== AUTHORISATION ==
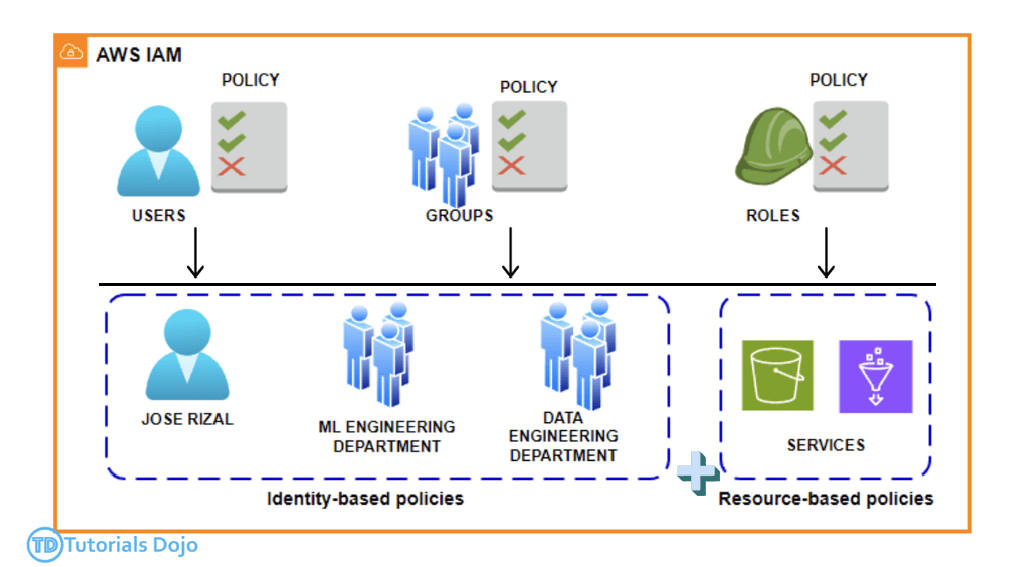
Identity and Access Management (IAM)
- Users (one physical user = one AWS user) and Groups (groups contain only users, no subgroups)
- The permissions boundary for an IAM entity (user or role) sets the max permissions that the entity can have
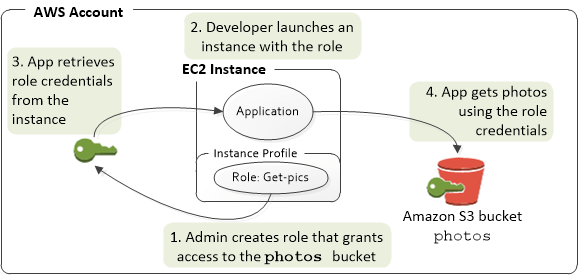
- IAM Role
- Roles hand out automatic credentials and permissions
- Giving permissions to non-humans, such as services / applications
- Giving permissions to federated / outside users & groups
- Authorisations from identity providers (like AWS Cognito) are mapped to your IAM role(s), NOT users or groups
- to pass the role to service, the users need to have iam:PassRole permission; to see, using iam:GetRole
- Roles can only passed to what their trust allows, using “Trust Relationships”
- Use Case: An IAM role is primarily used when one AWS resource or entity (such as an EC2 instance, Lambda function, or AWS service) needs to assume a set of permissions to interact with other AWS resources. The role itself doesn’t have credentials; instead, entities assume the role and inherit its permissions.
- vs “Resources Policies”
- Use Case: Resource policies are DIRECTLY attached to resources like S3 buckets, SNS topics, or SQS queues to specify which principals (AWS users, accounts, or services) can access them. These are directly associated with the resource, not a user or entity.”
- When you need to control access to a resource directly and specify which principals (IAM users, roles, services, or accounts) can access it.
- Roles hand out automatic credentials and permissions
- IAM Policies
- assign permissions, using JSON documents
- using “least privilege principle”
- consist of
- version
- id (optional)
- statement
- Sid (optional)
- Effect: Allow or Deny
- Principal: account/user/group/role
- Action: list of action, like S3:GetObject, S3:PutObject, iam:PassRole, iam:GetRole
- Resource: AWS resource
- Condition (optional)
- Permission Evaluation Flow
- If there’s explicit DENY, end flow with DENY
- Else, if there is an ALLOW, end flow with ALLOW
- Else, DENY
- Dynamic Policy, with variable as ${aws:username}
- Policy Management
- AWS Managed Policy
- Customer Managed Policy, has version control + rollback
- Inline Policy, strict 1-to-1 relationship with principal; would be also deleted while delete principal
- IAM Password Policy, set minimum length, require specific character types (number, upper/lower-case letters, non-alphabetic), expiration, and re-use forbidden
- Multi Factor Authentication (MFA)
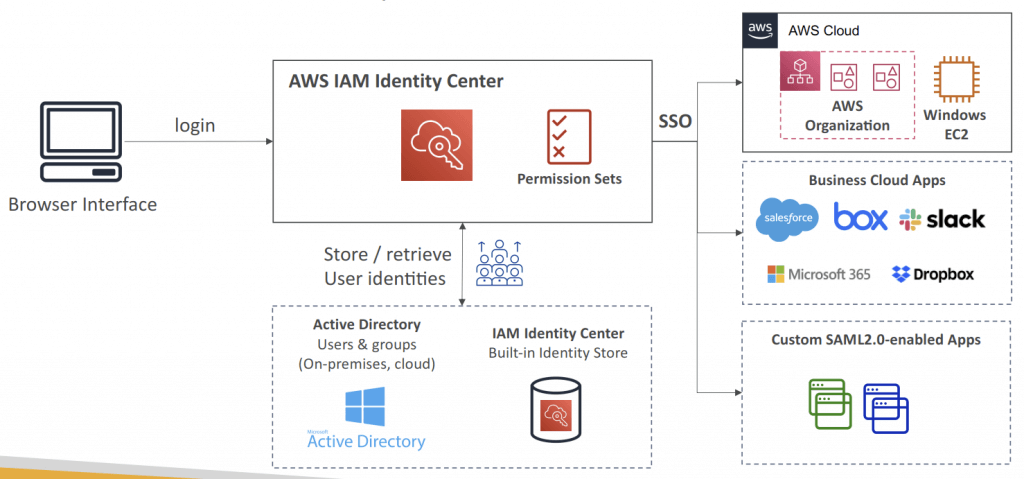
AWS IAM Identity Center
- successor to AWS Single Sign-On
- centralizes access management across AWS accounts and applications
- One login (single sign-on) for all your
- AWS accounts in AWS Organizations
- Business cloud applications (e.g., Salesforce, Box, Microsoft 365…)
- SAML2.0-enabled applications
- EC2 Windows Instances
- Identity providers
- Built-in identity store in IAM Identity Center
- 3rd party: Active Director y (AD), OneLogin, Okta…
- issues temporary security credentials for users to access AWS resources
- Fine-grained Permissions and Assignments
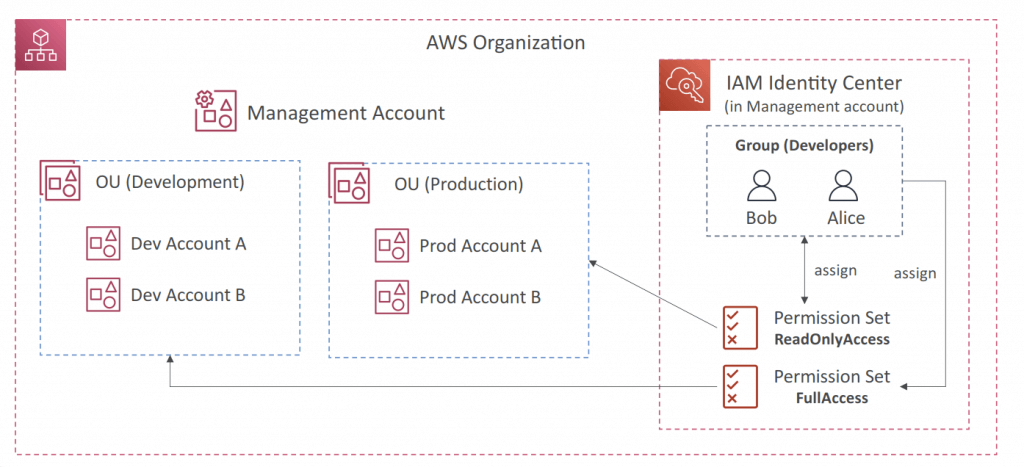
- Multi-Account Permissions
- Manage access across AWS accounts in your AWS Organization
- Permission Sets – a collection of one or more IAM Policies assigned to users and groups to define AWS access
- Application Assignments
- SSO access to many SAML 2.0 business applications (Salesforce, Box, Microsoft 365…)
- Provide required URLs, cer tificates, and metadata
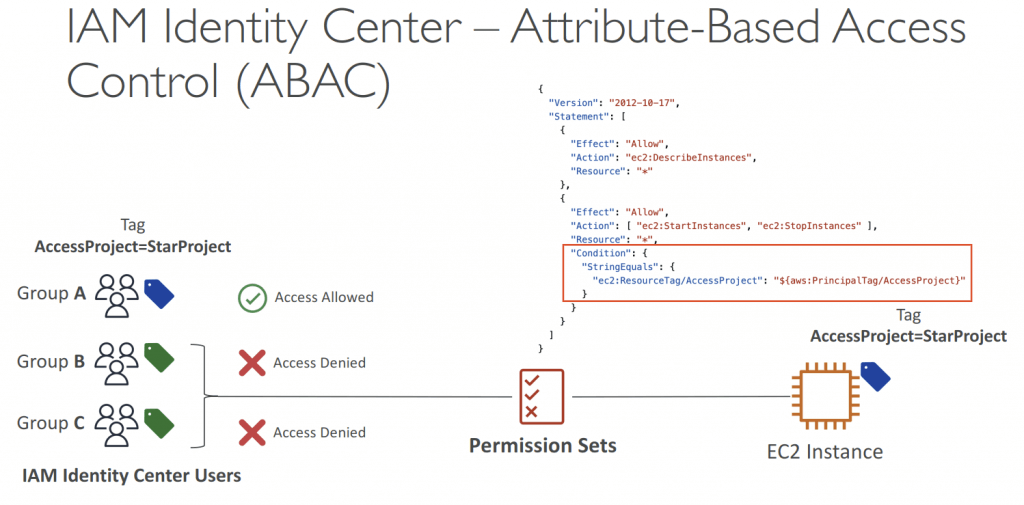
- Attribute-Based Access Control (ABAC)
- Fine-grained permissions based on users’ attributes stored in IAM Identity Center Identity Store
- Example: cost center, title, locale…
- Use case: Define permissions once, then modify AWS access by changing the attributes IAM
- User attributes are mapped from the IdP as key-value pairs
- Multi-Account Permissions
- External IdPs
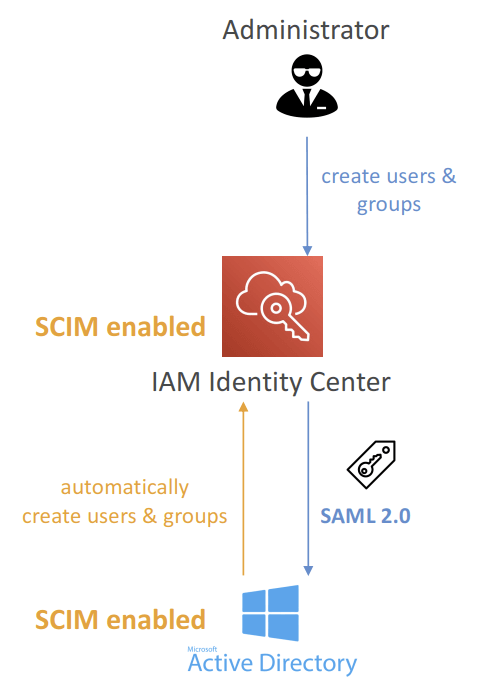
- SAML 2.0: authenticate identities from external IdP
- Users sign into AWS access por tal using their corporate identities
- Suppor ts Okta, Azure AD, OneLogin…
- SAML 2.0 does NOT provide a way to query the IdP to learn about users and groups
- You must create users and groups in the IAM Identity Center that are identical to the users and groups in the External IdP
- SCIM: automatic provisoning (synchronization) of user identities from an external IdP into IAM Identity Center
- SCIM = System for Cross-domain Identity Management
- Must be supported by the external IdP
- Perfect complement to using SAML 2.0
- SAML 2.0: authenticate identities from external IdP
- Multi-Factor Authentication (MFA)
- Every Time They Sign-in (Always-on)
- Only When Their Sign-in Context Changes (Context-aware) – analyzes user behavior (e.g., device, browser, location…)
IAM Security/Audit Tools
- IAM Credentials Report (account-lv)
- IAM Access Advisor (user-lv), for check/revise the permissions granted with usage
- IAM Policy Simulator evaluates the policies that you choose and determines the effective permissions for each of the actions that you specify
AWS STS (Security Token Service)
- request temporary limited-privilege (15mins to 1 hour) credentials for IAM users, or for users that you authenticate such as federated users from an on-prem directory
- APIs
- AssumeRole
- AssumeRoleWithSAML
- AssumeRoleWithWebIdentity -> using Cognito Identity Pools instead
- GetSessionToken, for MFA (returns “Access ID”, “Secret Key”, “Session Token”, and “Expiration Date”)
- GetFederationToken
- GetCallerIdentity
- DecodeAuthorizationMessage
- STS for MFA, needs
- using GetSessionToke api
- in IAM Policy, need set in Conditions (in statement), as “aws:MultiFactorAuthPresent:true”
- Federation: STS can be used Federation (typically with Azure AD). It uses SAML 2.0 for authentication to grant temporary access based on the AD creds
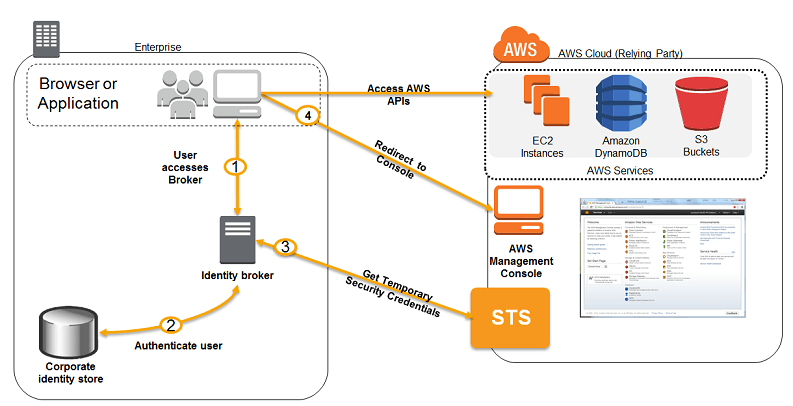
- Single Sign-On: STS can be used to develop a custom identity broker for SSO to a service such as the AWS management console:
- Verify that the user is authenticated on the local IDP (AD)
- Call STS AssumeRole or GetFederationToken API to get temp credentials
- Pass the temp creds to AWS federation endpoint to request a sign-in token
- Construct a URL to the service that includes the token which can be provided to the user
For On-Premier applications
- Applications running outside of an AWS environment will need access keys for programmatic access to AWS resources. For example, monitoring tools running on-premises and third-party automation tools will need access keys.
- However, if the resources that need programmatic access are running inside AWS, the best practice is to use IAM roles instead. An IAM role is a defined set of permissions—it’s not associated with a specific user or group. Instead, any trusted entity can assume the role to perform a specific business task.
- Access keys are long-term credentials for an IAM user or the AWS account root user. You can use access keys to sign programmatic requests to the AWS CLI or AWS API (directly or using the AWS SDK).
- In order to use the AWS SDK for your application, you have to create your credentials file first at ~/.aws/credentials for Linux servers or at C:\Users\USER_NAME\.aws\credentials for Windows users and then save your access keys.
== CERTIFICATE & KEYS ==
AWS Certificate Manager (ACM)
- manage SSL/TLS certificates, for in-flight encryption of websites (HTTPS)
- SSL refers to Secure Sockets Layer, used to encrypt connections
- TLS refers to Transport Layer Security, which is a newer version
- automatically renewal
- Elastic Load Balancers(Application Load Balancer & Network Load Balancer), CloudFront Distributions, API Gateway Calls
- Public and Private
AWS Private Certificate Authority (CA)
- including root and subordinaries certificates (X.509), trusted by only private Organisation
Encryption
- Best practice is to lock away or delete the root user access keys. Never store in an S3 bucket, even if encrypted
- Never ever store your secrets in plaintext, especially in your code!
- Encryption in flight
- SSL/TLS is for encrypting data in transit, not data at rest.
- SSL/TLS is synonymous with HTTPS traffic. It goes over port 443.
- Server-side encryption at rest
- Data is encrypted after being received by the server, and decrypted before being sent
- So the data stored is in an encrypted from
- Types
- SSE-C: use customer-provided keys and manage them yourself
- SSE-S3, SSE-SQS, SSE-DDB: Amazon manages the keys
- SSE-KMS: keys are managed in Amazon Key Management Service
- CloudHSM: generate and use your own encryption keys, held in the cloud in Amazon’s HSM
- Client-side encryption
- Data stored is also in an encrypted from
- but the is encrypted before sending to the server, and decrypted in client side after being received
AWS Key Management Service (KMS)
- AWS manages encryption keys for us
- Fully integrated with IAM for authorization
- Able to audit KMS Key usage using CloudTrail
- KMS Keys is the new name of KMS Customer Master Key (KMS CMK)
- Symmetric (AES-256 keys)
- AWS services default
- must call KMS API
- encrypt up to 4 KB of data through KMS
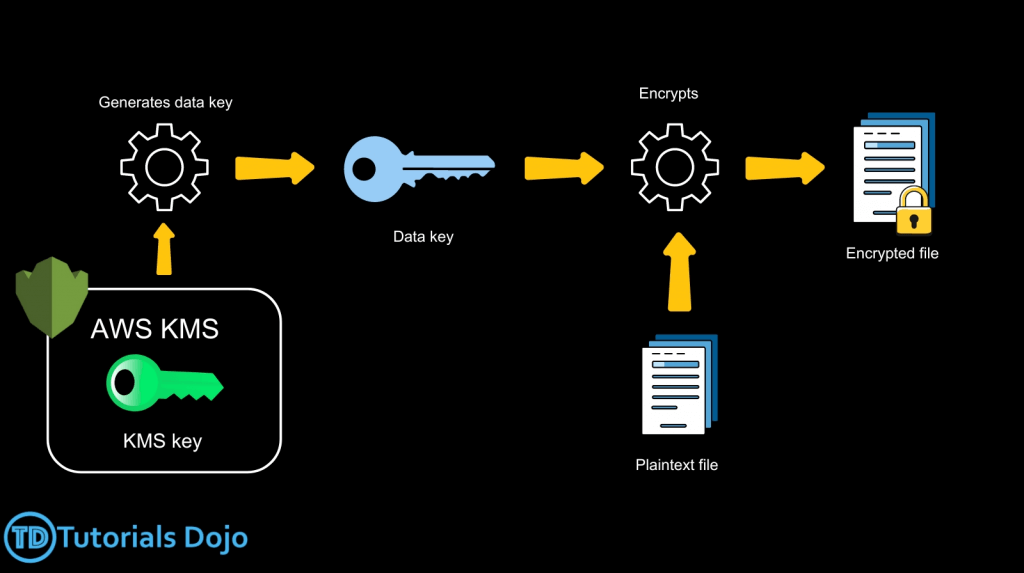
- to encrypt > 4KB with KMS Encrypt API call, need to use Envelope Encryption (aka GenerateDataKey API), let client side to Encrypt/Decrypt with DEK received
- GenerateDataKey: generates a unique symmetric data key (DEK)
- returns a plaintext copy of the data key
- AND a copy that is encrypted under the CMK
- GenerateDataKeyWithoutPlaintext
- Generate a DEK that is encrypted under the CMK
- Decrypt: decrypt up to 4 KB of data (also “Data Encryption Keys”)
- GenerateRandom: Returns a random byte string
- Encrypt data locally in your application (ie, Envelope Encryption) with KMS
- Use the GenerateDataKey operation to get a data encryption key.
- Use the plaintext data key (returned in the Plaintext field of the response) to encrypt data locally, then erase the plaintext data key from memory.
- Store the encrypted data key (returned in the CiphertextBlob field of the response) alongside the locally encrypted data.
- To Decrypt data locally:
- Use the Decrypt operation to decrypt the encrypted data key. The operation returns a plaintext copy of the data key.
- Use the plaintext data key to decrypt data locally, then erase the plaintext data key from memory.
- Envelope encryption is the practice of “encrypting plaintext data with a data key and then encrypting the data key under another key”. But, eventually, one key must remain in plaintext so you can decrypt the keys and your data. This top-level plaintext encryption key is known as the root key.
- GenerateDataKey: generates a unique symmetric data key (DEK)
- Asymmetric (RSA & ECC key pairs)
- Public (Encrypt) and Private Key (Decrypt) pair
- Symmetric (AES-256 keys)
- Types of KMS Keys
- AWS Owned Keys (free): SSE-S3, SSE-SQS, SSE-DDB (DynamoDB)
- AWS Managed Key (free): aws/service-name, automatic renew every 1 year
- Customer managed keys created in KMS: $1 / month, can be renewed automatic & on-demand
- Customer managed keys imported: $1 / month, only manual rotation
- AWS Encryption SDK has already implemented Envelope Encryption
- the feature – Data Key Caching, can reuse the data keys, with LocalCryptoMaterialsCache
- Request Quotas: if got ThrottlingException, use exponential backoff (backoff and retry); and all cryptographic operations (aka Encrypt and Decrypt), they share a quota
- To hugely reduce the cost on S3 encryption, use “S3 Bucket Key”
CloudHSM
- Compared with KMS, AWS provisions encryption with dedicated hardware (HSM = Hardware Security Module)
- Encryption keys are managed on client side
- Good option to use with SSE-C encryption
- CloudHSM clusters are spread across Multi AZ (HA)
AWS System Manager (SSM) Parameter Store
- Secure storage for configuration and secrets
- Version tracking of configurations / secrets
- Allow to assign a TTL to a parameter (expiration date) to force updating or deleting sensitive data such as passwords
- Parameter policies are only available for parameters in the Advanced tier
- Expiration – deletes the parameter at a specific date
- ExpirationNotification – sends an event to Amazon EventBridge (Amazon CloudWatch Events) when the specified expiration time is reached.
- NoChangeNotification – sends an event to Amazon EventBridge (Amazon CloudWatch Events) when a parameter has not been modified for a specified period of time.
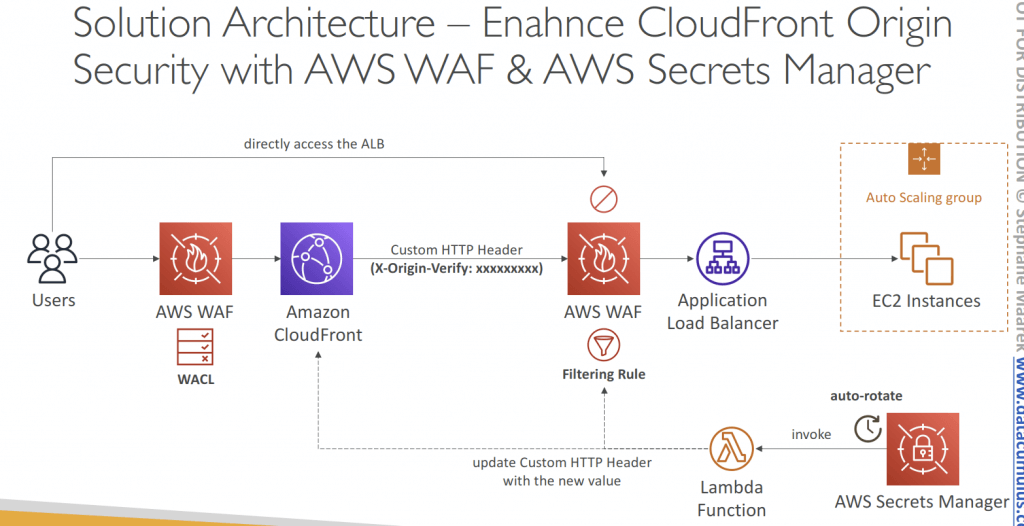
AWS Secrets Manager
- Capability to force rotation of secrets every X days
- Automate generation of secrets on rotation (uses Lambda)
- Integration with Amazon RDS (MySQL, PostgreSQL, Aurora)
- Secrets are encrypted using KMS
- Mostly meant for RDS integration
- Multi-Region Secrets
- Replicate Secrets across multiple AWS Regions
- Secrets Manager keeps read replicas in sync with the primary Secret
- Ability to promote a read replica Secret to a standalone Secret
- Use cases: multi-region apps, disaster recovery strategies, multi-region DB…
== AUTHENTICATION ==
Amazon Cognito
- authentication for users with identity for mobile and web application
- Benefit over IAM: “hundreds of users”, “mobile users” and “authenticate with SAML”
- Cognito User Pools (CUP)
- Authentication, Identity Verification
- Provide sign-in functionality for user
- A serverless database of “User”
- Simple Login (User name/email + Password)
- Password Recovery
- Email/Phone verification
- Multi-Factor authentication (MFA)
- Federated identities with 3rd parties, Google/FB/SAML/OpenID, etc.
- JWT(JSON Web Token) for login send backs
- Integrated with API Gateway & Application Load Balancer
- Lambda Triggers
- Authentication Events (Sign-In)
- Sign-Up
- Messages
- Token Creation
- Hosted Authentication UI & Custom Domain
- ACM certificate in “us-east-1”
- must defined in the “App Integration” section
- Adaptive
- using risk score for each attempt; finally block or requires (second) MFA for suspicious logins
- Integrated with CloudWatch Logs
- JSON Web Token
- Base64 encoded
- Header, Payload(contains “sub”-UUID, email, phone, user name, etc.), and Signature
- Authenicate Users on Application Load Balancer
- Offload the authentication from applications to load balancer
- Identity Provider (IdP): OpenID Connect compliant
- AWS Cognito User Pools
- Set up HTTPS listeners with “authenticate-oidc” or “authenticate-cognito” rules
- OnUnauthenticatedRequest – authenticate(default), deny, allow
- Cognito Identity Pools (CIP)
- Authorisation, Access Control
- Federated Identities
- Temporary AWS credentials to AWS resources directly (or via API Gateway)
- IAM policies via Security Token Service (STS), at least one “trust” policy
- can be customised based on the user_id
- Identity pool/sources
- Public 3rd Parties (Google, Facebook, Apple, etc.)
- OpenID Connect & SAML
- AWS Cognito User Pools
- Developer Authenticated Identities (custom Login server)
- unauthenicate (guess) access
- can partition users with IAM policy “variables”
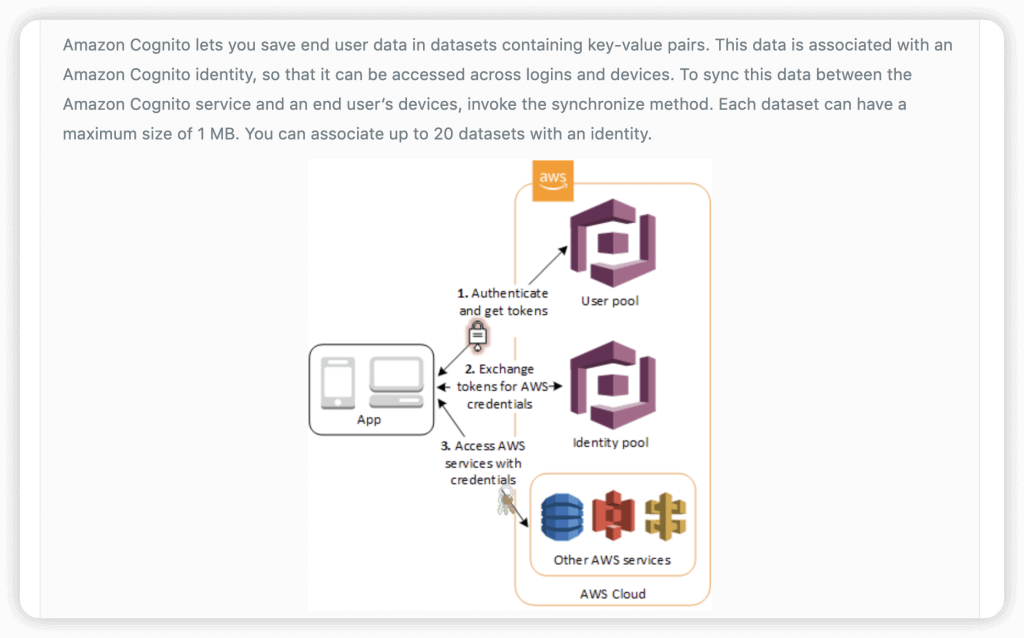
- Amazon Cognito Sync is an AWS service and client library that enables cross-device syncing of application-related user data.
AWS Directory Services
- for MS Active Directory (AD), with AD Domain Services
- AWS Managed Microsoft AD
- an AD instance on AWS, connecting as “trust” with on-premise AD; users are managed on AWS locally; support MFA
- AD Connector
- as (Directory Gateway) proxy only, using on-premise AD to manage; support MFA
- Simple AD
- a seperate AD on AWS, no connection with on-premise AD
- AWS Managed Microsoft AD
== SECURITY ==
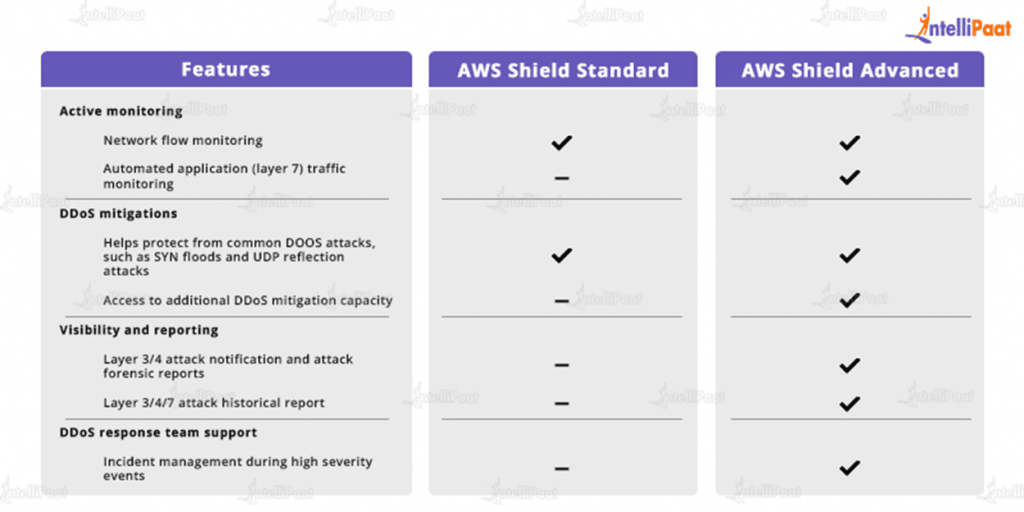
AWS Shield & Shield Advanced
- Protection against Distributed Denial of Service (DDoS)
AWS Web Application Firewall (WAF)
- Allow all requests except the ones that you specify
- Block all requests except the ones that you specify
- Count the requests that match the properties that you specify
- Protects your web applications from common web exploits (Layer 7)
- Deploy on Application Load Balancer (localized rules)
- Deploy on API Gateway (rules running at the regional or edge level)
- Deploy on CloudFront (rules globally on edge locations)
- Used to front other solutions: CLB, EC2 instances, custom origins, S3 websites
- Deploy on AppSync (protect your GraphQL APIs)
- Also for Cognito user pool, App Runner, Verified Access, and Amplify
- WAF is not for DDoS protection
- Define Web ACL (Web Access Control List, WACL):
- Rules can include IP addresses, HTTP headers, HTTP body, or URI strings
- Protects from common attack – SQL injection and Cross-Site Scripting (XSS)
- Size constraints, Geo match
- Rate-based rules (to count occurrences of events)
- Logging
- Amazon CloudWatch Logs log group – 5 MB per second
- Amazon Simple Storage Service (Amazon S3) bucket – 5 minutes interval
- Amazon Kinesis Data Firehose – limited by Firehose quotas
- Rule Actions: Count | Allow | Block | CAPTCHA | Challenge
- Baseline Rule Groups – general protection from common threats
- AWSManagedRulesCommonRuleSet, AWSManagedRulesAdminProtectionRuleSet…
- Use-case Specific Rule Groups – protection for many AWS WAF use cases
- AWSManagedRulesSQLiRuleSet, AWSManagedRulesWindowsRuleSet, AWSManagedRulesPHPRuleSet, AWSManagedRulesWordPressRuleSet…
- IP Reputation Rule Groups – block requests based on source (e.g., malicious IPs)
- AWSManagedRulesAmazonIpReputationList, AWSManagedRulesAnonymousIpList
- Bot Control Managed Rule Group – block and manage requests from bots
- AWSManagedRulesBotControlRuleSet
AWS Firewall Manager
- simplifies your AWS WAF and AWS Shield Advanced administration and maintenance tasks across multiple accounts and resources.
- Manage rules in all accounts of an AWS Organization
- Security policy:
- Policies are created at the region level
- WAF rules (Application Load Balancer, API Gateways, CloudFront)
- Enforce applying WebACLs to all ALBs in all accounts in AWS Organization
- Identify resources that don’t comply, but don’t auto remediate: create the
WebACL in each account without applying the WebACL to any resources - Auto remediate any noncompliant resources: automatically apply the
WebACLs to existing resources
- AWS Shield Advanced (ALB, CLB, NLB, Elastic IP, CloudFront)
- Enforce Shield Advanced protections in all accounts in AWS Organization
- Option to view only compliance (to assess impact) or auto remediate
- Security Groups for EC2, Application Load Balancer and ENI resources in VPC
- Common Security Groups
- Enforce applying SGs to all EC2 instances in all accounts in AWS Organization
- Auditing of Security Group Policy
- Check and manage SGs Rules in all accounts in AWS Organization
- Usage Audit Security Group Policy
- Monitor unused and redundant SGs and optionally perform cleanup
- Common Security Groups
- AWS Network Firewall (VPC Level)
- Centrally manage Network Firewall firewalls in all accounts in AWS Organization
- Distributed – creates and maintains firewall endpoint in each VPC
- Centralized – creates and maintains firewall endpoint in a centralized VPC
- Import Existing Firewalls – import existing firewalls using Resource Sets
- Amazon Route 53 Resolver DNS Firewall
- Manage associations between Resolver DNS Firewall Rule Groups and VPCs in all accounts in AWS Organization
- Rules are applied to new resources as they are created (good for compliance) across all and future accounts in your Organization
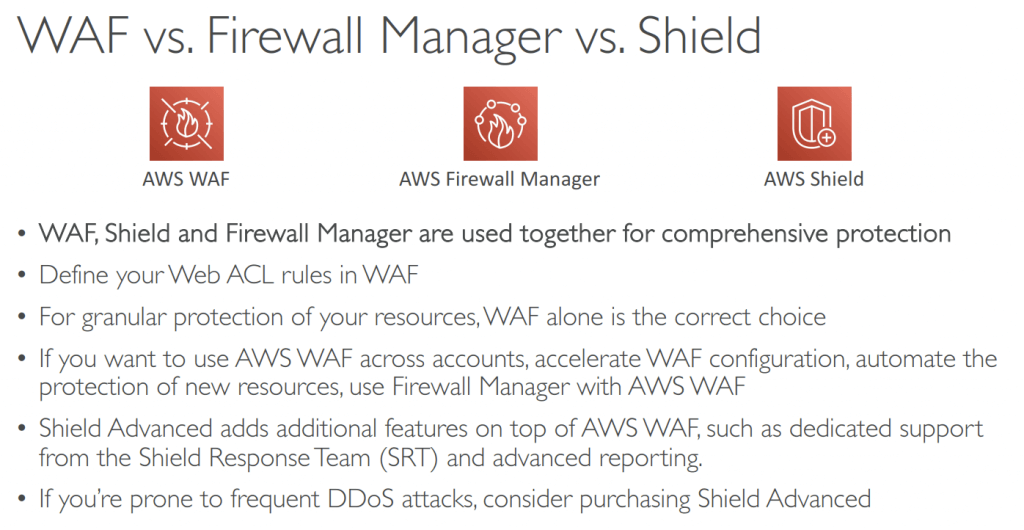
| Type | AWS WAF | AWS Shield |
| Operation OSI Layer | Operates in Application Layer (layer 7) | If you choose Shield Advanced, it will function in the Network Layer (Layer 3), Transport Layer (Layer 4), and Application Layer (Layer 7). |
| Use-case | Protects against web attacks like Cross-site Scripting, DDoS, SQL injection, etc. | It protects mainly against DDoS |
| Pricing | You have to pay for using AWS WAS, although initially, it’s free. | In AWS Shield, Shield Standard works with no additional cost whereas with Shield Advanced you have to pay as you use. |
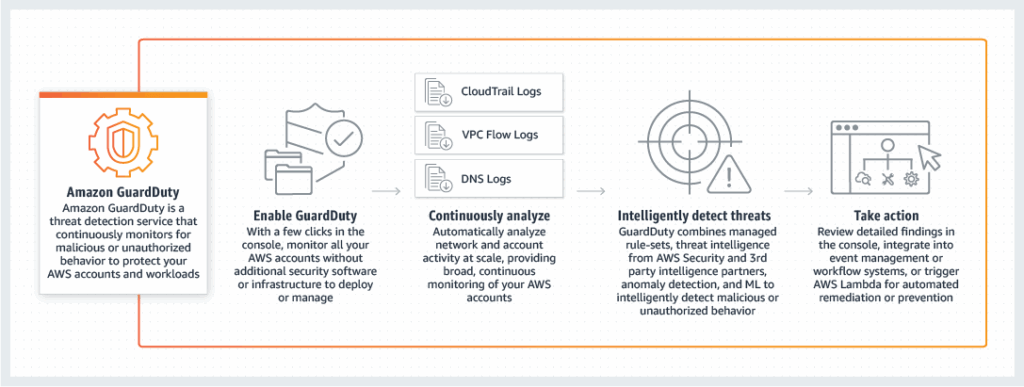
Amazon GuardDuty
- GuardDuty is a threat detection service that continuously monitors for malicious activity and unauthorized behavior in your AWS environment.
- Threat Detection – Utilizes machine learning and anomaly detection to identify potentially malicious activity such as unauthorized access, data exfiltration, or compromised instances.
- Security Findings: Provides detailed security findings with severity levels and recommendations for remediation.
- Automated Response: Can be configured to automatically trigger responses or notifications based on detected threats.
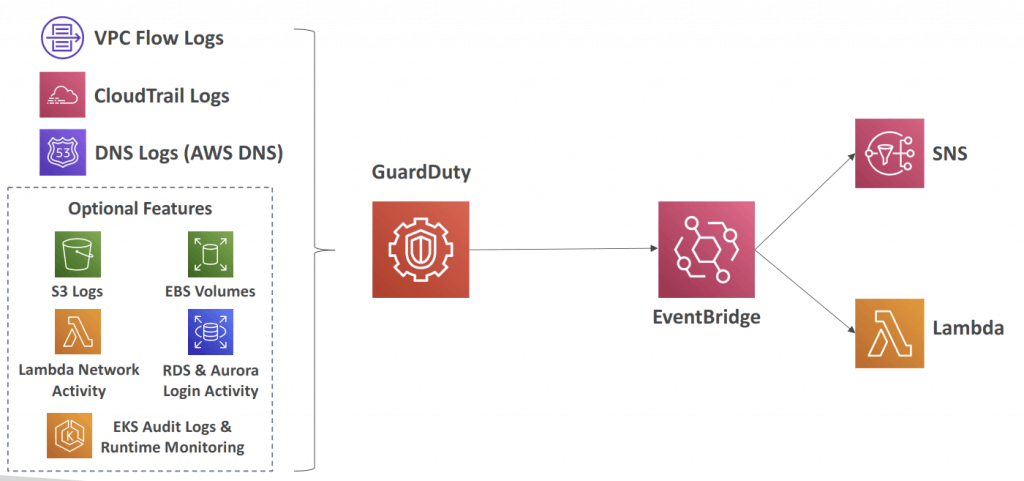
- Input data includes:
- CloudTrail Events Logs – unusual API calls, unauthorized deployments
- CloudTrail Management Events – create VPC subnet, create trail, …
- CloudTrail S3 Data Events – get object, list objects, delete object, …
- VPC Flow Logs – unusual internal traffic, unusual IP address
- DNS Logs – compromised EC2 instances sending encoded data within DNS queries
- Optional Feature – EKS Audit Logs, RDS & Aurora, EBS, Lambda, S3 Data Events…
- CloudTrail Events Logs – unusual API calls, unauthorized deployments
- Can setup EventBridge rules to be notified in case of findings
- EventBridge rules can target AWS Lambda or SNS
- Can protect against CryptoCurrency attacks (has a dedicated “finding” for it)
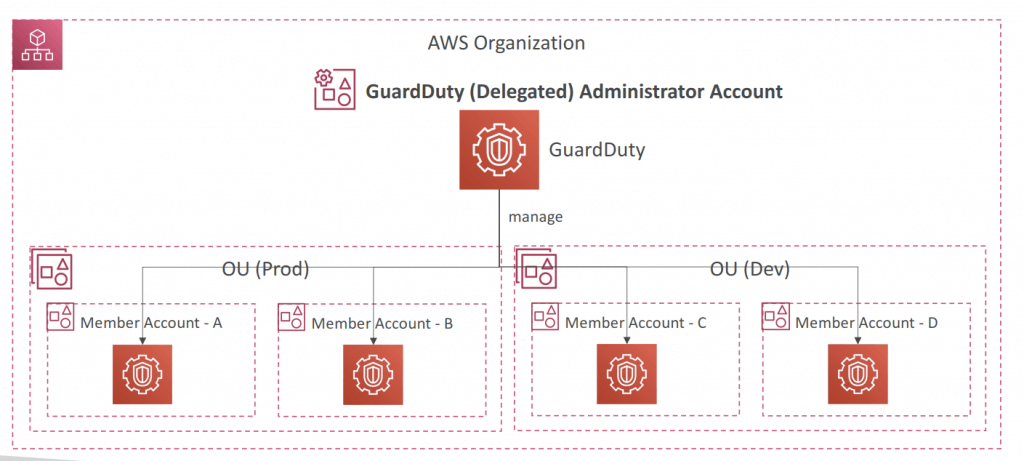
- Multi-Account Strategy
- Associate the Member accounts with the Administrator account
- Through an AWS Organization
- Sending invitation through GuardDuty
- Administrator account can:
- Add and remove member accounts
- Manage GuardDuty within the associated member accounts
- Manage findings, suppression rules, trusted IP lists, threat lists
- In an AWS Organization, you can specify a member account as the Organization’s delegated administrator for GuardDuty
- Associate the Member accounts with the Administrator account
- Findings
- Findings are potential security issue for malicious events happening in your AWS account
- GuardDuty pulls independent streams of data directly from CloudTrail logs (management events, data events), VPC Flow Logs or EKS logs
- Each finding has a severity value between 0.1 to 8+ (High, Medium, Low)
- Finding naming convention
ThreatPurpose:ResourceTypeAffected/ThreatFamilyName.DetectionMechanism!Artifact- ThreatPurpose – primary purpose of the threat (e.g., Backdoor, CryptoCurrency)
- ResourceTypeAffected – which AWS resource is the target (e.g., EC2, S3)
- ThreatFamilyName – describes the potential malicious activity (e.g., NetworkPortUnusual)
- DetectionMechanism – method GuardDuty detecting the finding (e.g., Tcp, Udp)
- Artifact – describes a resource that is used in the malicious activity (e.g., DNS)
- You can generate sample findings in GuardDuty to test your automations
- Findings Types
- EC2 Finding Types
- UnauthorizedAccess:EC2/SSHBruteForce, CryptoCurrency:EC2/BitcoinToo.B!DNS
- IAM Finding Types
- Stealth:IAMUser/CloudTrailLoggingDisabled, Policy:IAMUser/RootCredentialUsage
- Kubernetes Audit Logs Finding Types
- CredentialAccess:Kubernetes/MaliciousIPCaller
- Malware Protection Finding Types
- Execution:EC2/SuspiciousFile, Execution:ECS/ SuspiciousFile
- RDS Protection Finding Types
- CredentialAccess:RDS/AnomalousBehavior.SuccessfulLogin
- S3 Finding Types
- Policy:S3/AccountBlockPublicAccessDisabled, PenTest:S3/KaliLinux
- EC2 Finding Types
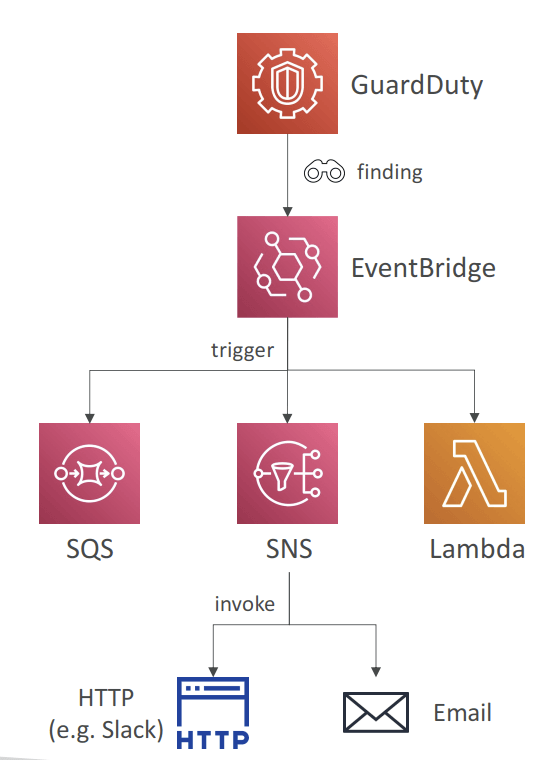
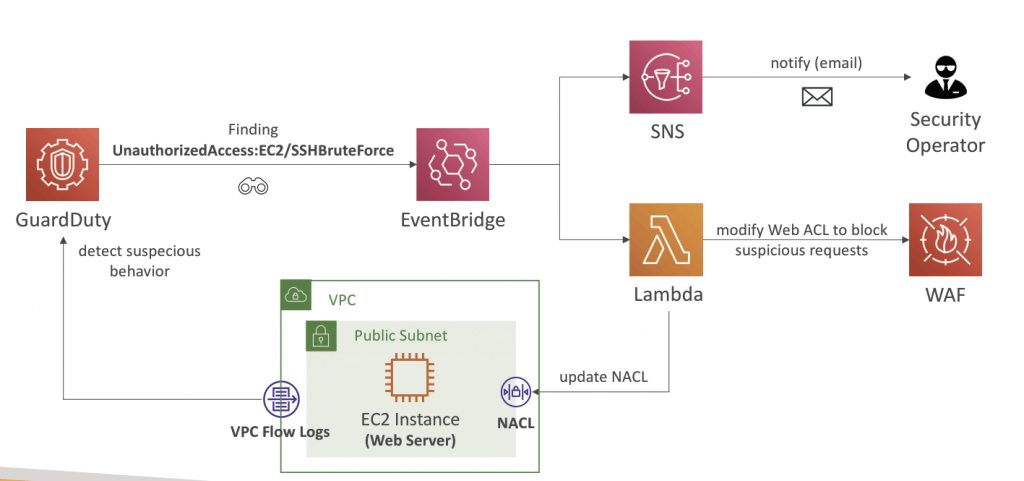
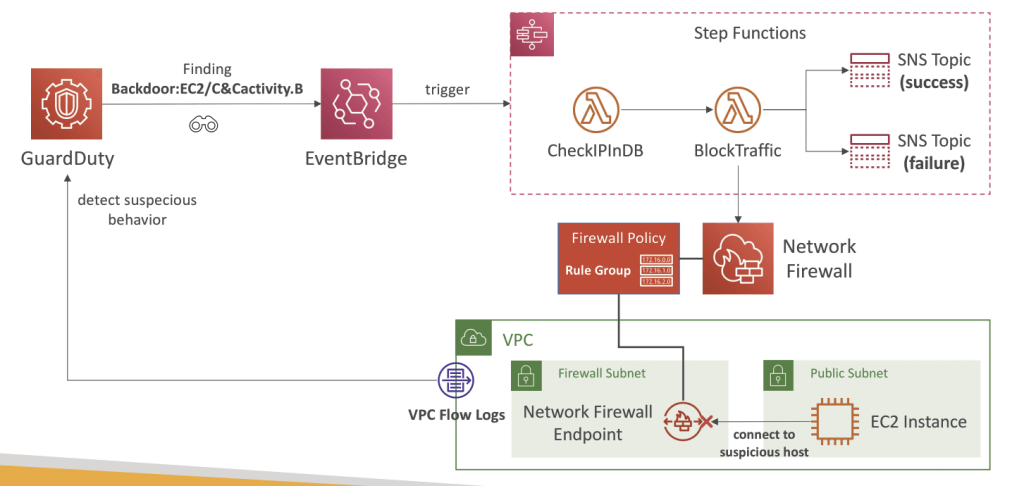
- Findings Automated Response
- Automate response to security issues revealed by GuardDuty Findings using EventBridge
- Send alerts to SNS (email, Lambda, Slack, Chime…)
- Events are published to both the administrator account and the member account that it is originated from
- Trusted and Threat IP Lists
- Works only for public IP addresses
- Trusted IP List
- List of IP addresses and CIDR ranges that you trust
- GuardDuty doesn’t generate findings for these trusted lists
- Threat IP List
- List of known malicious IP addresses and CIDR ranges
- GuardDuty generates findings based on these threat lists
- Can be supplied by 3rd party threat intelligence or created custom for you
- In a multi-account GuardDuty setup, only the GuardDuty administrator account can manage those lists
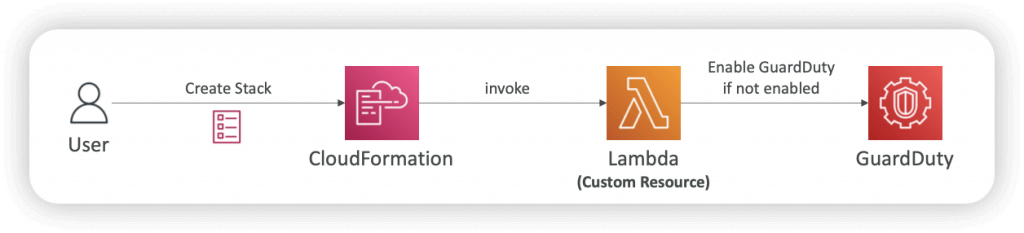
- CloudFormation
- You can enable GuardDuty by using Custom Resource (Lambda) in a CloudFormation template
- If GuardDuty is already enabled, the CloudFormation Stack deployment fails
- Deploy across all the Organization using a Stack Set
Amazon Macie
- discover and protect sensitive data (Personal Identifiable Information, PII) by machine learning and pattern matching, on S3 bucket
- Data Discovery – Automatically scans and classifies data stored in Amazon S3 buckets to identify sensitive data such as personally identifiable information (PII) or intellectual property.
- Data Classification – Assigns sensitivity labels to data based on its content and context, helping you understand the level of risk associated with different types of data.
- Security Monitoring – Continuously monitors data access and usage patterns to detect suspicious or unauthorized behavior, such as unusual access patterns or data leaks.
- Compliance Reporting – Provides reports and dashboards to help you demonstrate compliance with data protection regulations such as GDPR, HIPAA, or PCI DSS.
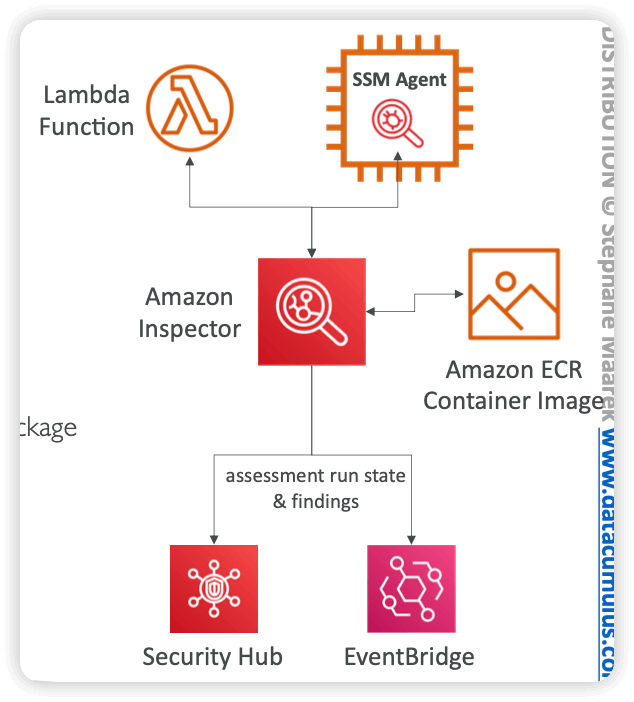
AWS Inspector
- “primarily used to help you check for unintended network accessibility of your Amazon EC2 instances and for vulnerabilities on those EC2 instances.”
- an automated security assessment service
- Continuous scanning of the infrastructure, only when needed
- Looking after
- Package vulnerabilities (EC2, ECR & Lambda) – database of CVE
- Network reachability (EC2)
- A risk score is associated with all vulnerabilities for prioritization
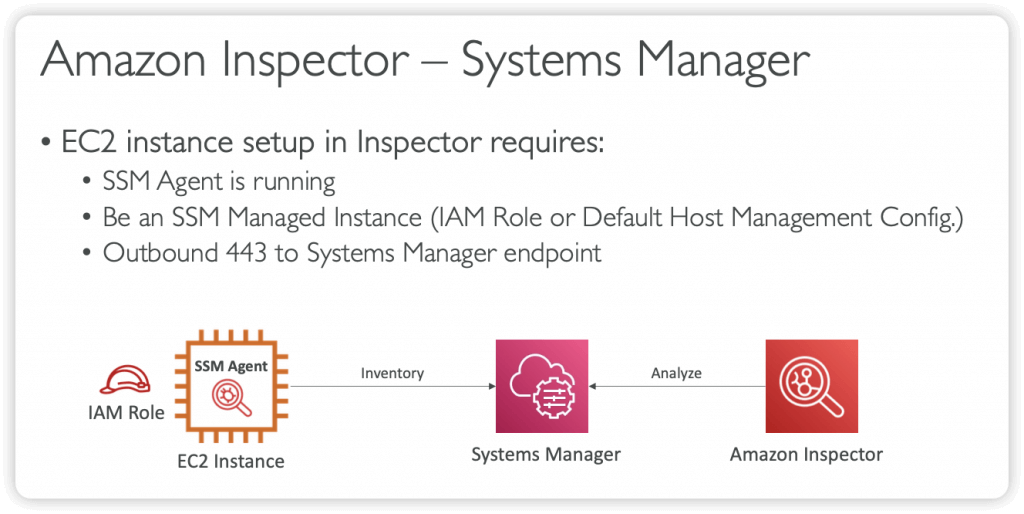
- For EC2 instances
- Leveraging the AWS System Manager (SSM) agent
- Analyze against unintended network accessibility
- Analyze the running OS against known vulnerabilities
- EC2 instance setup requires:
- SSM Agent is running
- Be an SSM Managed Instance (IAM Role or Default Host Management Config.)
- Outbound 443 to Systems Manager endpoint
- For Container Images push to Amazon ECR
- Assessment of Container Images as they are pushed
- For Lambda Functions
- Identifies software vulnerabilities in function code and package dependencies
- Assessment of functions as they are deployed assessment run state & findings
- Reporting & integration with AWS Security Hub
- Send findings to Amazon Event Bridge
AWS Security Hub
- acts as a centralized dashboard for your cloud security. Think of it as the control tower of your cloud environment, where you can monitor security findings, compliance checks, and trends across multiple AWS accounts and regions.It aggregates and organizes security alerts (findings) from various AWS services like GuardDuty, Inspector, Macie, and third-party tools into a single view. Additionally, it performs automated security checks against industry standards like CIS Benchmarks, PCI DSS, and NIST to help you maintain compliance.
- Key Features
- Centralized View: Aggregates findings from multiple sources into one place.
- Security Standards Compliance: Continuously checks your environment against best practices and compliance frameworks.
- Automated Insights: Generates insights to prioritize issues based on severity.
- Integration with Other Tools: Works with AWS services (e.g., GuardDuty) and third-party solutions.
- Automation: Supports automated remediation using Amazon EventBridge.
AWS Detective
- GuardDuty, Macie, and Security Hub are used to identify potential security issues, or findings
- Sometimes security findings require deeper analysis to isolate the root cause and take action – it’s a complex process
- Amazon Detective analyzes, investigates, and quickly identifies the root cause of security issues or suspicious activities using ML and graphs
- Automatically collects and processes events from VPC Flow Logs, CloudTrail, and GuardDuty to create a unified view
- Produces visualizations with details and context to get to the root cause
- Amazon Detective helps you analyze, investigate, and quickly identify the root cause of security findings or suspicious activities. Detective automatically collects log data from your AWS resources. It then uses machine learning, statistical analysis, and graph theory to generate visualizations that help you to conduct faster and more efficient security investigations. The Detective prebuilt data aggregations, summaries, and context help you to quickly analyze and determine the nature and extent of possible security issues.
- With Detective, you can access up to a year of historical event data. This data is available through a set of visualizations that show changes in the type and volume of activity over a selected time window. Detective links these changes to GuardDuty findings.
== COMPLIANCE ==
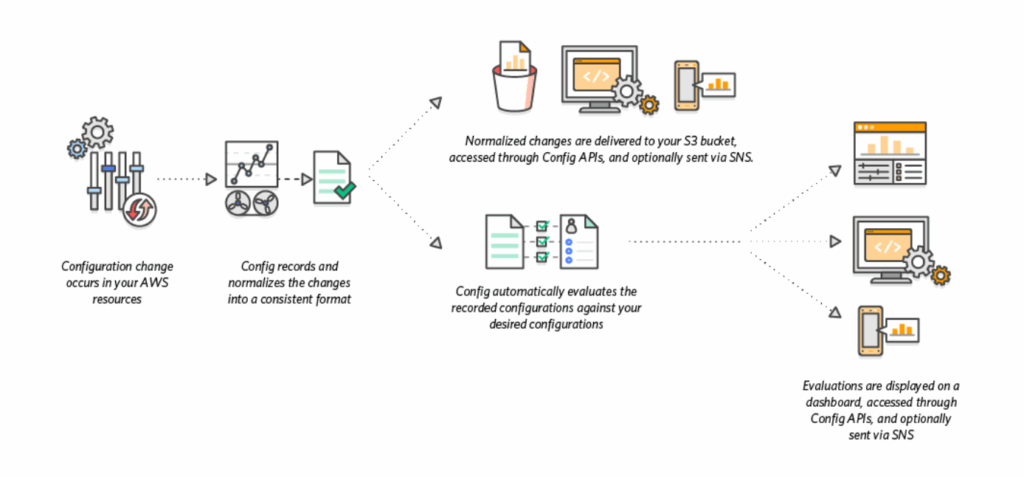
AWS Config
- auditing and recording compliance of your AWS resources
- tracks resource inventory, config history and config change notifications for the purpose of security and compliance. Assess, audit and evaluate the configurations of AWS resources.
- Questions that can be solved by AWS Config:
- Is there unrestricted SSH access to my security groups?
- Do my buckets have any public access?
- How has my ALB configuration changed over time?
- You can receive alerts (SNS notifications) for any changes
- AWS Config is a per-region service
- Can be aggregated across regions and accounts
- Possibility of storing the configuration data into S3 (analyzed by Athena)
- Config Rules
- AWS managed config rules
- custom config rules (must be defined in AWS Lambda)
- Rules can be evaluated / triggered
- Upon config change
- and/or: at regular time intervals
- AWS Config Rules does not prevent actions from happening (no deny)
- Configuration Recorder
- Stores the configurations of your AWS resources as Configuration Items
- Configuration Item – a point-in-time view of the various attributes of an AWS resource. Created
whenever AWS Config detects a change to the resource (e.g., attributes, relationships, config.,
events…) - Custom Configuration Recorder to record only the resource types that you specify
- Must be created before AWS Config can track your resources (created automatically when you enable AWS Config using AWS CLI or AWS Console)
- Remediations
- Automate remediation of non-compliant resources using SSM Automation Documents
- Use AWS-Managed Automation Documents or create custom Automation Documents
- Tip: you can create custom Automation Documents that invokes Lambda function
- You can set Remediation Retries if the resource is still non-compliant after auto-remediation
- Notifications
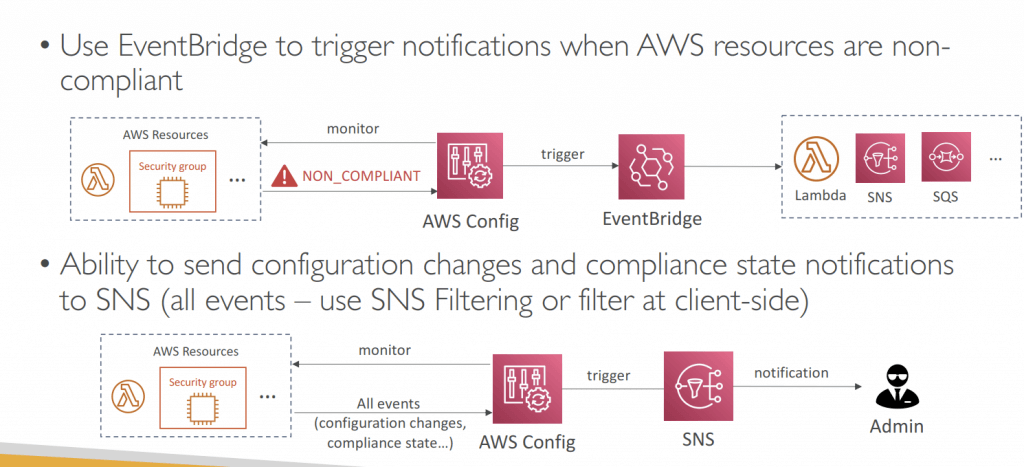
- Use EventBridge to trigger notifications when AWS resources are non-compliant
- Ability to send configuration changes and compliance state notifications to SNS (all events – use SNS Filtering or filter at client-side)
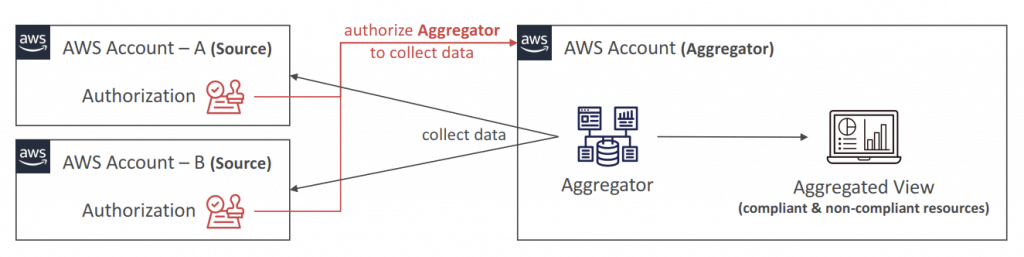
- Aggregators
- The aggregator is created in one central aggregator account
- Aggregates rules, resources, etc… across multiple accounts & regions
- If using AWS Organizations, no need for individual Authorization
- Rules are created in each individual source AWS account
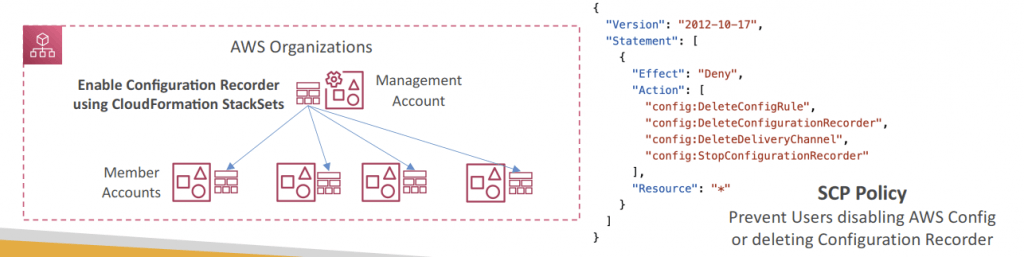
- Can deploy rules to multiple target accounts using CloudFormation StackSets
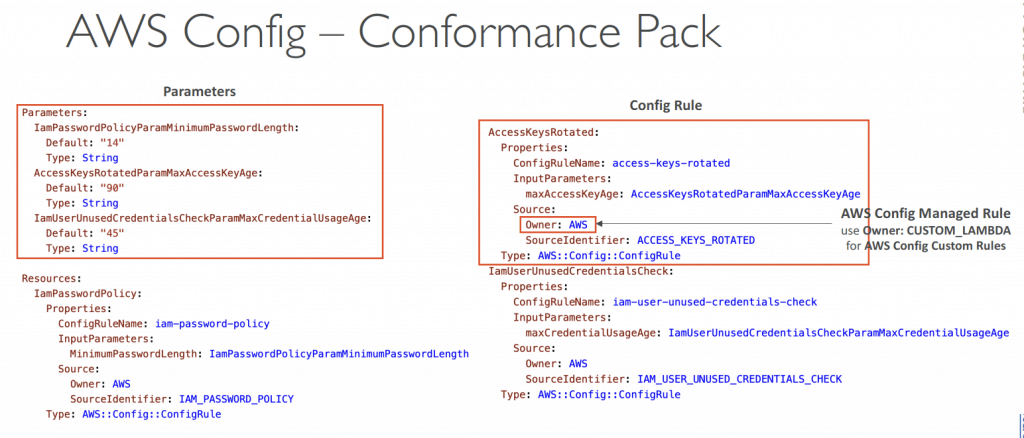
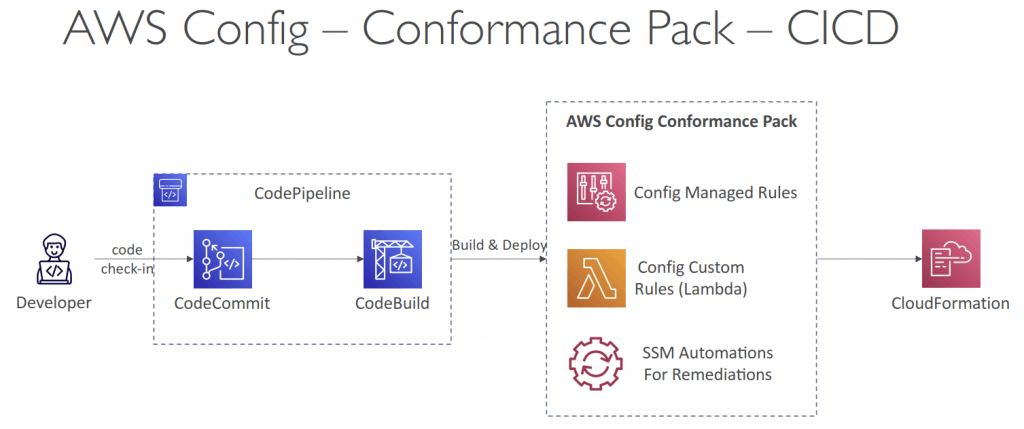
- Conformance Pack
- Collection of AWS Config Rules and Remediation actions
- Packs are created in YAML-formatted files (similar to CloudFormation)
- Deploy to an AWS account and regions or across an AWS Organization
- Pre-built sample Packs or create your own Custom Conformance Packs
- Can include custom Config Rules which are backed by Lambda functions to evaluate whether your resources are compliant with the Config Rules
- Can pass inputs via Parameters section to make it more flexible
- Can designate a Delegated Administrator to deploy Conformance Packs to your AWS Organization (can be Member account)
- Organizational Rules
- manage across all accounts within an AWS Organization
| Organizational Rules | Conformance Packs | |
|---|---|---|
| Scope | AWS Organization | AWS Accounts and AWS Organization |
| Evaluation Type | Evaluate resources against predefined rules that are defined and enforced at Organization level | Evaluate resources against predefined rules that are defined and enforced at the Account level |
| Rules Count | One rule | Many rules at a time |
| Compliance Level | Managed at the Organizational level | Managed at the Account level |
| AWS Config | AWS Trusted Advisor | AWS Inspector | |
|---|---|---|---|
| Purpose | To continuously record and evaluate your AWS resource configurations and the relationships between them. | To provide real-time, actionable recommendations for optimizing your AWS environment across multiple pillars of the AWS Well-Architected Framework. | An automated security assessment service that identifies vulnerabilities, misconfigurations, and unintended network exposure on your workloads. |
| How it works? | It creates a detailed view of your AWS resource configurations, tracks changes, and allows you to create custom rules to assess compliance with your desired settings. | It scans your infrastructure and provides guidance on how to improve your AWS environment based on established best practices. | It continuously scans your applications and EC2 instances to find security flaws, software vulnerabilities, and deviations from AWS security best practices. |
| Key uses | – Tracking resource changes and configuration history. – Ensuring compliance with specific policies (e.g., running only approved AMIs or using encrypted volumes). – Managing resources across multiple accounts and regions. | – Cost Optimization: Identifying underutilized resources to reduce costs. – Performance: Recommending adjustments for better resource utilization. – Security: Alerting you to potential security vulnerabilities and deviations from best practices. – Fault Tolerance & Resilience: Suggesting improvements to your architecture for better availability. – Service Limits: Warning you about potential breaches of service quotas. | – Detecting known vulnerabilities and security issues. – Assessing network accessibility and security posture. – Generating prioritized lists of security findings to help remediate issues. |
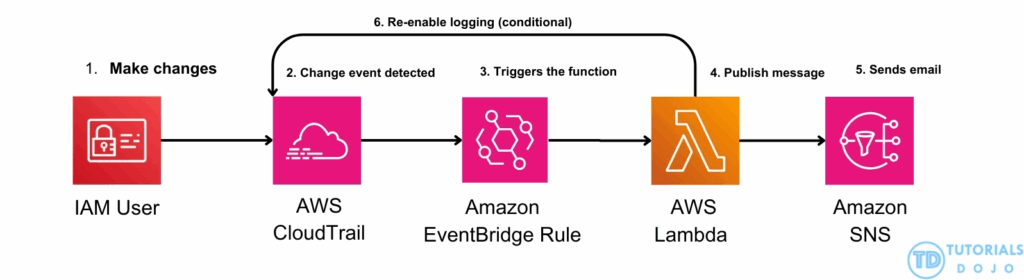
- [ 🧐QUESTION🧐 ] prevent CloudTrail from being disabled on some AWS accounts automatically
- Use the
cloudtrail-enabledAWS Config managed rule with a periodic interval of 1 hour to evaluate whether your AWS account enabled the AWS CloudTrail. Set up an Amazon EventBridge rule for AWS Config rules compliance change. Launch a Lambda function that uses the AWS SDK and add the Amazon Resource Name (ARN) of the Lambda function as the target in the Amazon EventBridge rule. Once aStopLoggingevent is detected, the Lambda function will re-enable the logging for that trail by calling theStartLoggingAPI on the resource ARN. - Configuration changes – AWS Config triggers the evaluation when any resource that matches the rule’s scope changes in configuration. The evaluation runs after AWS Config sends a configuration item change notification.
- Periodic – AWS Config runs evaluations for the rule at a frequency that you choose (for example, every 24 hours)
- the
cloudtrail-enabledAWS Config managed rule is only available for theperiodic triggertype and notConfiguration changes
- Use the
Policy evaluation logic
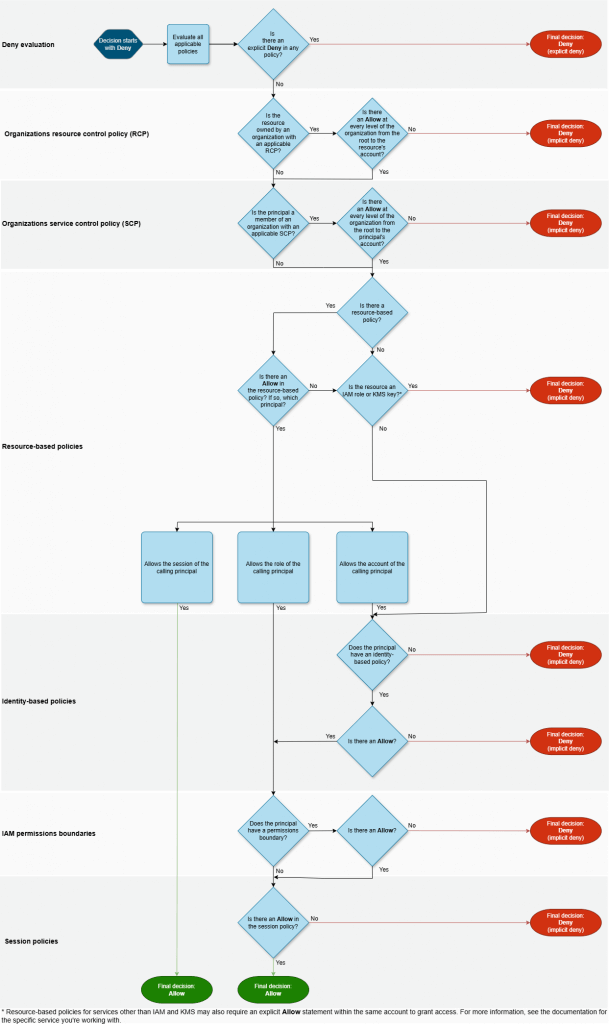
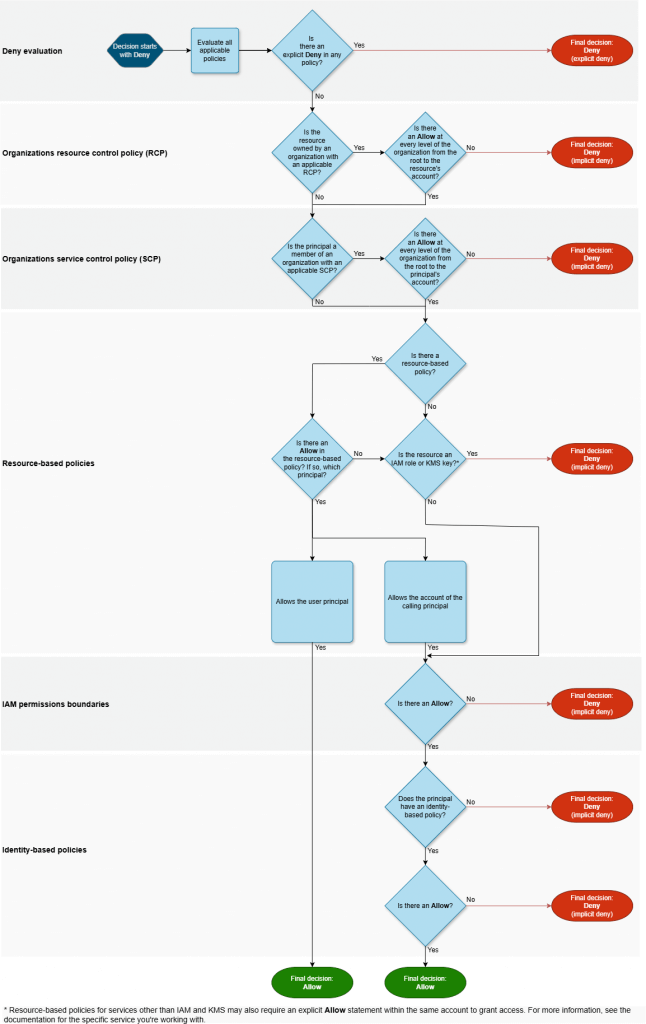
- Authentication – AWS first authenticates the principal that makes the request, if necessary. This step is not necessary for a few services, such as Amazon S3, that allow some requests from anonymous users.
- Processing the request context – AWS processes the information gathered in the request to determine which policies apply to the request.
- How AWS enforcement code logic evaluates requests to allow or deny access – AWS evaluates all of the policy types and the order of the policies affects how they are evaluated. AWS then processes the policies against the request context to determine whether the request is allowed or denied.
- Evaluating identity-based policies with resource-based policies
- Any deny -> overrides the allows
- Allows are union combination
- Evaluating identity-based policies with permissions boundaries
- Any deny -> overrides the allows
- Allows are intersection only
- Evaluating identity-based policies with AWS Organizations SCPs or RCPs
- an account that is a member of an organization and accesses a resource that doesn’t have a resource-based policy configured
- the resulting permissions are the intersection of the user’s policies, service control policies (SCPs), and resource control policy (RCP)
- Any deny -> overrides the allows
- Allows are intersection only
AWS Accounts
- To apply security restrictions across multiple AWS accounts, use Service Control Policy (SCP). For just a single account, use IAM policies.
- You can migrate an account to another AWS organization, e.g. if you divest a business unit
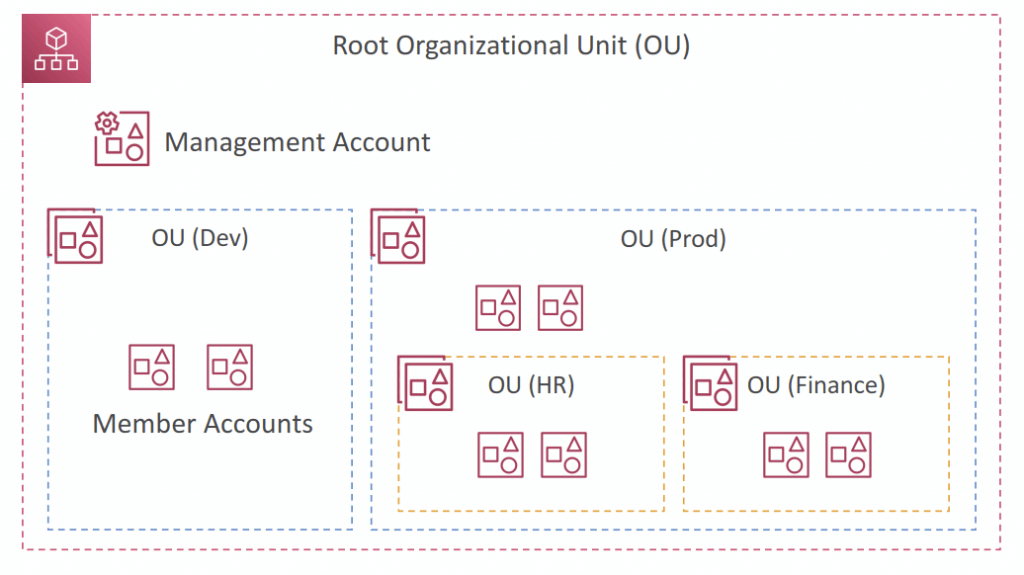
AWS Organizations
- an account management service that enables you to consolidate multiple AWS accounts into an organization that you create and centrally manage. AWS Organizations includes account management and consolidated billing capabilities that enable you to better meet the budgetary, security, and compliance needs of your business.
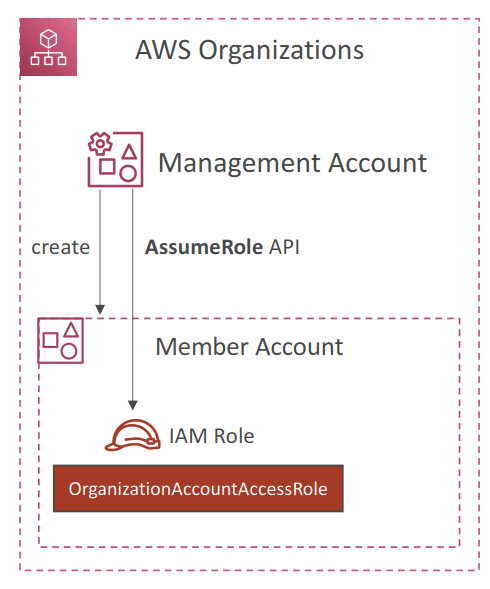
- OrganizationAccountAccessRole
- IAM role which grants full administrator permissions in the Member account to the
Management account - Used to perform admin tasks in the Member accounts (e.g., creating IAM users)
- Could be assumed by IAM users in the Management account
- Automatically added to all new Member accounts created with AWS Organizations
- Must be created manually if you invite an existing Member account
- IAM role which grants full administrator permissions in the Member account to the
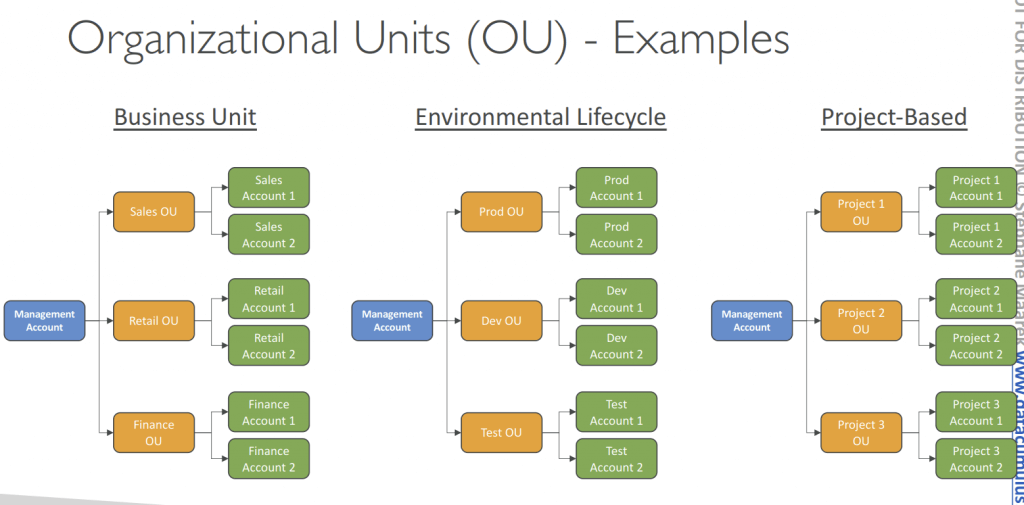
- Multi Account Strategies
- Create accounts per department, per cost center, per dev / test / prod, based on regulatory restrictions (using SCP), for better resource isolation (ex: VPC), to have separate per-account ser vice limits, isolated account for logging,
- Multi Account vs. One Account Multi VPC
- Use tagging standards for billing purposes
- Enable CloudTrail on all accounts, send logs to central S3 account
- Send CloudWatch Logs to central logging account
- Strategy to create an account for security
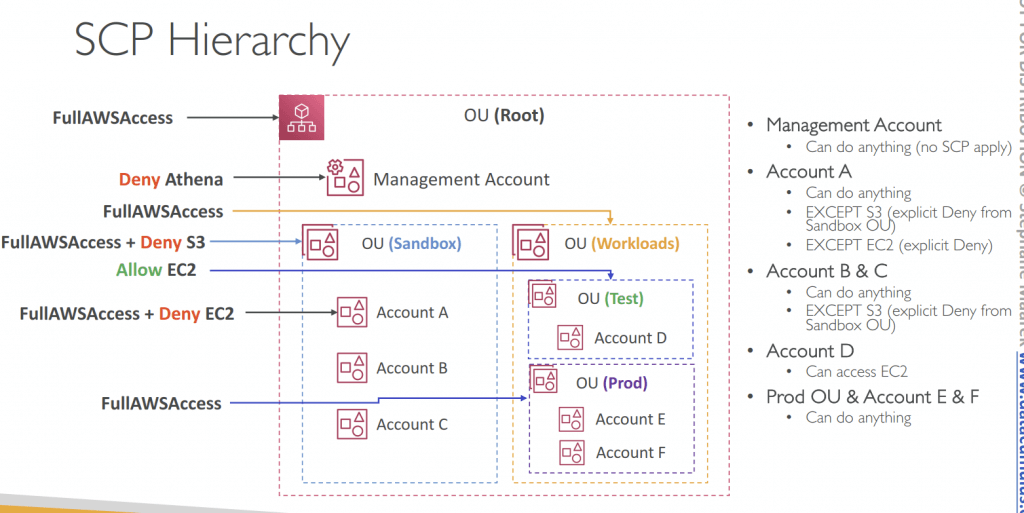
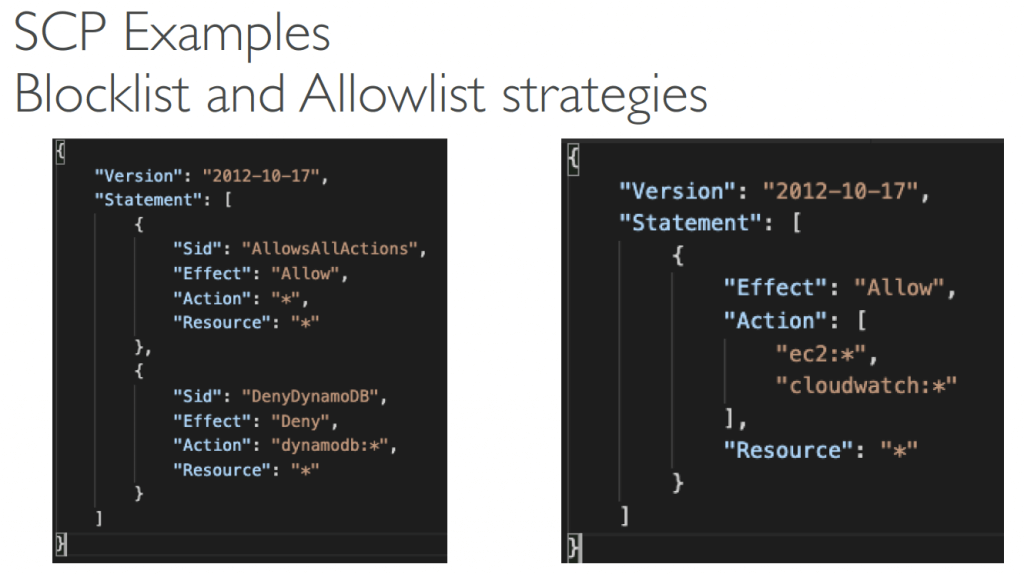
- Service Control Policies (SCPs)
- Define allowlist or blocklist IAM actions
- Applied at the OU or Account level
- Does not apply to the Management Account
- SCP is applied to all the Users and Roles in the account, including Root user
- The SCP does not affect Service-linked roles
- Service-linked roles enable other AWS services to integrate with AWS Organizations
and can’t be restricted by SCPs.
- Service-linked roles enable other AWS services to integrate with AWS Organizations
- SCP must have an explicit Allow from the root through each OU in the direct path to the target account (does not allow anything by default)
- Use cases:
- Restrict access to certain services (for example: can’t use EMR)
- Enforce PCI compliance by explicitly disabling services
- Service control policies (SCPs) are a type of organization policy that you can use to manage permissions in your organization. SCPs offer central control over the maximum available permissions for the IAM users and IAM roles in your organization. SCPs help you to ensure your accounts stay within your organization’s access control guidelines. SCPs are available only in an organization that has all features enabled. SCPs aren’t available if your organization has enabled only the consolidated billing features.
- SCPs do not grant permissions to the IAM users and IAM roles in your organization. No permissions are granted by an SCP. An SCP defines a permission guardrail, or sets limits, on the actions that the IAM users and IAM roles in your organization can perform. To grant permissions, the administrator must attach policies to control access, such as identity-based policies that are attached to IAM users and IAM roles, and resource-based policies that are attached to the resources in your accounts.
- The effective permissions are the logical intersection between what is allowed by the SCP and resource control policies (RCPs) and what is allowed by the identity-based and resource-based policies.
- Feature Modes
- Consolidated billing features:
- Consolidated Billing across all accounts – single payment method
- Pricing benefits from aggregated usage (volume discount for EC2, S3…)
- All Features (Default):
- Includes consolidated billing features, SCP
- Invited accounts must approve enabling all features
- Ability to apply an SCP to prevent member accounts from leaving the org
- Can’t switch back to Consolidated Billing Features only
- Consolidated billing features:
- Reserved Instances
- For billing purposes, the consolidated billing feature of AWS Organizations treats all the accounts in the organization as one account.
- This means that all accounts in the organization can receive the hourly cost benefit of Reserved Instances that are purchased by any other account.
- The payer account (Management account) of an organization can turn off Reserved Instance (RI) discount and Savings Plans discount sharing for any accounts in that organization, including the payer account
- This means that RIs and Savings Plans discounts aren’t shared between any accounts that have sharing turned off.
- To share an RI or Savings Plans discount with an account, both accounts must have sharing turned on
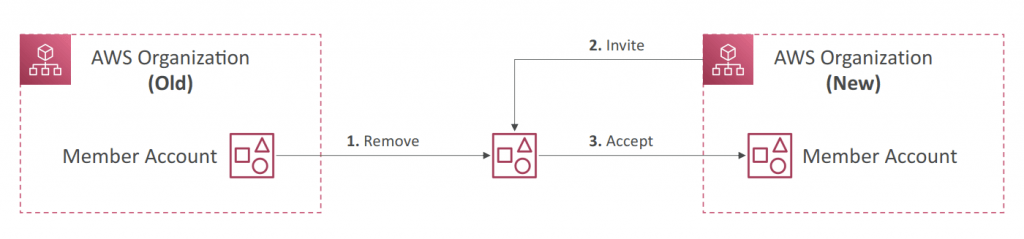
- Moving Accounts
- STEP ONE: Remove the member account from the AWS Organization
- STEP TWO: Send an invite to the member account from the AWS Organization
- STEP THREE: Accept the invite to the new Organization from the member account
- [ 🧐QUESTION🧐 ] monitoring setup that notifies of any changes to the AWS accounts
- AWS Organizations can work with Amazon EventBridge to raise events when administrator-specified actions occur in an organization.
- Multi-account, multi-region data aggregation in AWS Config enables you to aggregate AWS Config data from multiple accounts and regions into a single account.
- An aggregator is a new resource type in AWS Config that collects AWS Config data from multiple source accounts and regions.
- Launch a new trail in Amazon CloudTrail to capture all API calls to your AWS Organizations, including calls from the AWS Organizations console. Also, track all code calls to the AWS Organizations APIs. Integrate Amazon EventBridge and Amazon SNS to raise events when administrator-specified actions occur in an organization and configure it to send a notification.
- Monitor the compliance of your AWS Organizations using AWS Config. Launch a new SNS Topic or Amazon Amazon EventBridge rule to send alerts for any changes.
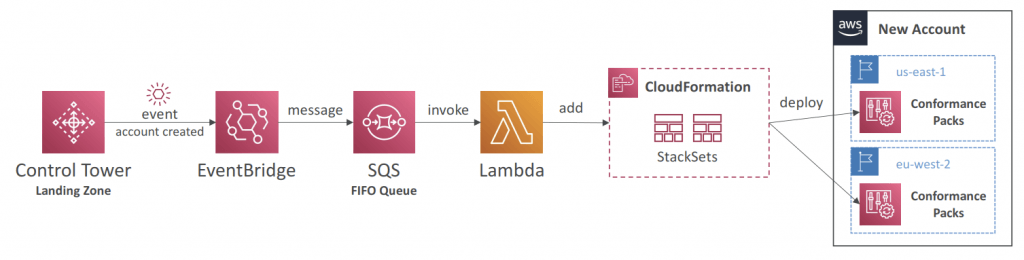
AWS Control Tower
- Easy way to set up and govern a secure and compliant multi-account AWS environment based on best practices
- Benefits:
- Automate the set up of your environment in a few clicks
- Automate ongoing policy management using guardrails
- Detect policy violations and remediate them
- Monitor compliance through an interactive dashboard
- AWS Control Tower runs on top of AWS Organizations:
- It automatically sets up AWS Organizations to organize accounts and implement SCPs (Service Control Policies)
- Account Factory
- Automates account provisioning and deployments
- Enables you to create pre-approved baselines and configuration options for AWS accounts in your organization (e.g., VPC default configuration, subnets, region, …)
- Uses AWS Service Catalog to provision new AWS accounts
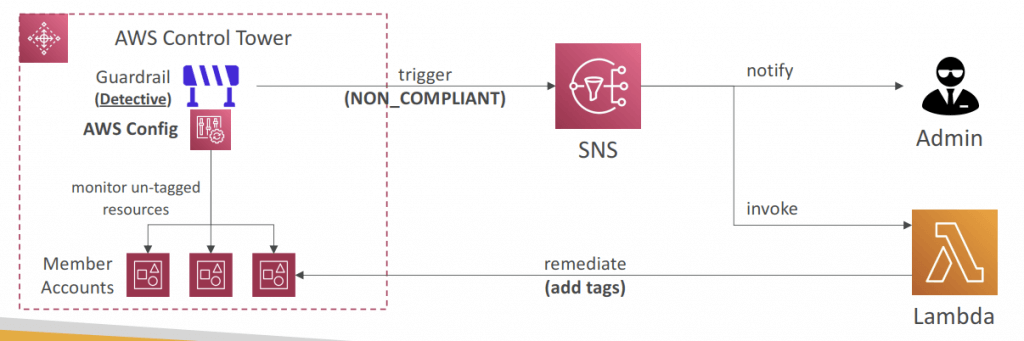
- Guardrail
- Detect and Remediate Policy Violations
- Provides ongoing governance for your Control Tower environment (AWS Accounts)
- Preventive – using SCPs (e.g., Disallow Creation of Access Keys for the Root User)
- Detective – using AWS Config (e.g., Detect Whether MFA for the Root User is Enabled)
- Example: identify non-compliant resources (e.g., untagged resources)
- Guardrails Levels
- Mandatory
- Automatically enabled and enforced by AWS Control Tower
- Example: Disallow public Read access to the Log Archive account
- Strongly Recommended
- Based on AWS best practices (optional)
- Example: Enable encryption for EBS volumes attached to EC2 instances
- Elective
- Commonly used by enterprises (optional)
- Example: Disallow delete actions without MFA in S3 buckets
- Mandatory
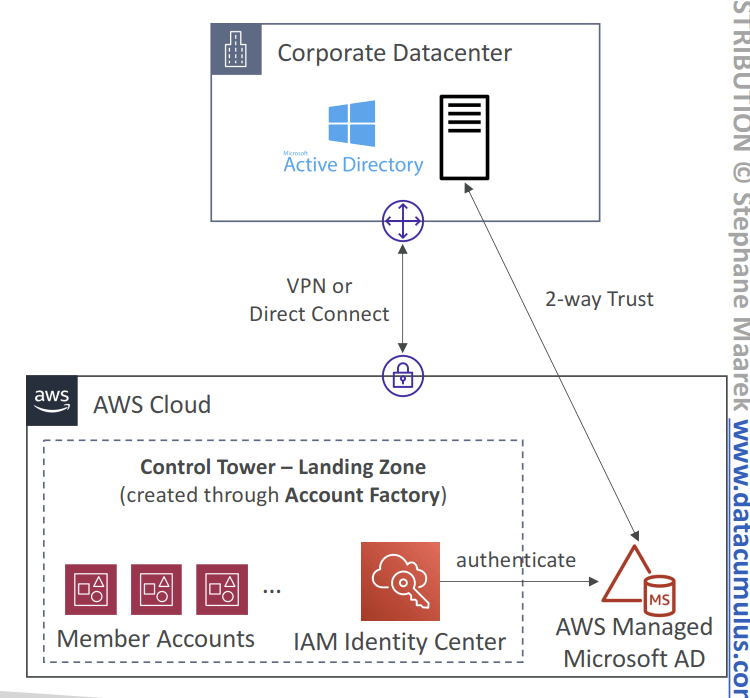
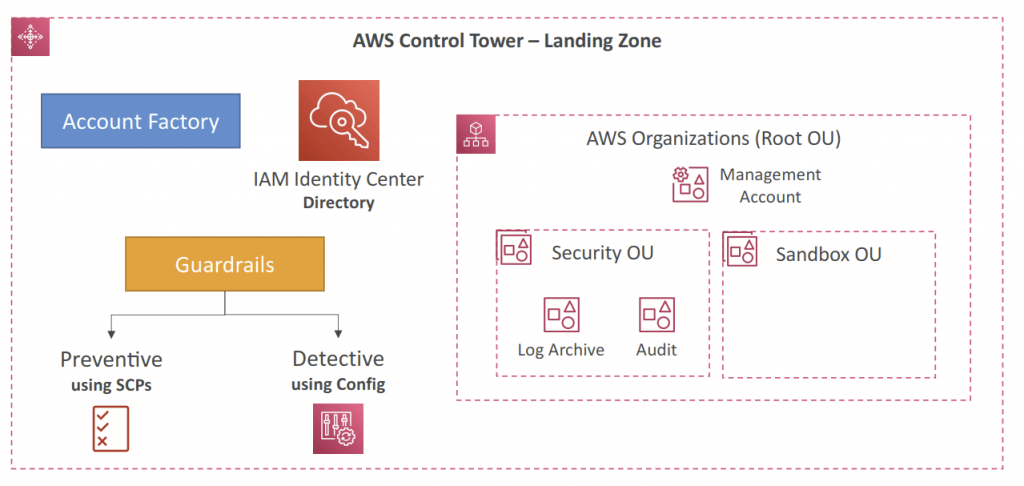
- Landing Zone
- Automatically provisioned, secure, and compliant multi-account environment based on AWS best practices
- Landing Zone consists of:
- AWS Organization – create and manage multi-account structure
- Account Factory – easily configure new accounts to adhere to config. and policies
- Organizational Units (OUs) – group and categorize accounts based on purpose
- Service Control Policies (SCPs) – enforce fine-grained permissions and restrictions
- IAM Identity Center – centrally manage user access to accounts and services
- Guardrails – rules and policies to enforce security, compliance and best practices
- AWS Config – to monitor and assess your resources’ compliance with Guardrails
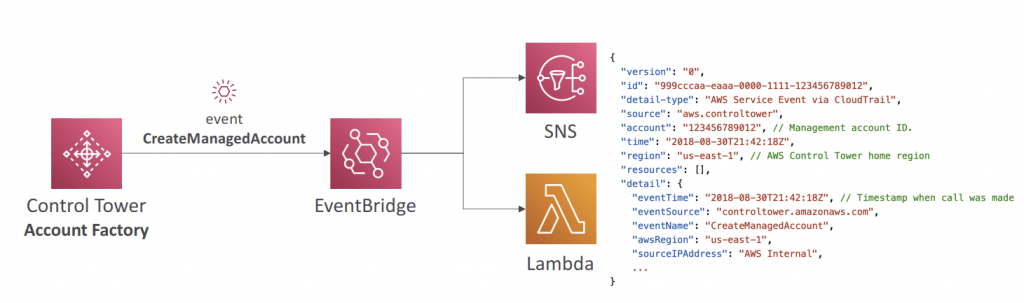
- Account Factory
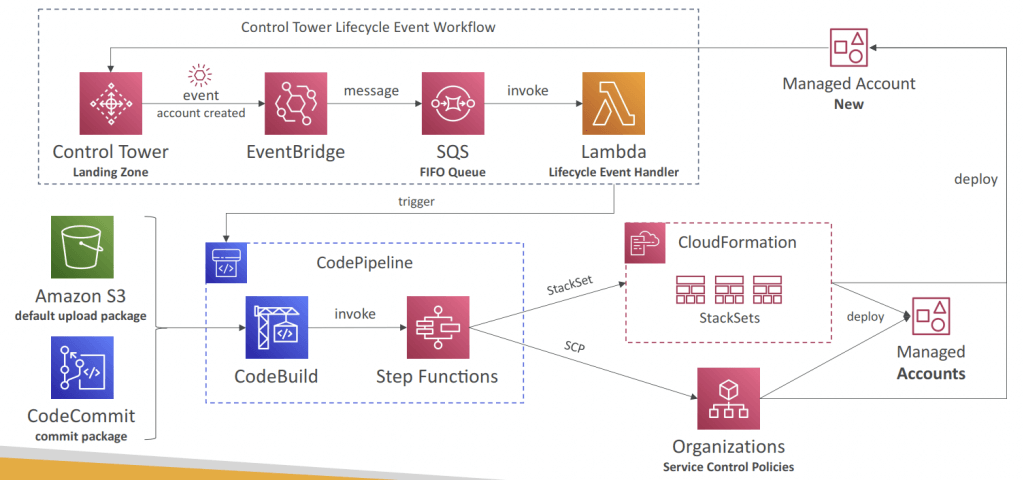
- You can react to new accounts created using EventBridge
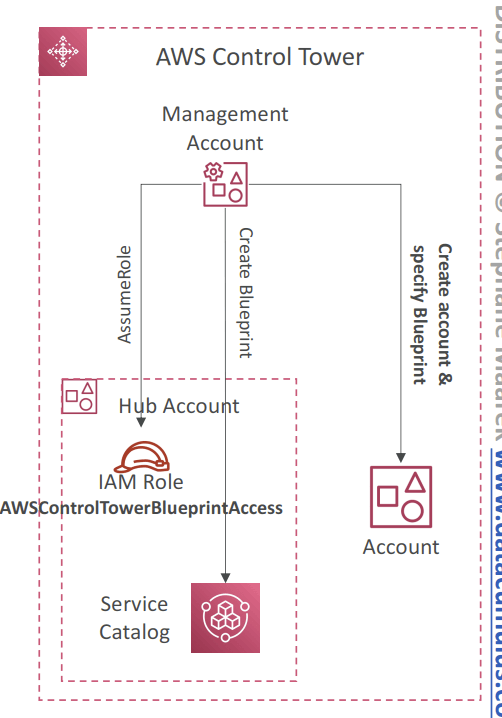
- Account Factory Customization (AFC)
- Automatically customize resources in new and existing accounts created through Account Factory
- Custom Blueprint
- CloudFormation template that defines the resources and configurations you want to customize in the account
- Defined in the form on a Service Catalog Product
- Stored in a Hub Account, which stores all the Custom Blueprints (recommended: don’t use the Management account)
- Also available pre-defined blueprints created by AWS Partners
- Only one blueprint can be deployed to the account
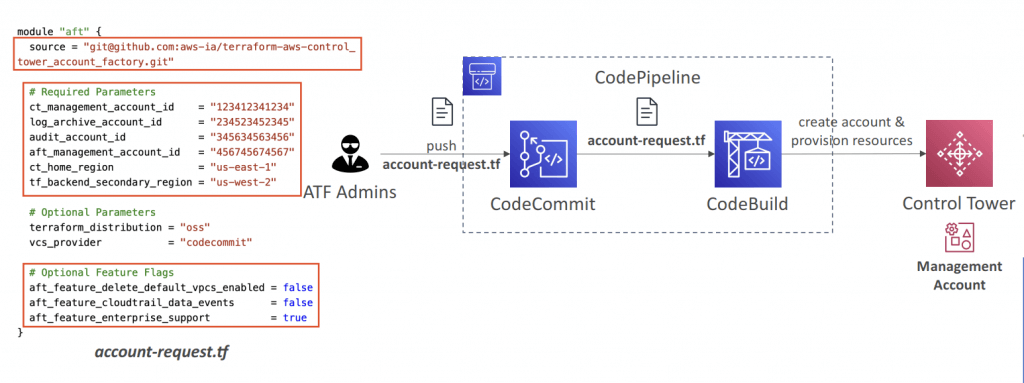
- Account Factor y for Terraform (AFT)
- Helps you provision and customize AWS accounts in Control Tower through Terraform using a deployment pipeline
- You create an account request Terraform file which triggers the AFT workflow for account provisioning
- Offers built-in feature options (disabled by default)
- AWS CloudTrail Data Events – creates a Trail & enables CloudTrail Data Events
- AWS Enterprise Support Plan – turns on the Enterprise Suppor t Plan
- Delete The AWS Default VPC – deletes the default VPCs in all AWS Regions
- Terraform module maintained by AWS
- Works with Terraform Open-source, Terraform Enterprise, and Terraform Cloud
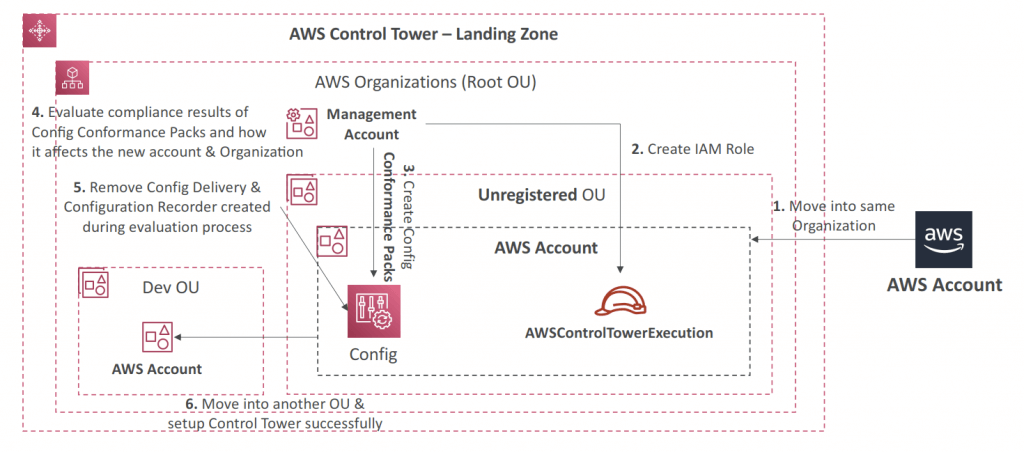
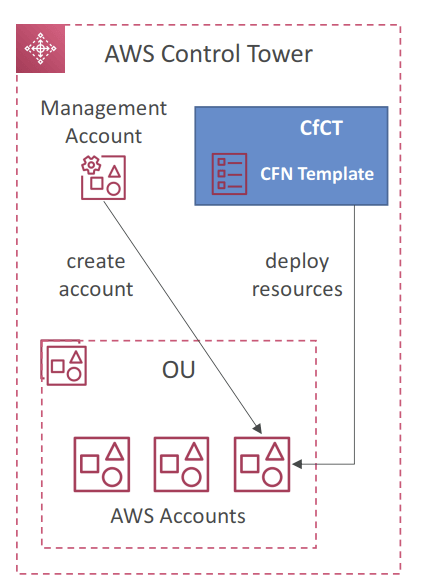
- Customizations for AWS Control Tower (CfCT)
- GitOps-style customization framework created by AWS
- Helps you add customizations to your Landing Zone using your custom CloudFormation templates and SCPs
- Automatically deploy resources to new AWS accounts created using Account Factory
- Note: CfCT is different from AFC (Account Factory Customization ; blueprint)
- AWS Config Integration
- Control Tower uses AWS Config to implement Detective Guardrails
- Control Tower automatically enables AWS Config in enabled Regions
- AWS Config Configuration History and snapshots delivered to S3 bucket in a centralized Log Archive account
- Control Tower uses CloudFormation StackSets to create resources like Config Aggregator, CloudTrail, and centralized logging
- Config Conformance Packs – enables you to create packages of Config Compliance Rules & Remediations for easy deployment at scale
- Deploy to individual AWS accounts or entire and AWS Organization
AWS Trusted Advisor
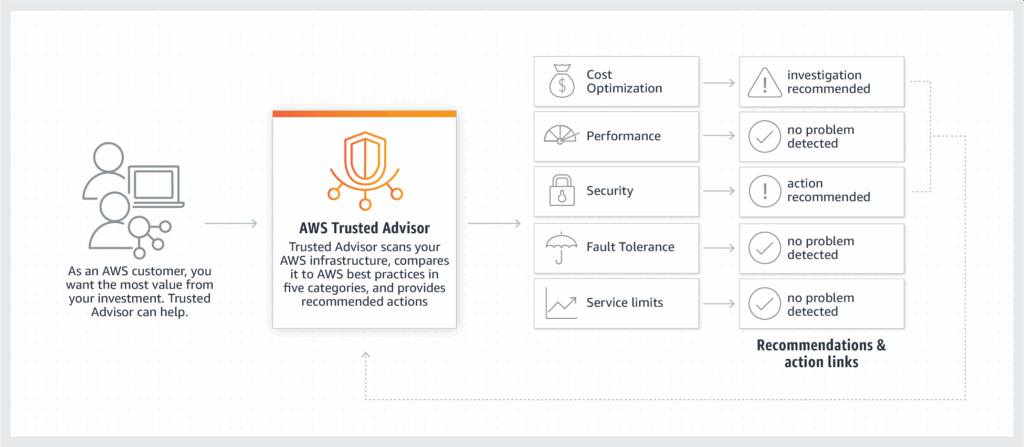
- No need to install anything – high level AWS account assessment
- Analyze your AWS accounts and provides recommendation on 6 categories:
- Cost optimization
- Performance
- Security
- Fault tolerance
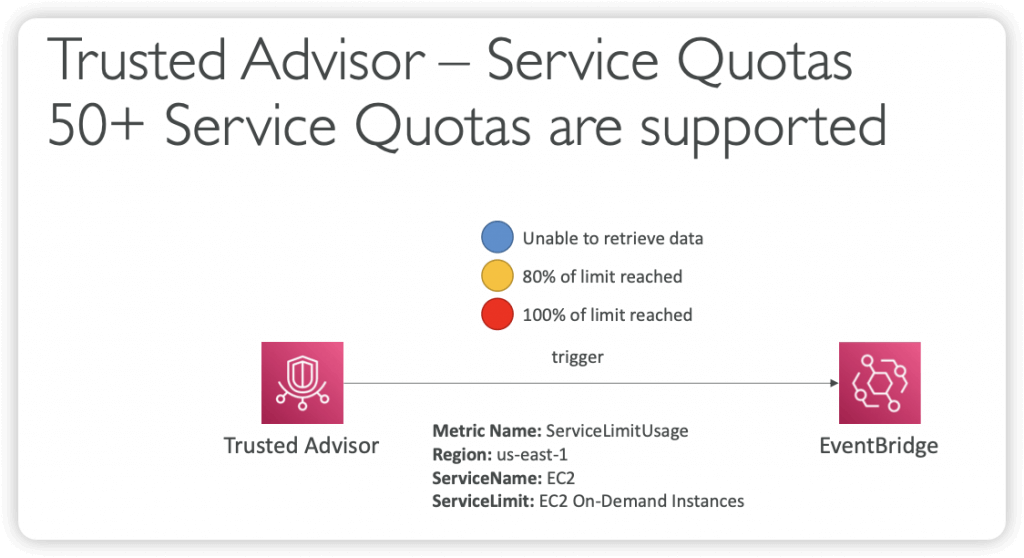
- Service limits
- Operational Excellence
- Business & Enterprise Support plan
- Full Set of Checks
- Programmatic Access using AWS Support API
- “not suitable for configuration management and automatic violation detection”
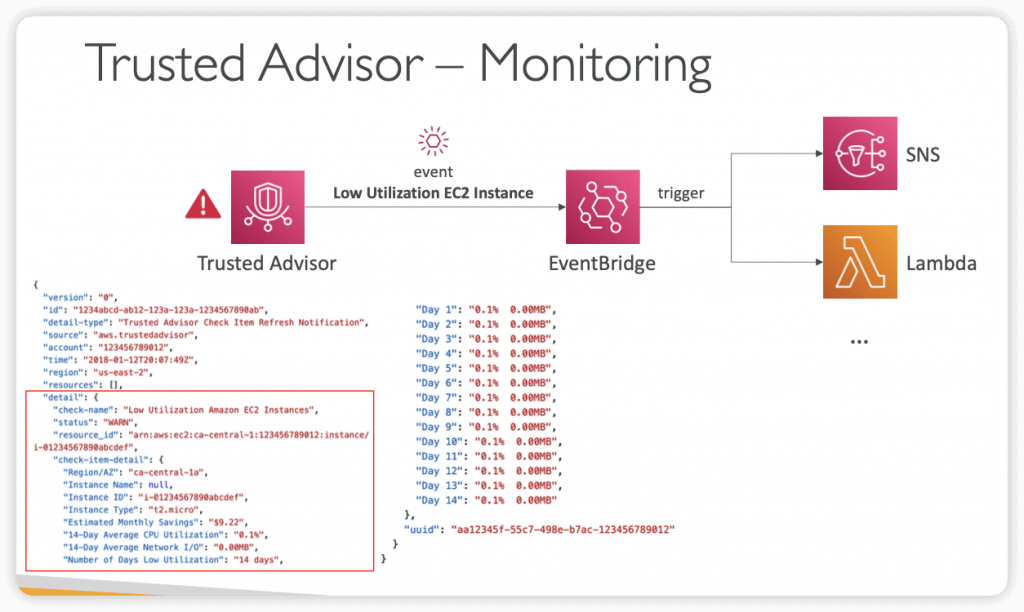
- AWS Trusted Advisor is integrated with the Amazon EventBridge and Amazon CloudWatch services. You can use Amazon EventBridge to detect and react to changes in the status of Trusted Advisor checks and you can use Amazon CloudWatch to create alarms on Trusted Advisor metrics for check status changes, resource status changes, and service limit utilization.
AWS CloudTrail
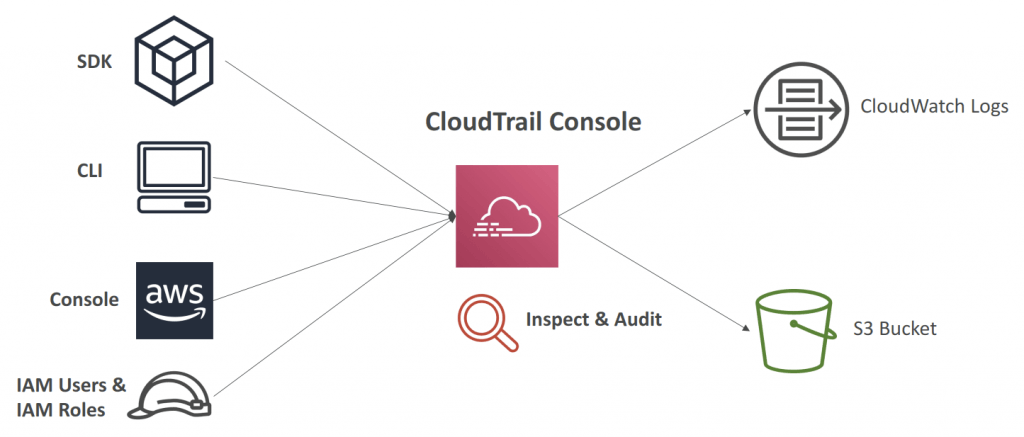
- Audit an history of events / API calls made by users / services / AWS console, under AWS account(s)
- history of events / API calls
- Console
- SDK
- CLI
- AWS services
- useful to find AWS resources changes (when and how)
- history of events / API calls
- CloudTrail is enabled by default!
- export logs to CloudWatch Logs or S3
- A trail can be applied to All Regions (default) or a single Region.
- If a resource is deleted in AWS, investigate CloudTrail first!
- Event Type
- Management Events (default enabled)
- also known as “control plane operations”
- Operations that are performed on resources in your AWS account
- Examples:
- Configuring security (IAM AttachRolePolicy)
- Configuring rules for routing data (Amazon EC2 CreateSubnet)
- Setting up logging (AWS CloudTrail CreateTrail)
- By default, trails are configured to log management events.
- Can separate Read Events (that don’t modify resources) from Write Events (that may modify resources)
- Data Events (default disabled):
- also known as “data plane operations”
- By default, data events are not logged (because high volume operations)
- Amazon S3 object-level activity (ex: GetObject, DeleteObject, PutObject): can separate Read and Write Events
- AWS Lambda function execution activity (the Invoke API)
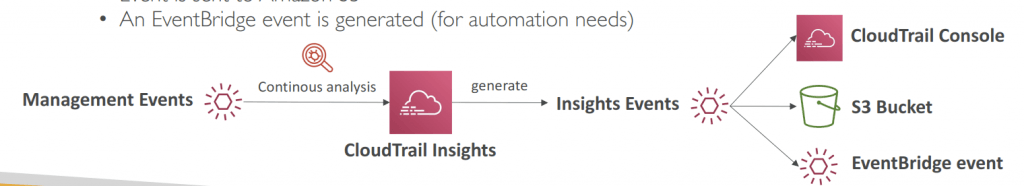
- Insights Events:
- to detect unusual activities (by analyze “Write” events)
- inaccurate resource provisioning
- hitting service limits
- Bursts of AWS IAM actions
- Gaps in periodic maintenance activity
- CloudTrail Insights analyzes normal management events to create a baseline
- And then continuously analyzes write events to detect unusual patterns
- Anomalies appear in the CloudTrail console
- Event is sent to Amazon S3
- An EventBridge event is generated (for automation needs)
- to detect unusual activities (by analyze “Write” events)
- Management Events (default enabled)
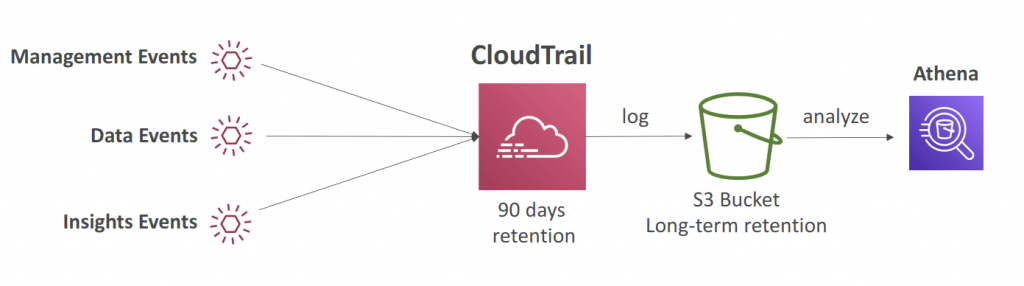
- Event Retention as 90 days. Can be export to S3 and use Athena for further analysis.
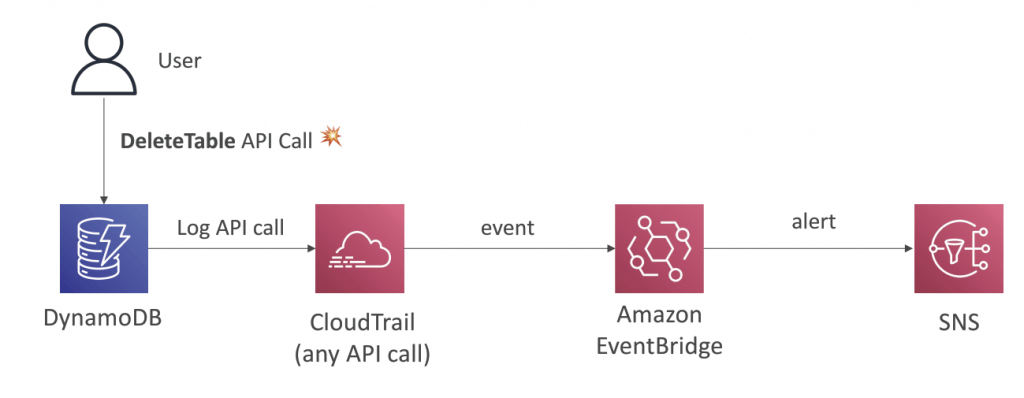
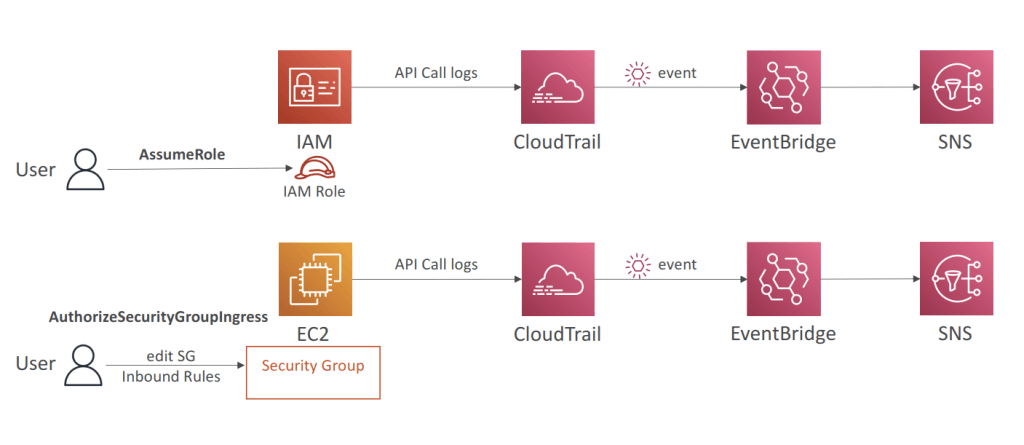
- CloudTrail log file integrity validation
- Validated log files are invaluable in security and forensic investigations.
- When you enable log file integrity validation, CloudTrail creates a hash for every log file that it delivers. Every hour, CloudTrail also creates and delivers a file that references the log files for the last hour and contains a hash of each. This file is called a digest file. CloudTrail signs each digest file using the private key of a public and private key pair. After delivery, you can use the public key to validate the digest file. CloudTrail uses different key pairs for each AWS region.
- The digest files are delivered to the same Amazon S3 bucket associated with your trail as your CloudTrail log files. If your log files are delivered from all regions or from multiple accounts into a single Amazon S3 bucket, CloudTrail will deliver the digest files from those regions and accounts into the same bucket.
- The digest files are put into a folder separate from the log files. This separation of digest files and log files enables you to enforce granular security policies and permits existing log processing solutions to continue to operate without modification. Each digest file also contains the digital signature of the previous digest file if one exists. The signature for the current digest file is in the metadata properties of the digest file Amazon S3 object.
- [ 🧐QUESTION🧐 ] notified of any S3 bucket policy changes
- Create an AWS CloudTrail trail that sends logs to an Amazon CloudWatch log group. Create a CloudWatch Metric Filter on the log group for S3 bucket policy events. Create an Alarm that will notify you whenever this metric threshold is reached.
- A CloudTrail trail is required since it will send its logs to a CloudWatch Log group. To create an alarm, you must first create a metric filter and then configure an alarm based on the filter.
- For notification, you will then create a CloudWatch Alarm for this Metric with a threshold of >=1 and set your email as a notification recipient. Even a single S3 bucket event on the log group will trigger this alarm and should send you a notification.
- S3 Server access logging is primarily used to provide detailed records for the requests that are made to a bucket. Each access log record provides details about a single access request, such as the requester, bucket name, request time, request action, response status, and an error code, if relevant. It is more appropriate to use CloudWatch or CloudTrail to track the S3 bucket policy changes.
- can’t directly send the S3 server access logs to CloudWatch logs. You need to use CloudTrail to send the events to a log group before you can create a metric and alarm for those events.
- can’t simply use an EventBridge rule to filter your log groups directly
- [ 🧐QUESTION🧐 ] to search and review the actions on specific s3 buckets (Get, Put, Delete…) for auditing purposes
- You can log the object-level API operations on your S3 buckets. Before Amazon EventBridge can match these events, you must use AWS CloudTrail to set up a trail configured to receive these events. To log data events for an S3 bucket to AWS CloudTrail and EventBridge, create a trail. A trail captures API calls and related events in your account and delivers the log files to an S3 bucket that you specify. After you create a trail and configure it to capture the log files you want, you need to be able to find the log files and interpret the information they contain.
- Typically, log files appear in your bucket within 15 minutes of the recorded AWS API call or other AWS event. Then you need to create a Lambda function to log data events for your S3 bucket. Finally, you need to create a trigger to run your Lambda function in response to an Amazon S3 data event. You can create this rule on Amazon EventBridge and setting Lambda function as the target. Your logs will show up on the CloudWatch log group, which you can view and search as needed.