Parameter Store and Secrets Manager within CloudFormation templates
- CloudFormation retrieves the value of the specified reference during create/update/delete operations
- Using ‘{{resolve:service-name:reference-key}}’
- ssm – for plaintext values stored in SSM Parameter Store
- ssm-secure – for secure strings stored in SSM Parameter Store
- secretsmanager – for secret values stored in Secrets Manager
- (Python) Helper scripts
- cfn-init – Use to retrieve and interpret resource metadata, install packages, create files, and start services.
- AWS::CloudFormation::Init
- A config contains the following and is executed in that order
- Packages: used to download and install pre-packaged apps and components on Linux/Windows (ex. MySQL, PHP, etc…)
- Groups: define user groups
- Users: define users, and which group they belong to
- Sources: download files and archives and place them on the EC2 instance
- Files: create files on the EC2 instance, using inline or can be pulled from a URL
- Commands: run a series of commands
- Services: launch a list of sysvinit
- AWS::CloudFormation::Init
- cfn-signal – Use to signal with a WaitCondition, so you can synchronize other resources in the stack when the prerequisite resource or application is ready
- WaitCondition
- Block the template until it receives a signal from cfn-signal
- We attach a CreationPolicy (also works on EC2, ASG)
- We can define a Count > 1 (in case you need more than 1 signal)
- Troubleshooting: Verify that the instance has a connection to the Internet.
- WaitCondition
- cfn-get-metadata – Use to retrieve metadata for a resource or path to a specific key.
- cfn-hup – Use to check for updates to metadata every 15(default) minutes and execute custom hooks when changes are detected.
- cfn-init – Use to retrieve and interpret resource metadata, install packages, create files, and start services.
- Troubleshooting
- DELETE_FAILED
- Some resources must be emptied before deleting, such as S3 buckets
- Use Custom Resources with Lambda functions to automate some actions
- Security Groups cannot be deleted until all EC2 instances in the group are gone
- Think about using DeletionPolicy=Retain to skip deletions
- UPDATE_ROLLBACK_FAILED
- Can be caused by resources changed outside of CloudFormation, insufficient permissions, Auto Scaling Group that doesn’t receive enough signals…
- Manually fix the error and then ContinueUpdateRollback
- DELETE_FAILED
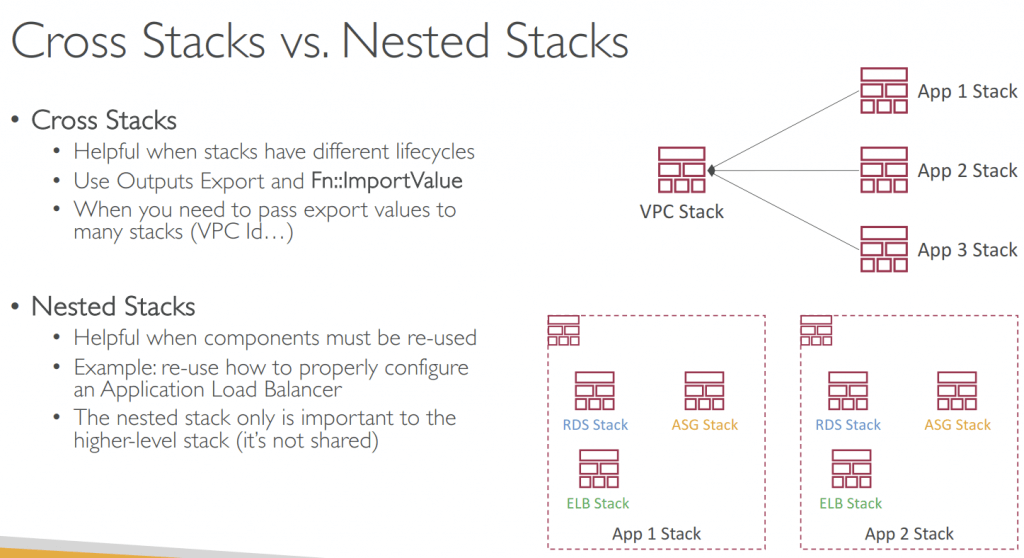
- Nested Stacks
- Nested stacks are stacks as par t of other stacks
- Nested stacks are considered best practice
- To update a nested stack, always update the parent (root stack)
- Nested stacks can have nested stacks themselves!
- DependsOn
- Specify that the creation of a specific resource follows another
- When added to a resource, that resource is created only after the creation of the resource
specified in the DependsOn attribute - Applied automatically when using !Ref and !GetAtt
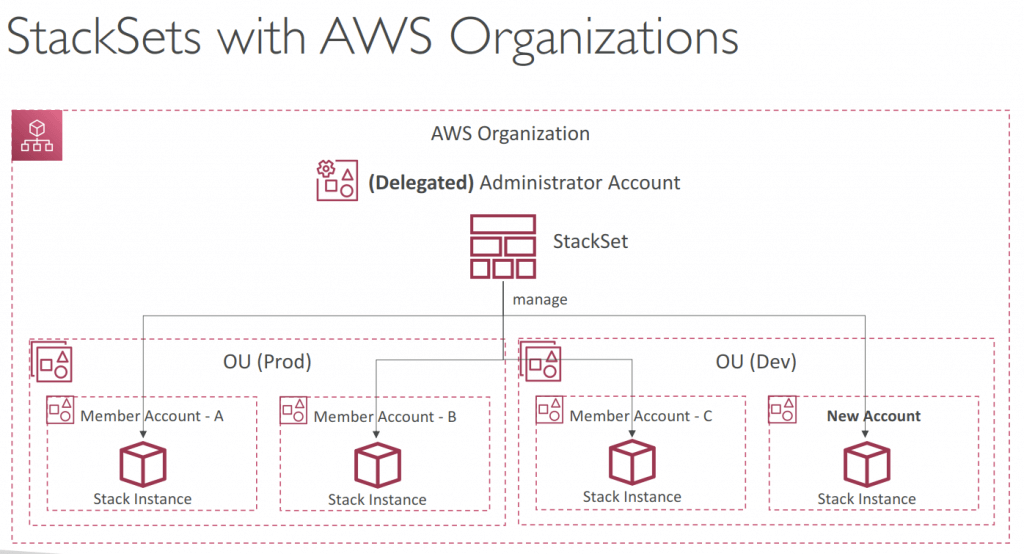
- Stackset is used for cross accounts/regions stacks management, with a single CloudFormation template.
- A stack instance is simply a reference to a stack in a target account within a region.
- When you update a stackset, all associated stack instances are updated throughout all accounts and regions
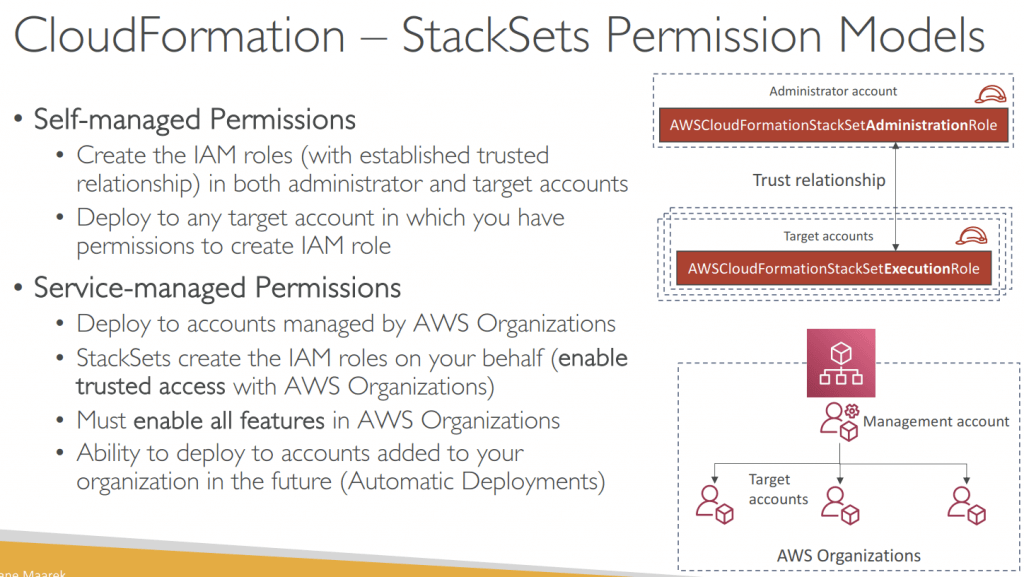
- Permission Models
- Self-managed Permissions
- Create the IAM roles (with established trusted relationship) in both administrator and target accounts
- Deploy to any target account in which you have permissions to create IAM role
- Service-managed Permissions
- Deploy to accounts managed by AWS Organizations
- StackSets create the IAM roles on your behalf (enable trusted access with AWS Organizations)
- Must enable all features in AWS Organizations
- Ability to deploy to accounts added to your organization in the future (Automatic Deployments)
- Self-managed Permissions
- Troubleshooting
- A stack operation failed, and the stack instance status is OUTDATED.
- Insufficient permissions in a target account for creating resources that are specified in your template.
- The template could be trying to create global resources that must be unique but aren’t, such as S3 buckets
- The administrator account does not have a trust relationship with the target account
- Reached a limit or a quota in the target account (too many resources)
- A stack operation failed, and the stack instance status is OUTDATED.
- Drift
- Performs drift detection on the stack associated with each stack instance in the StackSet
- If the current state of a resource in a stack varies from the expected state:
- The stack considered drifted
- And the stack instance that the stack associated with considered drifted
- And the StackSet is considered drifted
- Drift detection identifies unmanaged changes (outside CloudFormation)
- Changes made through CloudFormation to a stack directly (not at the StackSet level), aren’t considered drifted
- You can stop drift detection on a StackSet
- ChangeSets
- When you update a stack, you need to know what changes will happen before it applying them for greater confidence
- ChangeSets won’t say if the update will be successful
- For Nested Stacks, you see the changes across all stacks
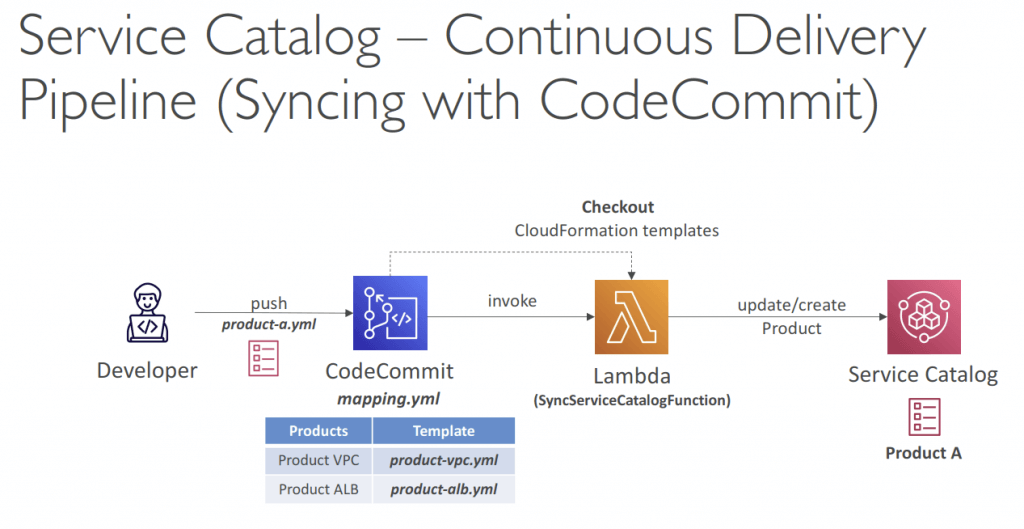
- AWS Service Catalog
- “AWS Service Catalog can be used for resource configuration”
- a quick self-service portal to launch a set of authorized products pre-defined by admins
- Create and manage catalogs of IT ser vices that are approved on AWS
- The “products” are CloudFormation templates
- Ex: Virtual machine images, Servers, Software, Databases, Regions, IP address ranges
- CloudFormation helps ensure consistency, and standardization by Admins
- They are assigned to Portfolios (teams)
- Teams are presented a self-service portal where they can launch the products
- All the deployed products are centrally managed deployed services
- Helps with governance, compliance, and consistency
- Can give user access to launching products without requiring deep AWS knowledge
- Integrations with “self-service portals” such as ServiceNow
- Stack Set Constraints
- Accounts
- Regions
- Permissions
- Launch Constraints
- IAM Role assigned to a Product which allows a user to launch, update, or terminate a product with minimal IAM permissions
- Example: end user has access only to Service Catalog, all other permissions required are
attached to the Launch Constraint IAM Role - IAM Role must have the following permissions:
- CloudFormation (Full Access)
- AWS Services in the CloudFormation template
- S3 Bucket which contains the CloudFormation template (Read Access)
- Local artifacts declared in CodeUri property
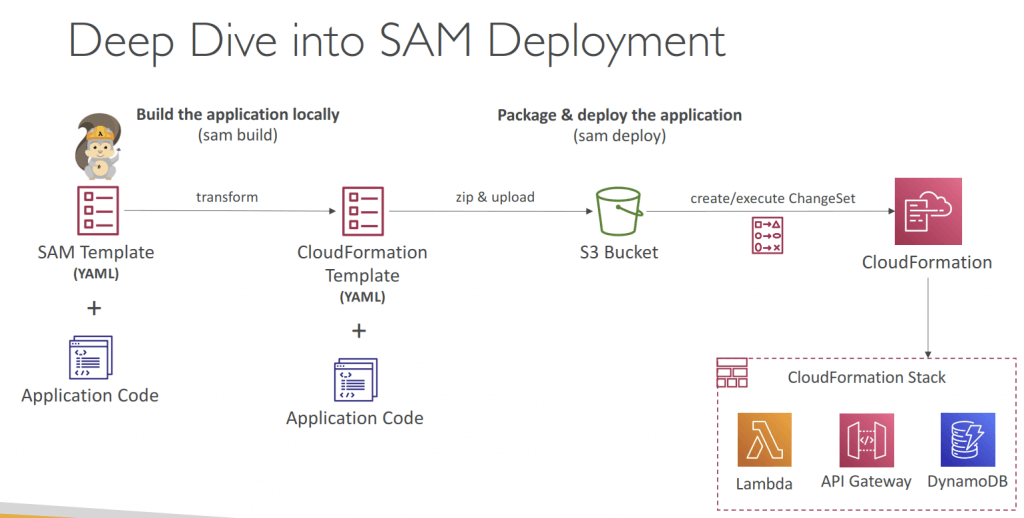
- The aws cloudformation package command packages the local artifacts (local paths) that your AWS CloudFormation template references.
- After you package your template’s artifacts, run the aws cloudformation deploy command to deploy the returned template.
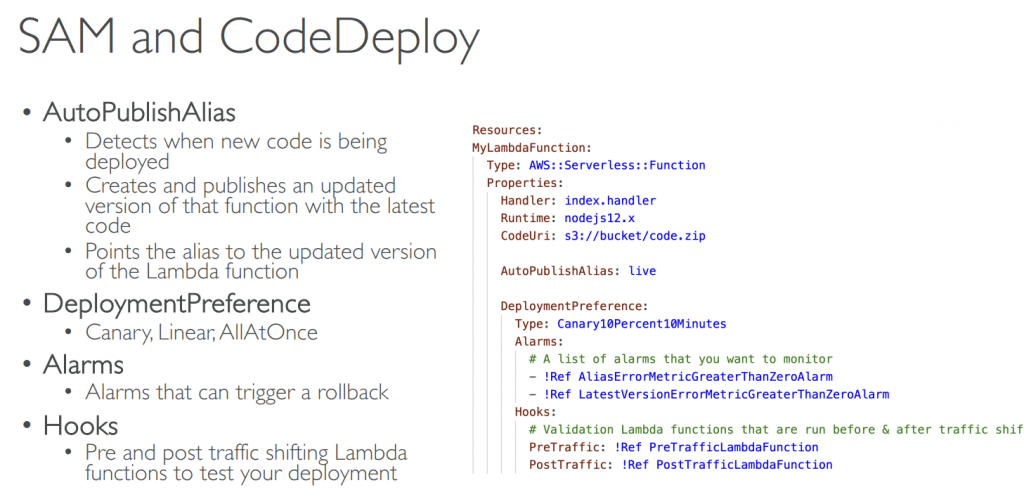
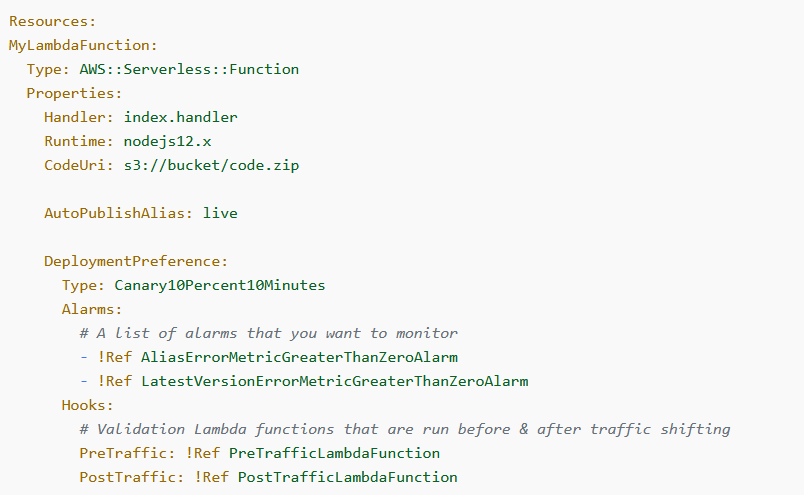
AWS Serverless Application Model (SAM)
- configure via YAML, complied to CloudFormation stack
- use CodeDeploy for Lambda function
- Traffic Shifting (from OLD ver to New ver)
- Linear: grow traffic every N minutes until 100%
- Canary: try X percent then 100%
- AllAtOnce: immediate
- Pre- and Pro- for testing on traffic shifting
- Pre and Post traffic hooks features to validate deployment (before the traffic shift star ts and after it ends)
- rollback by AWS CloudWatch Alarm
- AppSpec.yml
- Name
- Alias
- CurrentVersion
- TargetVersion
- Traffic Shifting (from OLD ver to New ver)
- run Lambda, API Gateway, DynamoDB locally
- Lambda start/invoke
- API Gateway
- AWS Events (sample payloads for event resources)
- SAM Recipe
- Transform Header – template
- Write Code
- AWS::Serverless::Function
- AWS::Serverless::Api
- AWS::Serverless::SimpleTable
- Package and Deploy – into S3 Bucket
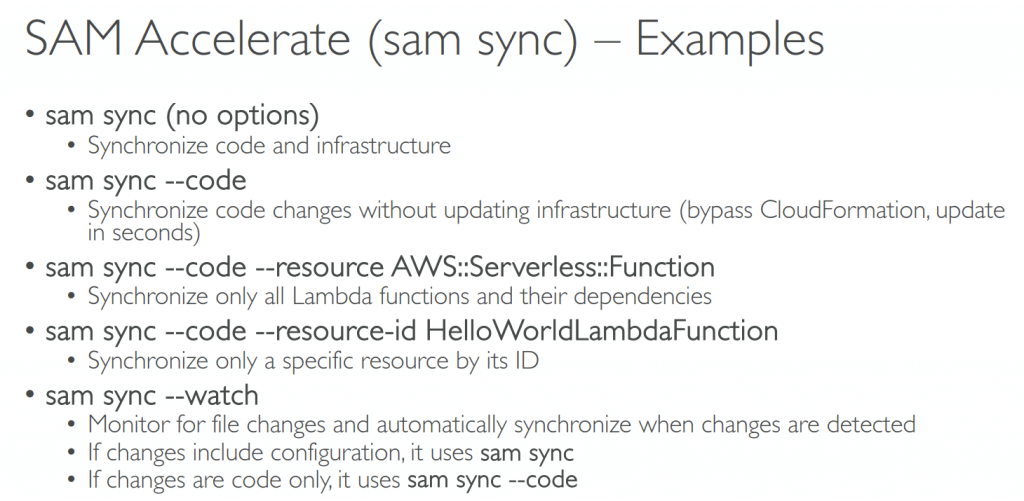
- Quickly sync local changes to AWS Lambda (SAM Accelerate): sam sync –watch
- SAM commands
- sam init – creating a new SAM project
- sam build – resolve dependencies and construct deployment artifacts for all functions and layers in the SAM template.
- sam package – prepares the serverless application for deployment by zipping artifacts, uploading them to S3, and generating a CloudFormation template with references to the uploaded artifacts in S3. But, it doesn’t deploy the application.
- sam deploy – zips your code artifacts, uploads them to Amazon S3, and produces a packaged AWS SAM template file that it uses to deploy your application
- for nested applications, need “
CAPABILITY_AUTO_EXPAND” option - Compared with “aws cloudformation deploy” – deploy a CloudFormation stack, it expects that your artifacts are already packaged and uploaded to S3.
- for nested applications, need “
- sam publish – publishes an AWS SAM application to the AWS Serverless Application Repository
- sam sync – update existing SAM template
- as Accelerate, reduce latency on deployments for rapid development testing
- using “–code” option, without updating infrastructure (service APIs and bypass CloudFormation)
- sam local
- can specify a named profile from your AWS CLI configuration using the –profile parameter with the sam local invoke command
- run the aws configure with the –profile option to set the credentials for a named profile
- AWS SAM template file
- AWS::Serverless::Application – for nested application
- AWS::Serverless::Function – configuration information for creating a Lambda function
- AWS::Serverless::LayerVersion – creates a Lambda layer version (LayerVersion) that contains library or runtime code that’s needed by a Lambda function
- AWS::Serverless::Api – describes an API Gateway resource. It’s useful for advanced use cases where you want full control and flexibility when you configure your APIs. Mostly as part of event sources of “AWS::Serverless::Function”
- SAM Policy Templates
- apply permissions to Lambda Functions
- SAM Multiple Environments, using “samconfig.toml”
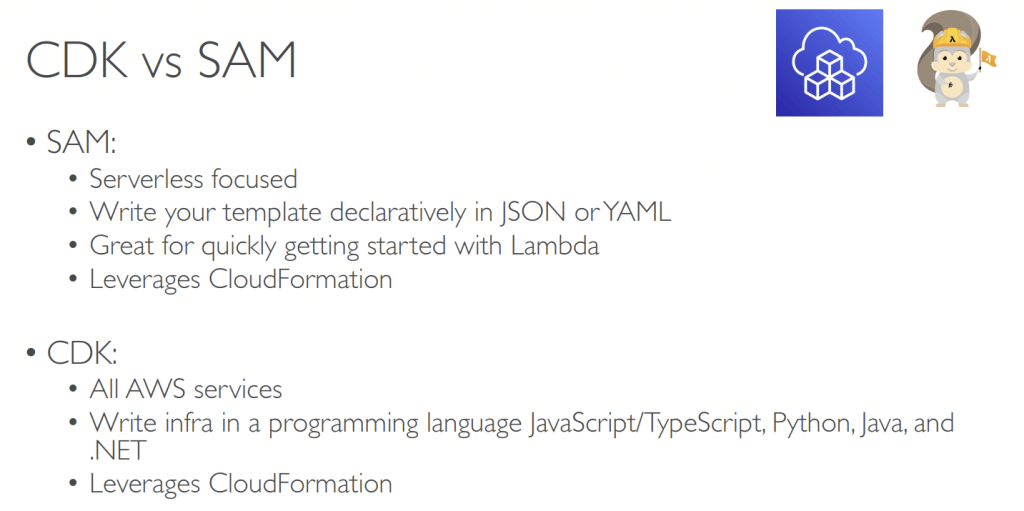
Cloud Development Kit (CDK)
- CloudFormation using JSON/YAML, but CDK using Javascript/Typescript, Python, Java, .Net
- Contain higher level components, constructs
- encapsulate everything for final CloudFormation stack creation
- AWS Construct Library or Construct Hub
- Layer 1 (L1): CloudFormation(CFN) resources, prefix with “Cfn”, and all resource properties needed to be explicitly configured
- Layer 2 (L2): intent-based API resources, with defaults and boilerplate, also can use methods
- Layer 3 (L3): aka Patterns, represents as multiple related resources (for example, API Gateway + Lambda, or Fargate cluster + Application Load Balancer)
- The codes would be complied to CloudFormation template
- Benefits for Lambda & ECS/EKS as infrastructures and applications runtime codes implemented together
- SAM focus on serverless, good for Lambda, but only JSON/YAML
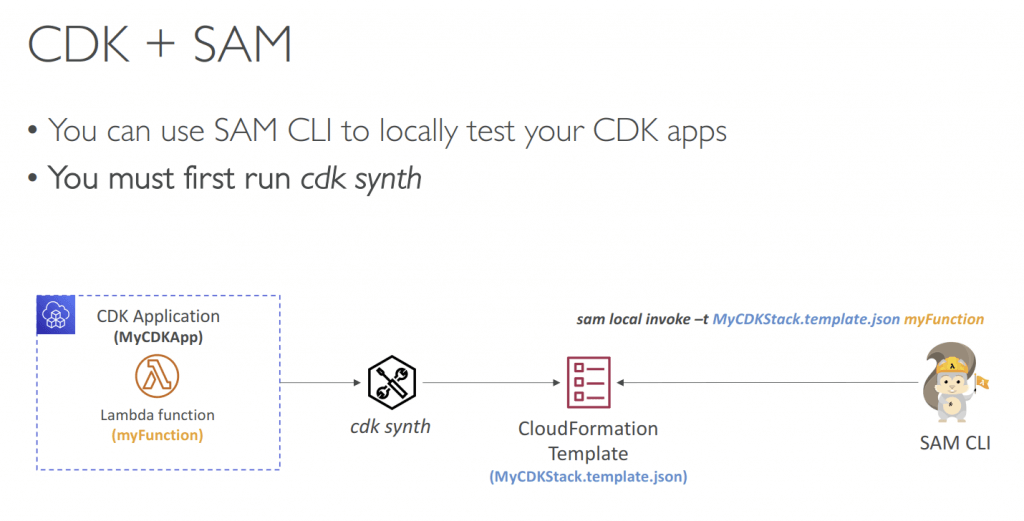
- Bootstrapping: the process of provisioning before deploying AWS environment (Account+Region)
- CDKToolkit (CloudFormation stack), with S3 Bucket – store files and IAM Roles
- Error: “Policy contains a statement with one or more invalid principal”, due to the lack of new IAM Roles for each new environment
- UnitTest, using CDK Assertion Module for Jest(Javascript) or Pytest(Python)
- Fine-granted Assertions (common): check certain property of certain resource
- Snapshot Test: test against baseline template
AWS Elastic Beanstalk
- provision infrastructure using a text-based template that describes exactly what resources are provisioned and their settings
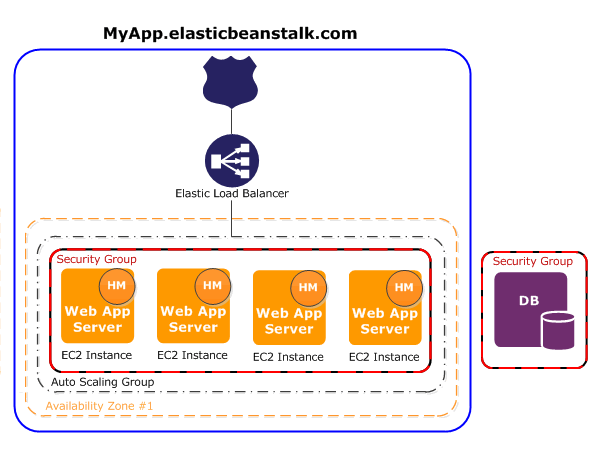
- Amazon EC2 Instance
- Amazon CloudWatch
- ELB & ASG
- AWS S3
- RDS, DynamoDB
- Amazon SNS
- complied to CloudFormation stack
- Managed service
- Automatically handles capacity provisioning, load balancing, scaling, application health monitoring, instance configuration…
- Just the application code is the responsibility of the developer
- Components
- Application
- collection of Elastic Beanstalk components (environments, versions, configurations…)
- Application Version
- an iteration of your application code
- Environment
- Collection of AWS resources running an application version (only one application version at a time)
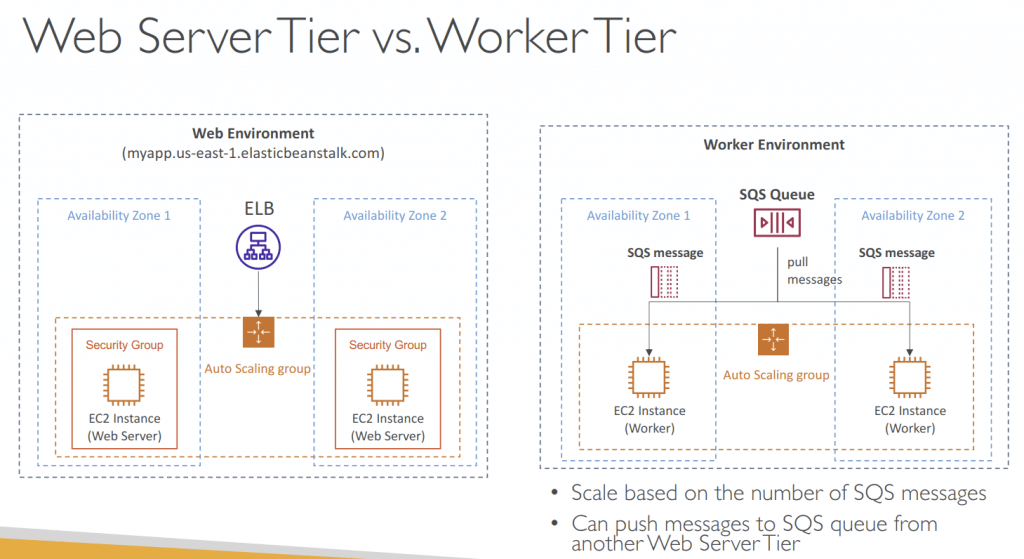
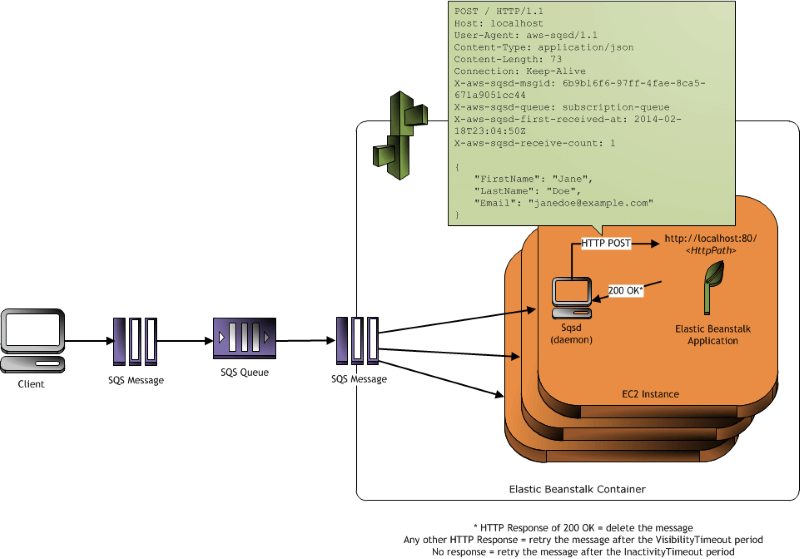
- Web Server Tier and Worker Tier
- If your application performs tasks that are long to complete, offload these tasks to a dedicated worker environment
- Elastic Beanstalk worker environments simplify the process by managing the Amazon SQS queue (with support of DLQ) and running a daemon process on each instance that reads from the queue
- define periodic tasks in a file cron.yaml
- If your application performs tasks that are long to complete, offload these tasks to a dedicated worker environment
- Application
- Deployment Method
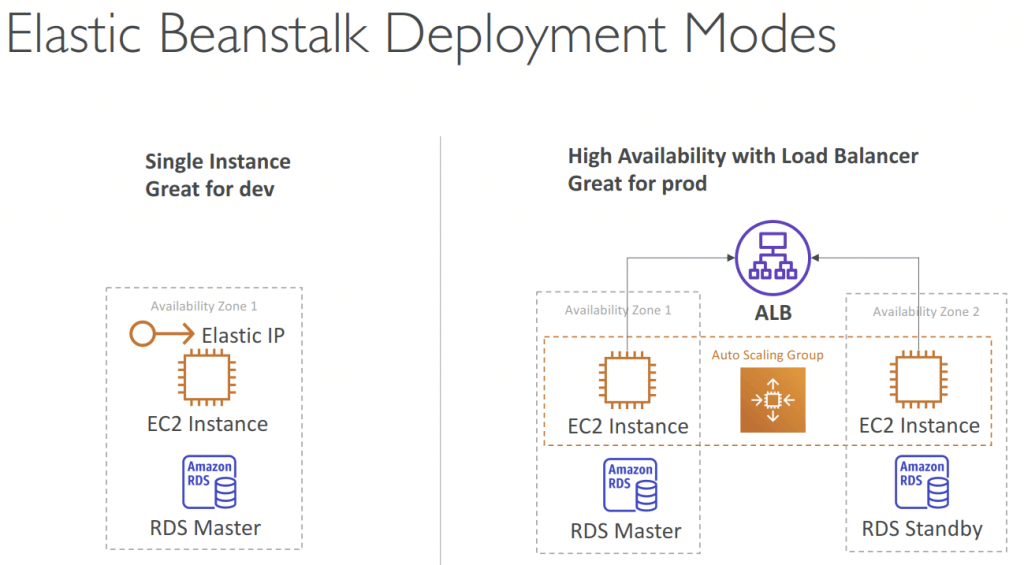
- All at once, has downtime <- Fastest!
- Deploy the new version to all instances simultaneously. All instances in your environment are out of service for a short time while the deployment occurs. This is the method that provides the least amount of time for deployment
- Rolling: running under capacity, no additional costs
- Rolling with additional batches: compared to Rolling, this let application running at capacity (ie temporary create more instances)
- Immutable: create new instances in a new ASG, then swap; zero downtime
- Immutable deployments perform an immutable update to launch a full set of new instances running the new version of the application in a separate Auto Scaling group, alongside the instances running the old version. Immutable deployments can prevent issues caused by partially completed rolling deployments. If the new instances don’t pass health checks, Elastic Beanstalk terminates them, leaving the original instances untouched.
- Blue Green: new environment then swap
- Not a “direct feature” of Elastic Beanstalk
- using Route53 with weighted policies
- Not suitable for applications with RDS instance tightly coupled
- a Blue/green deployment requires that your environment runs independently of your production database; If your Elastic Beanstalk environment has an attached Amazon RDS DB instance, the data will be lost if you terminate the original (blue) environment.
- Traffic Splitting: canary testing
- If there’s a deployment failure, this triggers an automated rollback (very quick)
- using ALB with weighted policies
- All at once, has downtime <- Fastest!

| Method | Impact of failed deployment | Deploy time | Zero downtime | No DNS change | Rollback process | Code deployed to |
|---|---|---|---|---|---|---|
| All at once | Downtime |  | No | Yes | Manual redeploy | Existing instances |
| Rolling | Single batch out of service; any successful batches before failure running new application version |   † † | Yes | Yes | Manual redeploy | Existing instances |
| Rolling with an additional batch | Minimal if first batch fails; otherwise, similar to Rolling |    | Yes | Yes | Manual redeploy | New and existing instances |
| Immutable | Minimal |     | Yes | Yes | Terminate new instances | New instances |
| Traffic splitting | Percentage of client traffic routed to new version temporarily impacted |     | Yes | Yes | Reroute traffic and terminate new instances | New instances |
| Blue/green | Minimal |     | Yes | No | Swap URL | New instances |
- Lifecycle
- max most Application versions: 1000, use LifeCycle Policy to phase out, based on Time or Space
- has option to retain source bundles on S3
- only deletes old .config files
- the minimum age limit is set in days, not hours
- EB deletion policy
- concerns the handling of associated resources, particularly Amazon RDS databases and application versions, when an environment or application is terminated or deleted
- When an Elastic Beanstalk environment is terminated, other resources provisioned by Elastic Beanstalk, such as EC2 instances, load balancers, and security groups, are typically deleted automatically. However, resources like S3 buckets used for application versions or logs may need manual cleanup if not managed by the application version lifecycle policy.
- EB Extensions
- YAML/JSON, with “.config” extension as file name
- update defaults with “option_settings”
- place under the “.ebextensions/” folder under root of source code
- resources managed by .ebextensions would be deleted if the environment goes away
- EB Clone, can help to setup exact same “configuration” environment
- Load Balancer type and configure
- RDS configure, but no data
- Environment variables
- EB Migration
- Once EB created, the Elastic Load Balancer (ELB) type cannot change
- Create another environment with new ELB, then using Route53 update or CNAME swap
- Decouple RDS with EB, for PROD
- Once EB created, the Elastic Load Balancer (ELB) type cannot change
- extra Configuration file could be able to add to the source bundle
- cron.yaml – schedule tasks
- env.yaml – configure the environment name, solution stack, and environment links
- Dockerrun.aws.json – multi-container Docker environments that are hosted in Elastic Beanstalk
- Notifications
- Create Rules in EventBridge to act to the following events:
- Environment Operations Status – create, update, terminate (start, success, fail)
- Other Resources Status – ASG, ELB, EC2 Instance (created, deleted)
- Managed Updates Status – started, failed
- Environment Health Status
- Create Rules in EventBridge to act to the following events:
- [ 🧐QUESTION🧐 ] Deploy existing applications with long installation/configuration setup, with dynamically massive loading
- each of the instances took more than half an hour to download the required application libraries and become fully configured
- A custom AMI can improve provisioning times when instances are launched in your environment if you need to install a lot of software that isn’t included in the standard AMIs.
- Using configuration files is great for configuring and customizing your environment quickly and consistently. Applying configurations, however, can start to take a long time during environment creation and updates. If you do a lot of server configuration in configuration files, you can reduce this time by making a custom AMI that already has the software and configuration that you need.
- A custom AMI also allows you to make changes to low-level components, such as the Linux kernel, that are difficult to implement or take a long time to apply in configuration files. To create a custom AMI, launch an Elastic Beanstalk platform AMI in Amazon EC2, customize the software and configuration to your needs, and then stop the instance and save an AMI from it.
- An Amazon RDS instance attached to an Elastic Beanstalk environment is ideal for development and testing environments. However, it’s not ideal for production environments because the lifecycle of the database instance is tied to the lifecycle of your application environment. If you terminate the environment, then you will lose your data because the Amazon RDS instance is deleted by the environment.
- [ 🧐QUESTION🧐 ] Why to set up an Amazon RDS MySQL database with a Multi-AZ deployments configuration that is decoupled from the Elastic Beanstalk stack
- An Amazon RDS instance attached to an Elastic Beanstalk environment is ideal for development and testing environments. However, it’s not ideal for production environments because the lifecycle of the database instance is tied to the lifecycle of your application environment. If you terminate the environment, then you will lose your data because the Amazon RDS instance is deleted by the environment.
- [ 🧐QUESTION🧐 ] Deploy existing RDS in current Elastic Beanstalk with least data loss
- Decouple the Amazon RDS instance from your Elastic Beanstalk environment using the blue/green deployment strategy to decouple. Take an RDS DB snapshot of the database and enable deletion protection. Set up a new Elastic Beanstalk environment with the necessary information to connect to the Amazon RDS instance. Before terminating the old Elastic Beanstalk environment, remove its security group rule first before proceeding.
- To allow the Amazon EC2 instances in your environment to connect to an outside database, you can configure the environment’s Auto Scaling group with an additional security group. The security group that you attach to your environment can be the same one that is attached to your database instance, or a separate security group from which the database’s security group allows ingress.
- You can connect your environment to a database by adding a rule to your database’s security group that allows ingress from the autogenerated security group that Elastic Beanstalk attaches to your environment’s Auto Scaling group. However, doing so creates a dependency between the two security groups. Subsequently, when you attempt to terminate the environment, Elastic Beanstalk will be unable to delete the environment’s security group because the database’s security group is dependent on it.
- When you terminate the environment, all Elastic Beanstalk resources are deleted except for the DB instance and the RDS security group that Elastic Beanstalk created. When you create an RDS instance as a part of load balanced Elastic Beanstalk environment, Elastic Beanstalk creates an Elastic Load Balancing (ELB) security group. Elastic Beanstalk also creates an Amazon Elastic Compute Cloud (Amazon EC2) security group to attach to the EC2 instances in the environment. And, Elastic Beanstalk creates an RDS security group to attach to the RDS instance. To allow inbound traffic at port 3306 from the EC2 security group, Elastic Beanstalk adds a security group inbound rule to the RDS security group.
- When you decouple the database, Elastic Beanstalk doesn’t remove the security group inbound rule. This security group inbound rule references the EC2 security group from the RDS security group that Elastic Beanstalk created. When you terminate the environment, Elastic Beanstalk can’t terminate the environment because the decouple RDS security group still references the EC2 security group.
- Decouple the Amazon RDS instance from your Elastic Beanstalk environment using the blue/green deployment strategy to decouple. Take an RDS DB snapshot of the database and enable deletion protection. Set up a new Elastic Beanstalk environment with the necessary information to connect to the Amazon RDS instance. Before terminating the old Elastic Beanstalk environment, remove its security group rule first before proceeding.
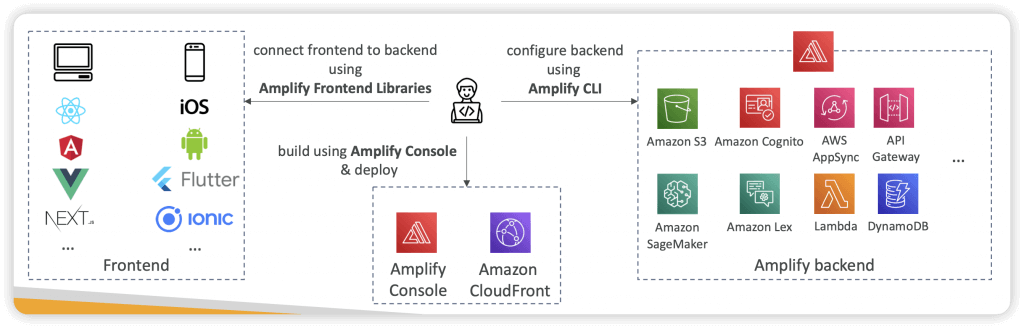
AWS Amplify
- create mobile and web applications (aka. ElasticBeans for mobile and web application)
- Authentication (Cognito), Storage (AppSync + DynamoDB), API (REST, GraphQL), CI/CD, PubSub, Analytics, AI/ML Predictions, Monitoring…
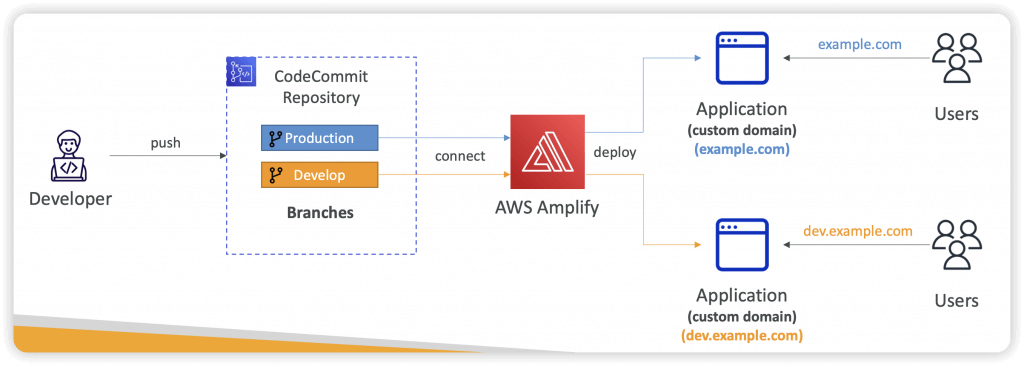
- Connect your source code from GitHub, AWS CodeCommit, Bitbucket, GitLab, or upload directly
- End-to-End (E2E) test, using Cypress
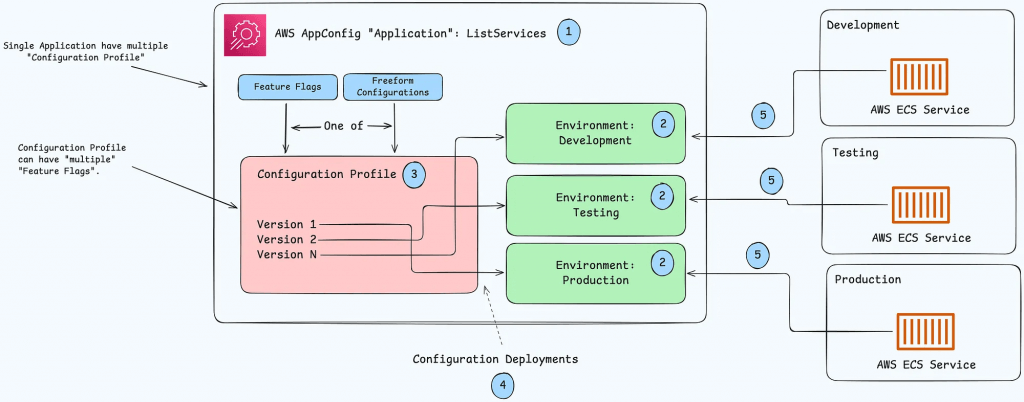
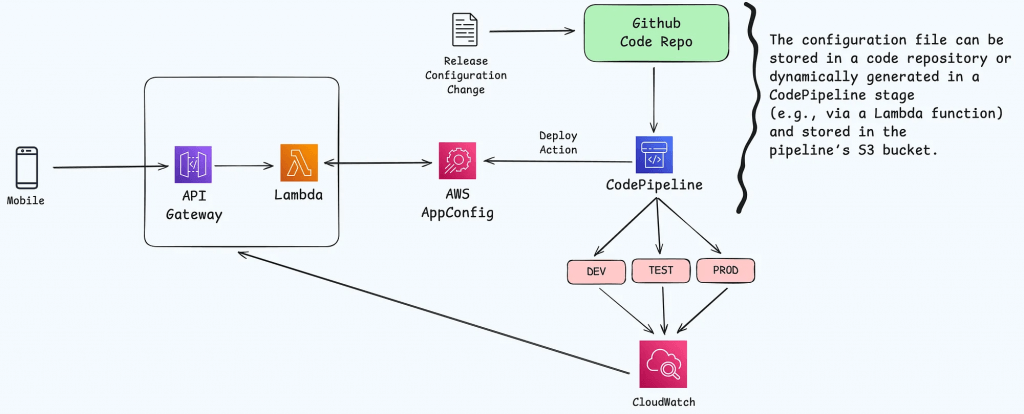
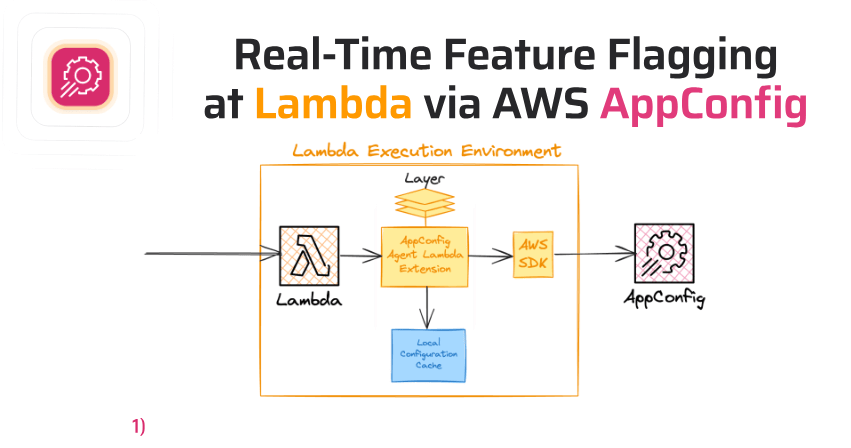
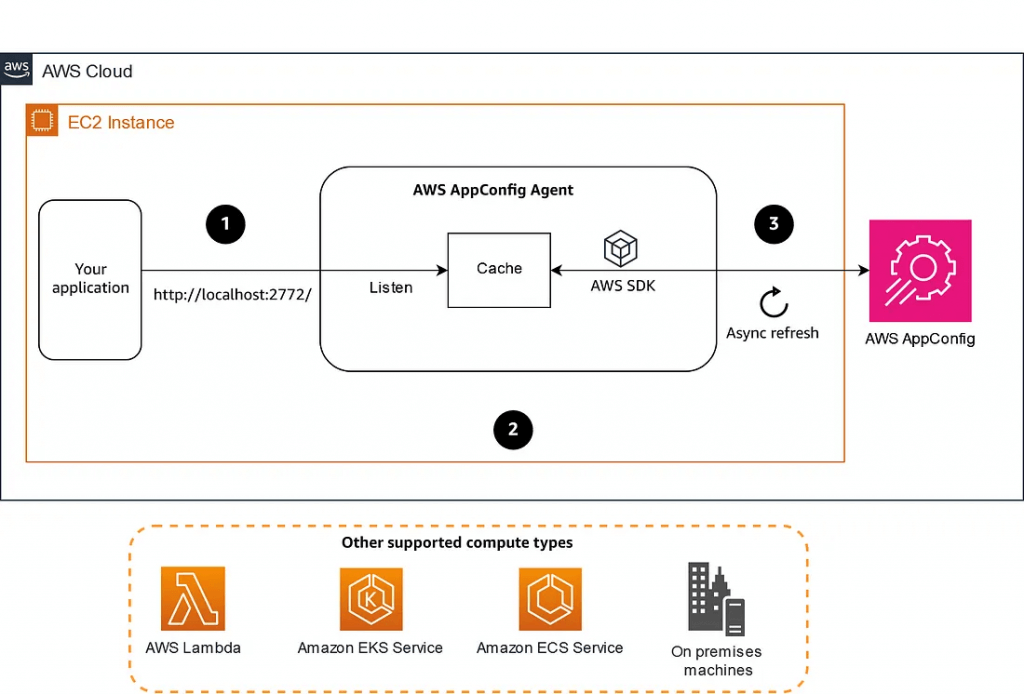
AWS AppConfig
- deploy dynamic configuration change without code deployment
- provides the functionality to manage feature flags, a powerful technique that allows developers to test and control new features in live environments
- Use with apps on EC2 instances, Lambda, ECS, EKS…
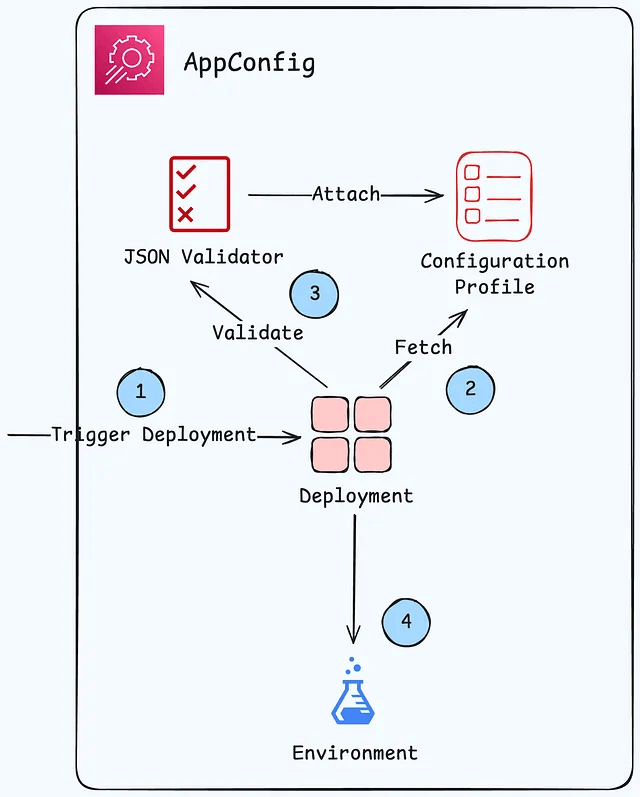
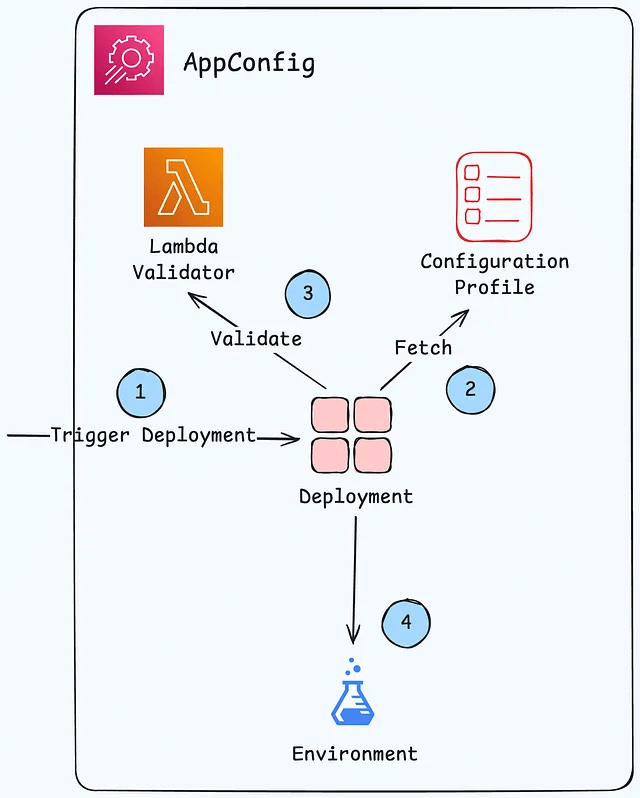
- Validate configuration changes before deployment using:
- JSON Schema (syntactic check) or
- Lambda Function – run code to perform validation (semantic check)
| Feature | AWS AppConfig | AWS Amplify |
|---|---|---|
| Primary Function | Configuration Management | Full-Stack Development |
| Focus | Dynamic Configuration Updates, Feature Flags, A/B Testing | Frontend Development, Backend Creation, Deployment |
| Use Cases | Feature Rollouts, Operational Changes, Scaling for Traffic Spikes | Rapid Prototyping, Building Web/Mobile Apps |
| Complexity | Relatively simpler for configuration management | Can involve more complex setups for full-stack applications |
| Typical Workflow | Defining configurations, deploying to environments, monitoring | Defining frontend components, creating backend resources, deploying to hosting environments |
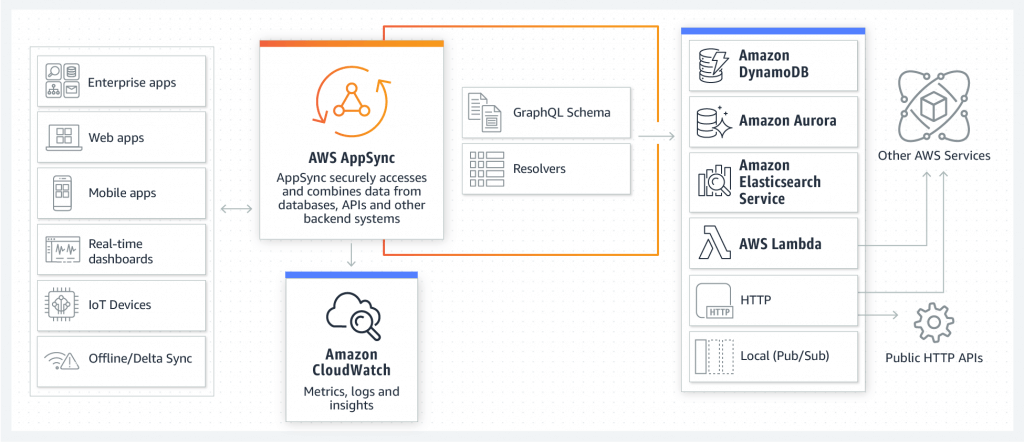
AWS AppSync
- extend Cognito Sync (user data, like app preferences or game state), and also allowing multiple users to synchronize and collaborate in real time on shared data.
- managed service of GraphQL, combining multiples data sources
- retrieve data in “realtime” or “MQTT” of WebSocket
- for mobile apps: local data access and data sync
- Security: API_KEY, AWS_IAM, OPENID_CONNECT, AMAZON_COGNITO_USER_POOLS
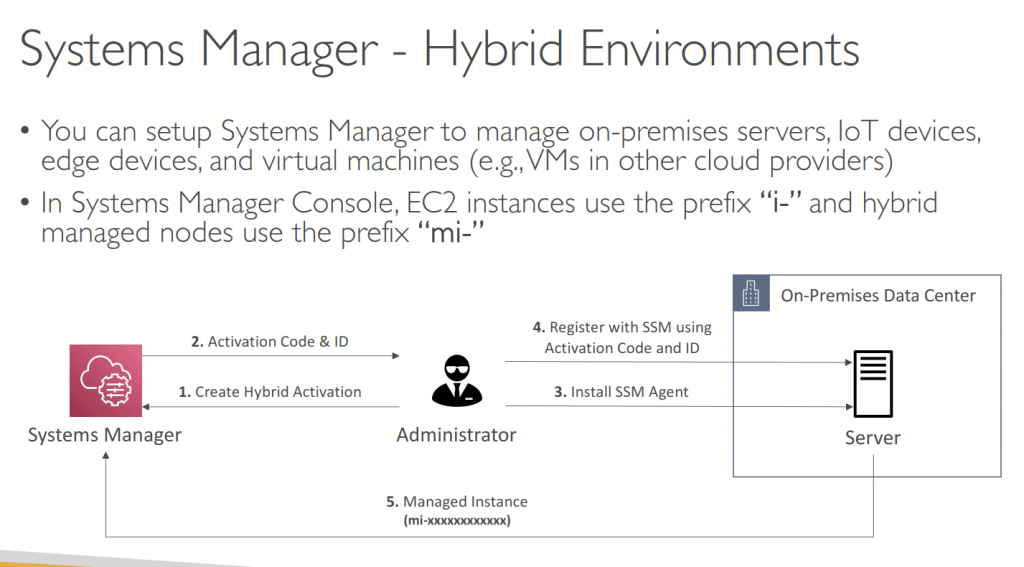
AWS Systems Manager
- focused on management and operations of AWS resources (EC2 and On-Premise), such as automation, patching, and configuration
- Patching automation for enhanced compliance
- with SSM Agent installed on system nodes
- Tools
- Node Tools
- Fleet Manager
- Session Manager
- Patch Manager
- Operation Tools
- Explorer
- OpsCenter
- Incident Manager
- Change Management Tools
- Automation
- Change Manager
- Maintenance Windows
- Application Tools
- Application Manager
- AppConfig
- Parameter Store
- Node Tools
- Documents: JSON or YAML
- Run Commands: Execute a document (= script) or just run a command
- Rate Control / Error Control
- Integrated with IAM & CloudTrail
- No need for SSH
- Command Output can be shown in the Console, sent to S3 bucket or CloudWatch Logs
- Send notifications to SNS about command statues (In progress, Success, Failed…)
- Can be invoked using EventBridge
- use SSM Run Command to configure instances without having to login to an instance. This setup requires the SSM agent to be installed on your EC2 instance and that proper IAM permission has been granted. Additionally, create an Amazon EventBridge rule to monitor the launch or termination events of the Auto Scaling group. Set the Systems Manager Run Command as the target for this rule.
- On the parameters of SSM Run Command, define the commands you need to update the configuration file. It is important that your target EC2 instance is properly tagged and defined on the SSM Run command as it will be the basis of SSM to identify your instance.
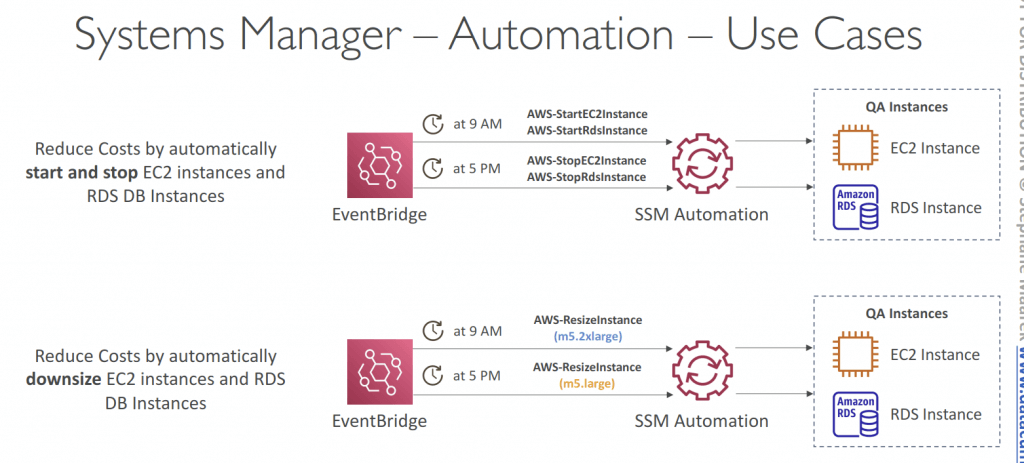
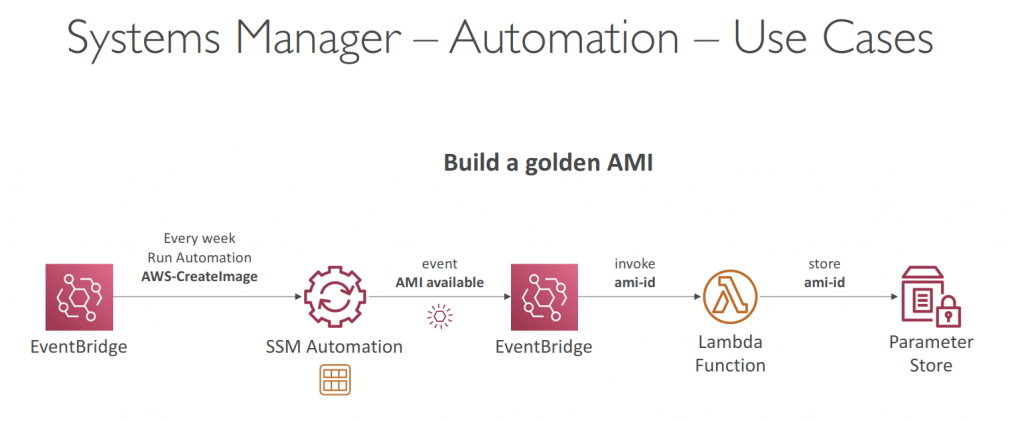
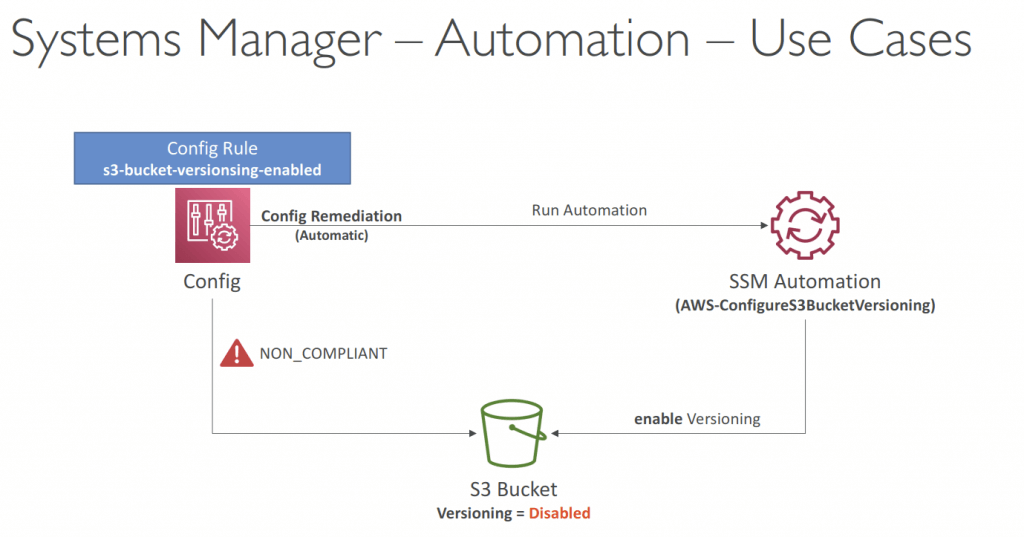
- Automation
- Automation Runbook
- SSM Documents of type Automation
- Defines actions preformed on your EC2 instances or AWS resources
- Pre-defined runbooks (AWS) or create custom runbooks
- Can be triggered
- Manually using AWS Console, AWS CLI or SDK
- By Amazon EventBridge
- On a schedule using Maintenance Windows
- By AWS Config for rules remediations
- Automation Runbook
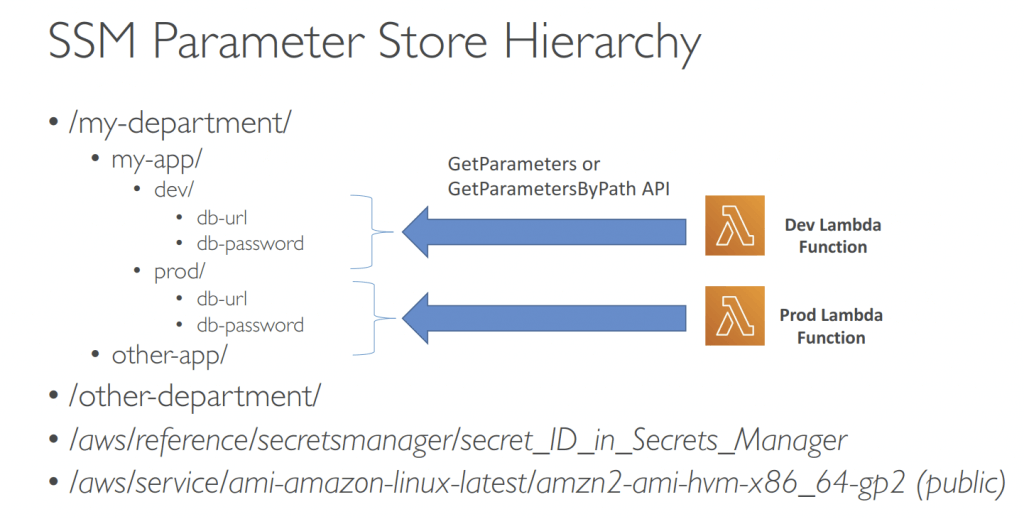
- Parameter Store
- Secure storage for configuration and secrets
- Optional Seamless Encryption using KMS
- Serverless, scalable, durable, easy SDK
- Version tracking of configurations / secrets
- Security through IAM
- Notifications with Amazon EventBridge
- Integration with CloudFormation
- Parameters Policies (for advanced parameters)
- Allow to assign a TTL to a parameter (expiration date) to force updating or deleting sensitive data such as passwords
- Can assign multiple policies at a time
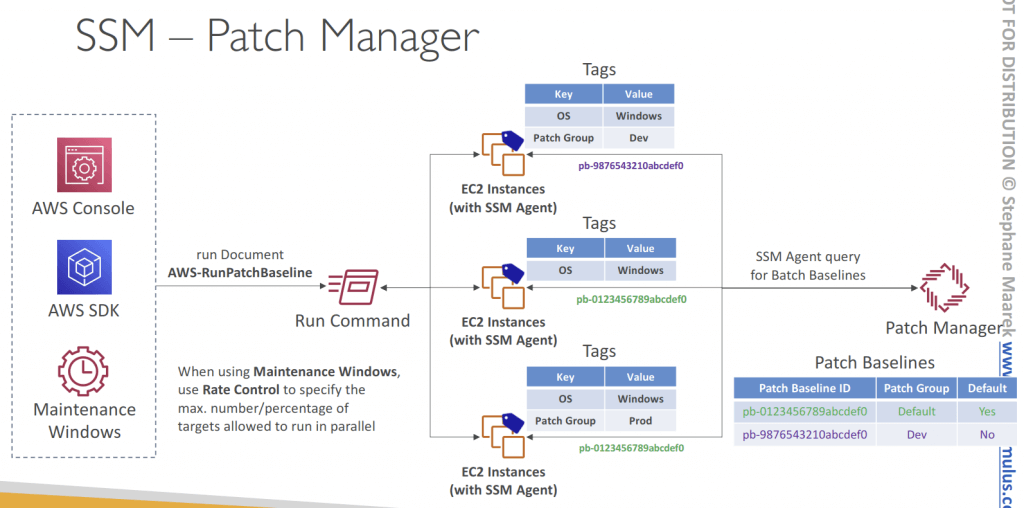
- Patch Manager
- Automates the process of patching managed instances
- OS updates, applications updates, security updates…
- Supports both EC2 instances and on-premises servers
- Supports Linux, macOS, and Windows
- Patch on-demand or on a schedule using Maintenance Windows
- Scan instances and generate patch compliance report (missing patches)
- Patch compliance report can be sent to S3
- Patch Baseline
- Defines which patches should and shouldn’t be installed on your instances
- Ability to create custom Patch Baselines (specify approved/rejected patches)
- Patches can be auto-approved within days of their release
- By default, install only critical patches and patches related to security
- Pre-Defined Patch Baseline
- Managed by AWS for different Operating Systems (can’t be modified)
- AWS-RunPatchBaseline (SSM Document) – apply both operating system and
application patches (Linux, macOS, Windows Server)
- Custom Patch Baseline
- Create your own Patch Baseline and choose which patches to auto-approve
- Operating System, allowed patches, rejected patches…
- Ability to specify custom and alternative patch repositories
- Patch Group
- Associate a set of instances with a specific Patch Baseline
- Example: create Patch Groups for different environments (dev, test, prod)
- Instances should be defined with the tag key Patch Group
- An instance can only be in one Patch Group
- Patch Group can be registered with only one Patch Baseline
- Maintenance Windows
- Defines a schedule for when to perform actions on your instances
- Example: OS patching, updating drivers, installing software…
- Maintenance Window contains
- Schedule
- Duration
- Set of registered instances
- Set of registered tasks
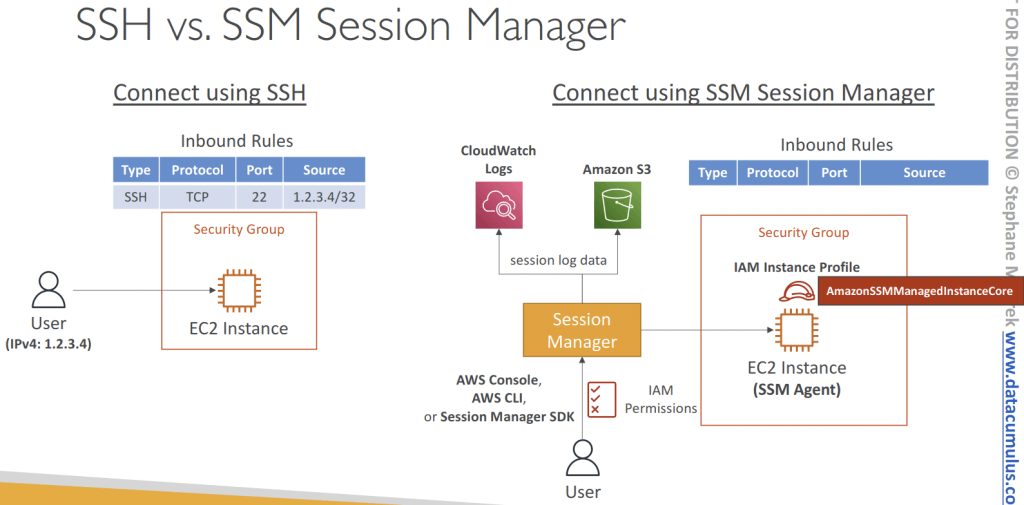
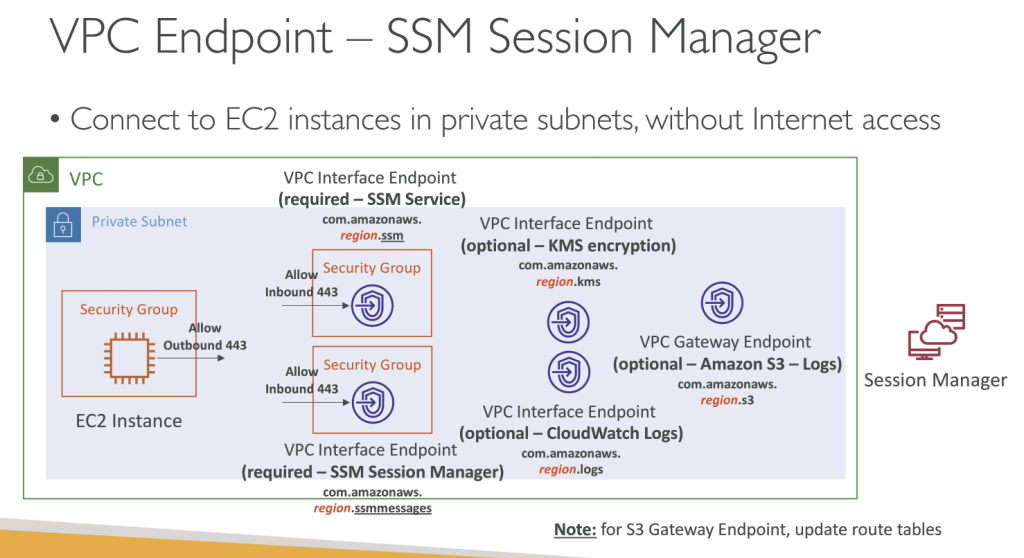
- Session Manager
- Allows you to star t a secure shell on your EC2 and on-premises servers
- Access through AWS Console, AWS CLI, or Session Manager SDK
- Does not need SSH access, bastion hosts, or SSH keys
- Session log data can be sent to S3 or CloudWatch Logs
- CloudTrail can intercept StartSession events
- IAM Permissions
- Control which users/groups can access Session Manager and which instances
- Use tags to restrict access to only specific EC2 instances
- Access SSM + write to S3 + write to CloudWatch
- Optionally, you can restrict commands a user can run in a session
- Default Host Management Configuration (DHMC)
- essentially creates a default IAM role with necessary permissions, allowing Systems Manager to manage all instances within an AWS account and region without requiring individual instance profiles
- When enabled, it automatically configure your EC2 instances as managed instances without the use of EC2 Instance Profile
- Instance Identity Role – a type of IAM Role with no permissions beyond identifying the EC2 instance to AWS Services (e.g., Systems Manager)
- EC2 instances must have IMDSv2 enabled and SSM Agent installed (doesn’t suppor t IMDSv1)
- Automatically enables Session Manager, Patch Manager, and Inventory
- Automatically keeps the SSM Agent up to date
- Must be enabled per AWS Region
- Benefits:
- Simplified setup: Eliminates the need to manually create and attach IAM roles to individual instances.
- Centralized management: Provides a central point for managing permissions for all EC2 instances related to Systems Manager.
- Reduced overhead: Simplifies the process of onboarding new instances into Systems Manager.
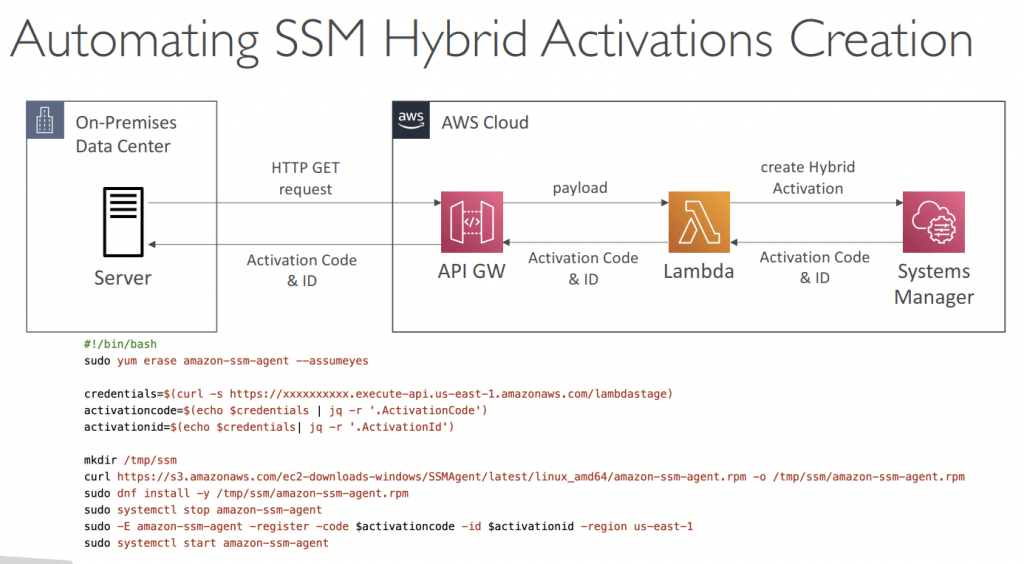
- IoT Greengrass Instance Activation
- Manage IoT Greengrass Core devices using SSM
- Install SSM Agent on Greengrass Core devices (registered as a managed node in SSM)
- SSM Agent can be installed manually or deployed as a Greengrass Component (pre-built software module that you deploy directly to Greengrass Core devices)
- You must add permissions to the Token Exchange Role (IAM Role for the IoT core device) to communicate with Systems Manager
- Supports all SSM Capabilities (Patch Manager, Session Manager, Run Command…)
- Use cases: easily update and maintain OS and software updates across a fleet of Greengrass Core devices
- Compliance
- Scan your fleet of managed nodes for patch compliance and configuration inconsistencies
- Displays current data about:
- Patches in Patch Manager
- Associations in State Manager
- Can sync data to an S3 bucket using Resource Data Sync, and you can analyze using Athena and QuickSight
- Can collect and aggregate data from multiple accounts and regions
- Can send compliance data to Security Hub
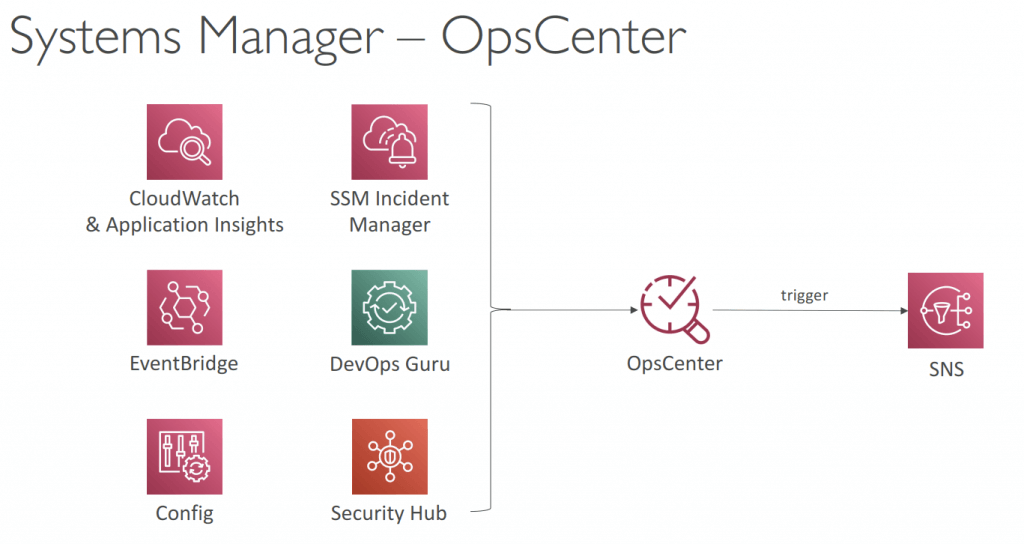
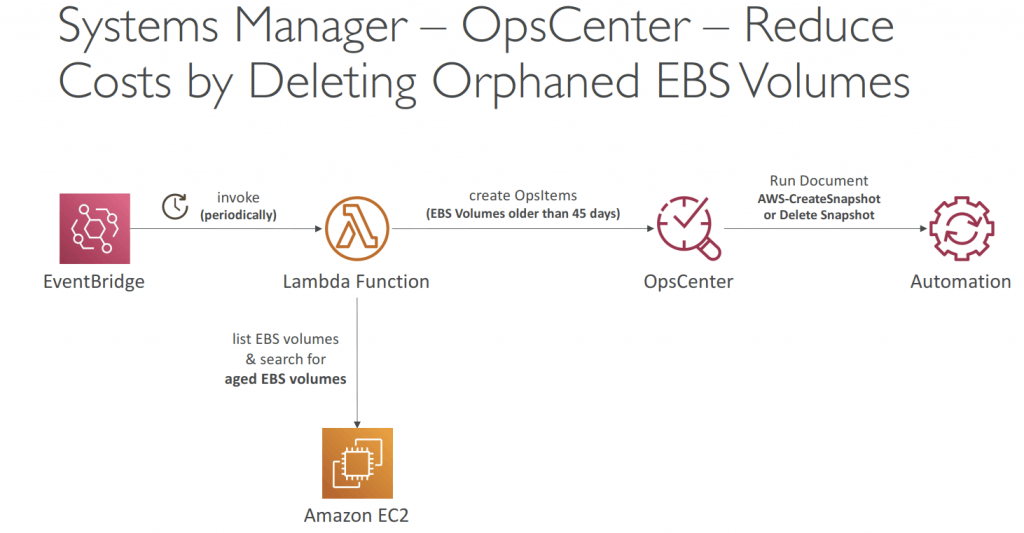
- OpsCenter
- Allows you to view, investigate, and remediate issues in one place (no need to navigate across different AWS services)
- Security issues (Security Hub), performance issues (DynamoDB throttle), failures (ASG failed launch instance)…
- OpsItems
- Operational issue or interruption that needs investigation and remediation
- Event, resource, AWS Config changes, CloudTrail logs, EventBridge…
- Provides recommended Runbooks to resolve the issue
- Supports both EC2 instances and on-premises managed nodes
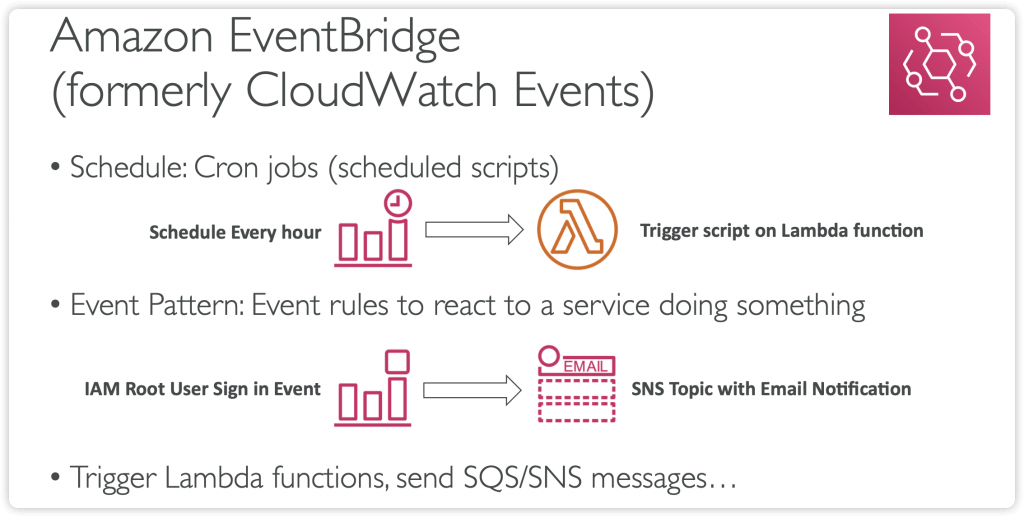
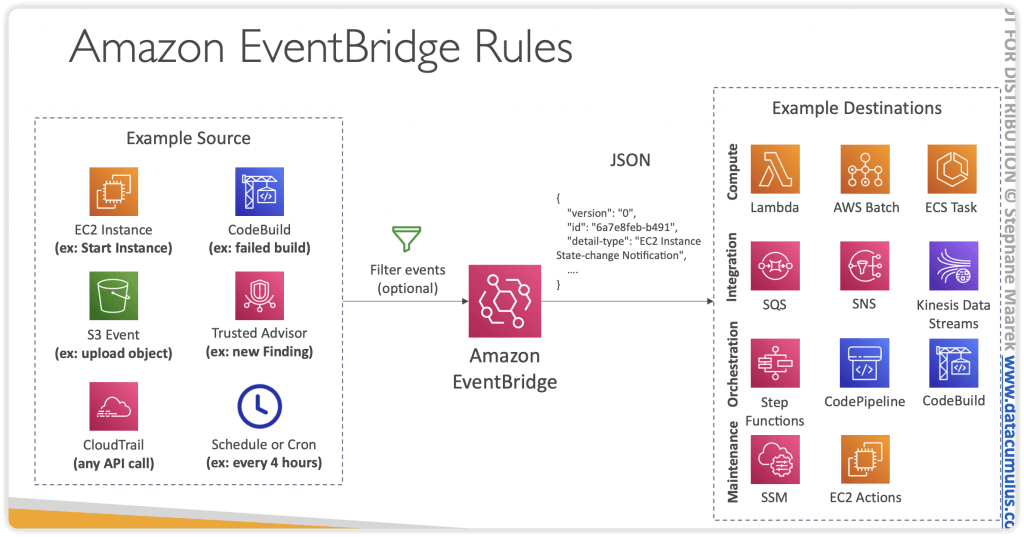
Amazon EventBridge
- previous CloudWatch Events
- Schedule: Cron jobs (scheduled scripts)
- Schedule Every hour Trigger script on Lambda funchon
- Event Pattern: Event rules to react to a service doing something
- IAM Root User Sign in Event SNS Topic with Email Nohficahon
- Trigger Lambda functions, send SQS/SNS messages…
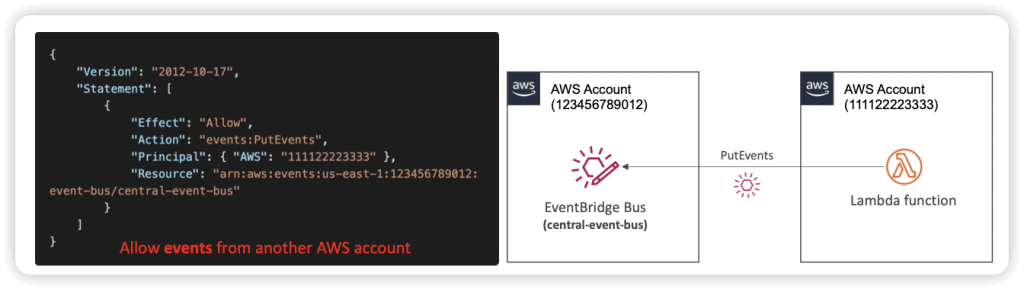
- Event buses can be accessed by other AWS accounts using Resource-based Policies
- You can archive events (all/filter) sent to an event bus (indefinitely or set period)
- Ability to replay archived events
- Schema Registry
- EventBridge can analyze the events in your bus and infer the schema
- The Schema Registry allows you to generate code for your application, that will know in advance how data is structured in the event bus
- Schema can be versioned
- Resource-based Policy
- Manage permissions for a specific Event Bus
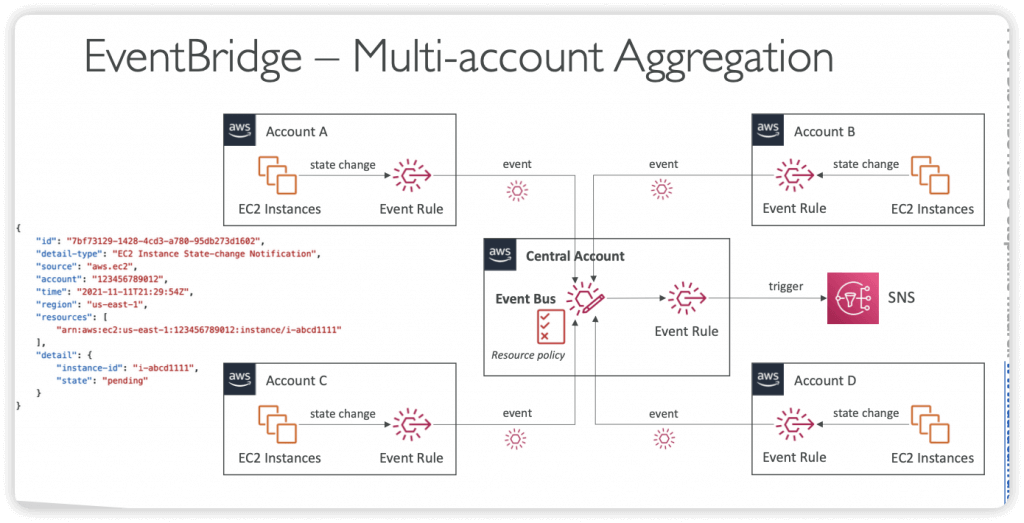
- Example: allow/deny events from another AWS account or AWS region
- Use case: aggregate all events from your AWS Organization in a single AWS account or AWS region
- Manage permissions for a specific Event Bus
AWS Application Auto Scaling
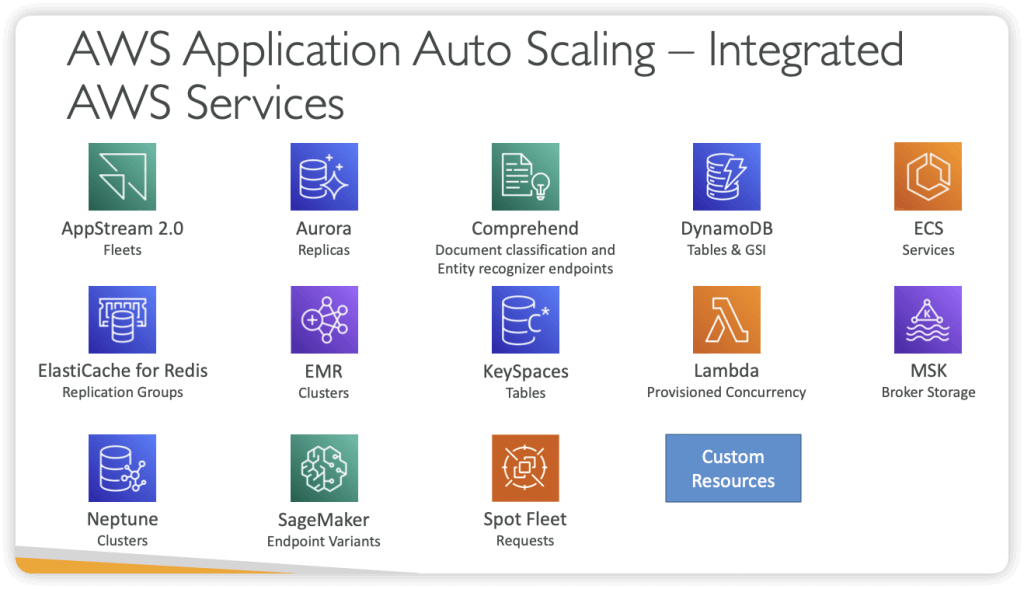
- Monitors your apps and automatically adjusts capacity to maintain steady, predictable performance at lowest cost
- Setup scaling for multiple resources across multiple services from a single place (no need to navigate across different services)
- Point to your app and select the services and resources you want to scale (no need to setup alarms and scaling actions for each service)
- Search for resources/services using CloudFormation Stack, Tags, or EC2 ASG
- Build Scaling Plans to automatically add/remove capacity from your resources in real-time as demand changes
- Supports Target Tracking, Step, and Scheduled Scaling Policies
Multi-AZ Architectures
- Services where Multi-AZ must be enabled manually:
- EFS, ELB, ASG, Beanstalk: assign AZ
- RDS, ElastiCache: multi-AZ (synchronous standby DB for failovers)
- Aurora:
- data is stored automatically across multi-AZ
- Can have multi-AZ for the DB itself (same as RDS)
- OpenSearch (managed): multi master
- Jenkins (self deployed): multi master
- Service where Multi-AZ is implicitly there:
- S3 (except OneZone-Infrequent Access)
- DynamoDB
- All of AWS’ proprietary, managed services
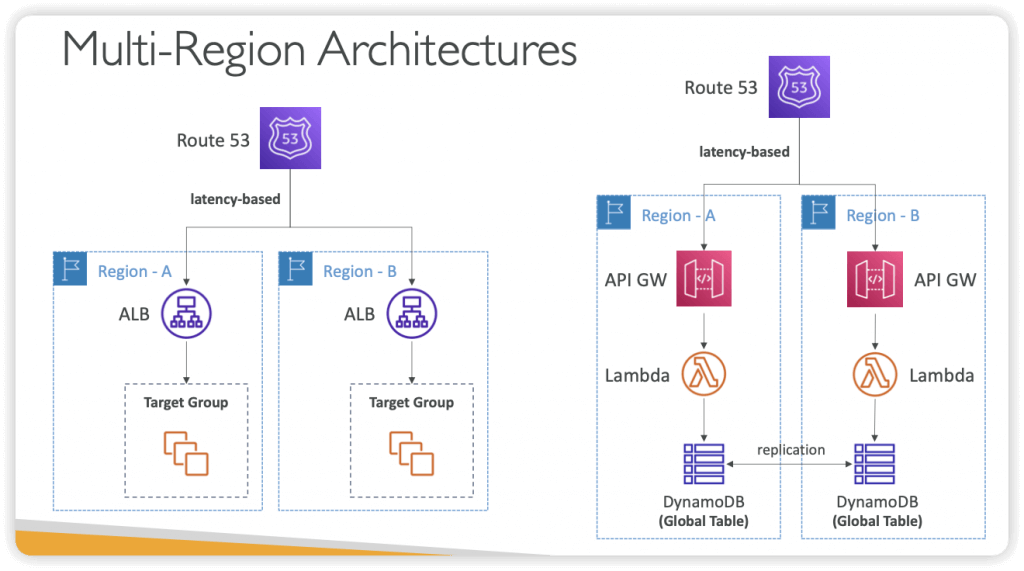
Multi-Region Architectures
- DynamoDB Global Tables (multi-way replication, enabled by Streams)
- AWS Config Aggregators (multi region & multi account)
- RDS Cross Region Read Replicas (used for Read & DR)
- Aurora Global Database (one region is master, other is for Read & DR)
- EBS volumes snapshots, AMI, RDS snapshots can be copied to other regions
- VPC peering to allow private traffic between regions
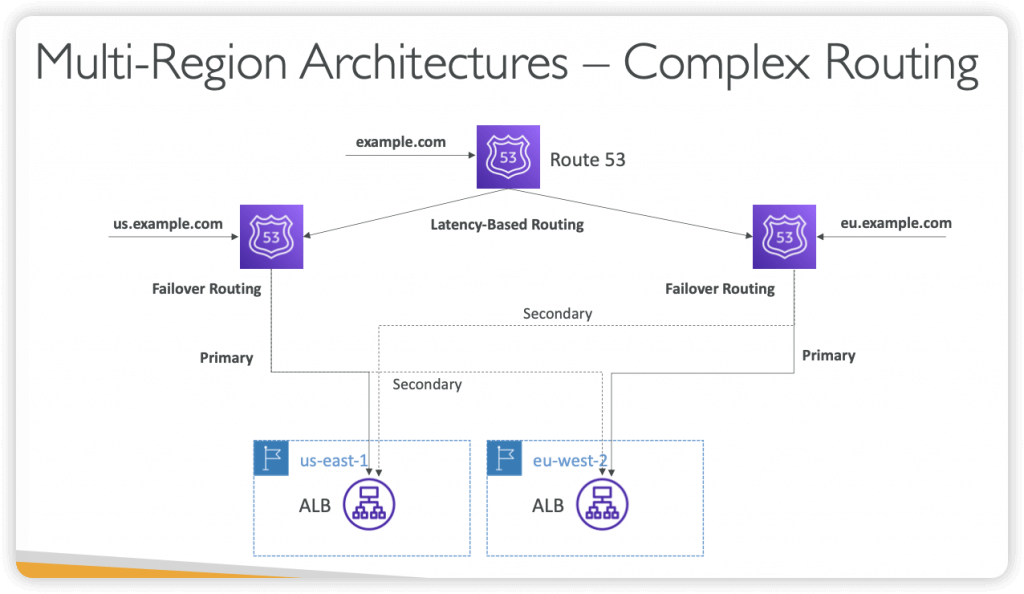
- Route53 uses a global network of DNS servers
- Health Check => automated DNS failovers:
- Health checks that monitor an endpoint (application, server, other AWS resource) Helpful to create a /health route
- Health checks that monitor other health checks (calculated health checks)
- Health checks that monitor CloudWatch alarms (full control !!) – e.g. throttles of DynamoDB, custom metrics, etc
- Health Checks are integrated with CW metrics
- Health Check => automated DNS failovers:
- S3 Cross Region Replication
- CloudFront for Global CDN at the Edge Locations
- Lambda@Edge for Global Lambda function at Edge Locations (A/B testing)
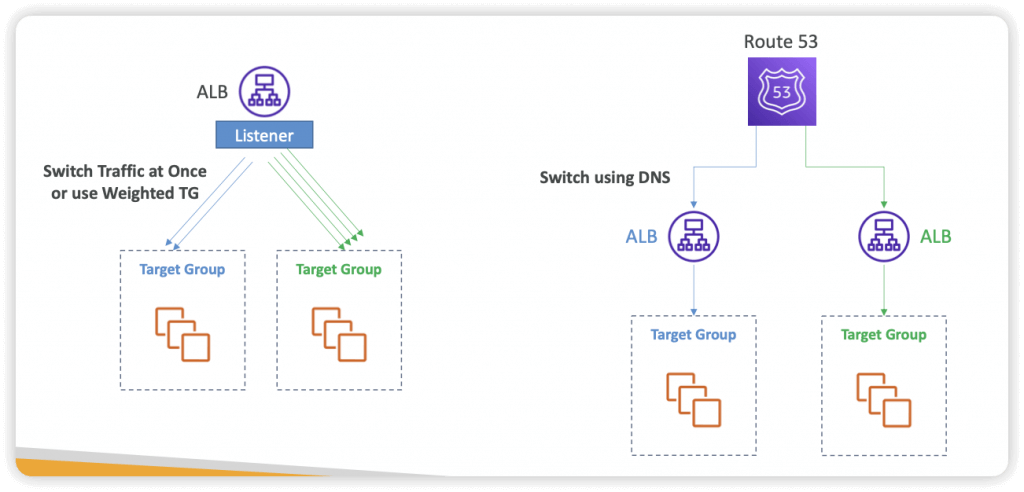
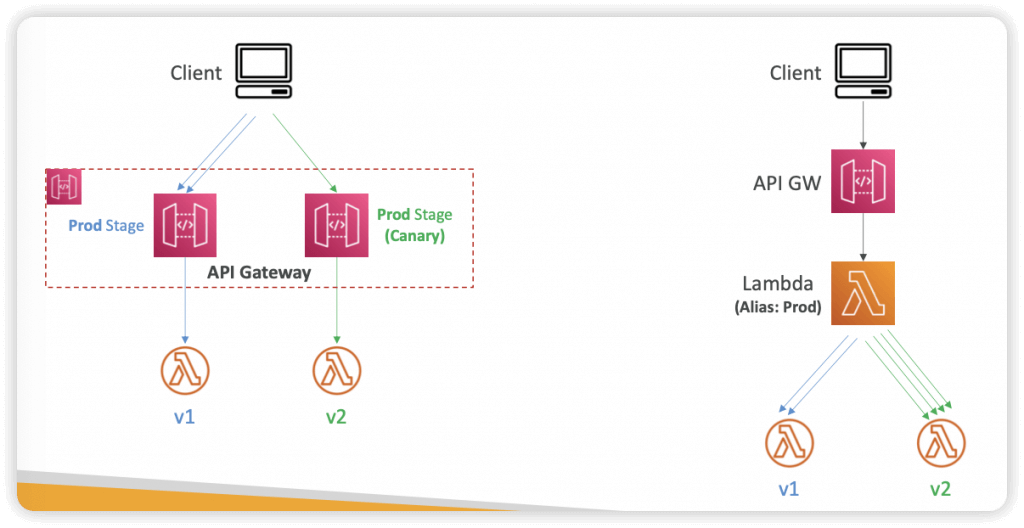
Blue-Green Architectures
- ALB
- Route 53
- API Gateway
- Lambda